During the last 3 months it was more quiet than usual on Hacking Tutorials. In this period less tutorials and articles were publish on Hacking Tutorials but there was a very good reason for that. For the last 3 months I have followed Offensive Security’s Penetration testing with Kali Linux (PWK) course and got certified as OSCP. In this article I will be reviewing the courseware, the labs and the brutal 24 hour exam. We will also look at which prior knowledge would be beneficial during the course and how to get this knowledge. We will conclude this article with some tips and hints that helped me passing the exam.
OSCP courseware and videos
The Penetration testing with Kali Linux courseware contains a PDF file and instruction videos on all subjects. The course covers many different subjects such as passive and active information gathering with many different tools but also writing simple buffer overflows exploits for Windows and Linux and privilege escalation techniques for both operating system. You will also learn about exploiting web applications, perform password attacks, tunnelling and how to use Metasploit. The full course syllabus is available here:
https://www.offensive-security.com/documentation/penetration-testing-with-kali.pdf
It is helpful if you have prior knowledge of networking basics, scripting/coding and maybe some hacking and enumeration techniques in general when you start the course. Every subject is explained very well in the courseware and starts from basic. However, you really need to learn a lot during this course in a very limited timeframe. Especially when you do this course beside a full time job like most of us. Any prior knowledge will speed up the learning, lower the learning curve and save you some time.
Tips for the OSCP courseware
- Follow the courseware first and then start practicing in the labs.
- Use additional sources to learn more. A list of great online and offline sources is at the bottom of this article.
- Join the offensive security PWK forums and social media and talk to other people. You can learn a lot from other people too, especially when you have little or no practical experience on the subject. InfoSec is often a passion and a way of living so people are often quite nice and willing to share information and educate people who share the same passion (read last paragraph for what questions to ask and what not).
OSCP Labs
The best part of the learning path to OSCP certification are the labs. The OSCP labs contain several networks with over 50 servers to practice your ethical hacking skills on. The operating systems on these hosts vary from Windows XP, Windows 2008 server and Windows 7 to different Linux/Unix based operating systems such as Debian, Ubuntu, CentOS, FreeBSD, Fedora and more. Some operating systems are old (there’s even a Windows 2000 server) and some are very recent like Windows 8.1 The lab also contains several clients performing automated tasks which can be targeted to learn about client side exploitation.
Proof.txt files
The main goal for each machine is to get a shell on the machine with administrator privileges and collect the contents of a proof.txt file on the Desktop. Some machines contain a networksecret.txt file besides the proof file. These machines are configured with a second network adapter which allows you to use the machine as a pivot point and access an otherwise unavailable network. The contents of the network secret files allows you to revert machines in other subnets from the student panel. The OSCP student panel is accessible through the VPN connection and is an interface to revert machines, use Offensive Security’s Crackpot and to (re)schedule your exam.
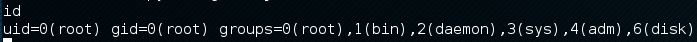
Vulnerable machines
Every host on the lab contains one or more known vulnerabilities, varying from local file inclusions (LFI), backdoors and SQL injection to remote buffer overflows, default passwords and remote file inclusions (RFI). Privilege escalation is often performed through exploiting OS and application level vulnerabilities but also trough misconfigurations such as incorrect user privileges on files and services. After proper enumeration and assessing the vulnerabilities you have to exploit them in order to get a limited user shell, sometimes directly a root shell or information which will lead to any of these. The vulnerabilities together have been setup very well and often you need to exploit a clever a combination of them to get root or administrator access. I must say that Offensive Security has done a great job on setting up these labs.
Metasploit and automated tools
The use of Metasploit is limited during the OSCP examination, although it is advised to get familiar with Metasploit and practice using it on the lab machines. You are allowed to use it on one machine during the exam which is often considered as a lifeline by many people. Personally I’ve often used both ways to exploit vulnerabilities, first manually and then with Metasploit if an exploit module was available. Using automated (commercial) vulnerability scanners, such as Open-VAS, is strictly forbidden on the exam. Using them in the labs would be wasting your learning experience when it comes to enumeration and vulnerability assessment as this part of the penetration test is automated.
Tips for the OSCP labs
- The student forums contain a walkthrough written by Offensive Security for machine 71. Follow it to get a clear picture of how to conduct a penetration test from enumeration to privilege escalation and post exploitation.
- Learn about the methodology used in the walkthrough, the techniques are less important.
- When you’re advancing through the labs, write a simple bash or python script to perform (a part of) the enumeration. This will improve your scripting skills and experience but also save time.
- Try to root as many machines as possible because all boxes contribute to your experience and learning process.
- Extend your lab time if necessary and possible when you have left a lot of boxes untouched at the end.
- You can install your own vulnerable machines for practising or download them elsewhere.
OSCP exam
After going through the courseware and finishing the bigger part of the labs, you might be ready for the horrific 24 hours OSCP certification exam. At the scheduled exam date you will receive new VPN credentials to access the exam network. The exam network consists of 5 machines with a number of points ranging from 10 – 25 in the networks I got. You will need a total of 70 points to pass the exam. Personally I have taken 2 attempts to pass the examination and obtain the OSCP certification.
The most important factors to consider prior to the exam are:
- Time management
- Avoiding rabbit holes
- Make a battle plan which you will stick to during the full length of the exam
OSCP Exam #1
On the first attempt I started at 11 AM and did not have a solid plan and just ran into the exam. In the first 2 hours I managed to get root on the first box. In the 6 hours to follow I rooted the second box. From that moment on everything went downwards and I got lost for hours in what later seemed to be a rabbit hole. At that moment it was impossible to get out of it, also because the tiredness kicked in after 16 hours making it hard to remain focused. I stopped at 3 AM and slept till 08:00.
I got back to the exam at 08:30 and only had 2 hours and 45 minutes left. In that period I got a limited shell on the box I was stuck at the night before and almost rooted a second one but it was too late. The VPN died and I knew I had failed the exam. I have learned a lot from this first failed attempt. I have learned how important time management is and that you really need a strategy to avoid rabbit holes and lose too much time. At the end of this article I will present you with a list of points to consider which really helped me to avoid rabbit holes. I found that avoiding rabbit holes is key in passing the exam on the second attempt.
OSCP Exam #2
The second attempt I’ve started the exam at 3 PM and planned to work till 3 AM and then sleep till early morning. This way I had 2 ‘fresh’ starts for the exam to utilize more productive hours. From the first attempt I knew that exam hours 12 to 16 are worthless. Personally I become too tired and lose too much focus after 12 hours. I also started with the harder exam machines this time. Those are the ones that give 20 or 25 points. In the first 12 hours of the exam of the I managed to get 55 points. I went to sleep at about 5 AM and woke up to continue the exam at 8 AM.
In the hours to follow I managed to get another 40 points. I had a total of 90 points and I knew I had passed the exam. For one box I did not manage to escalate my privilege level to root, but I was fine with that.
OSCP exam report
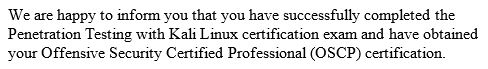
In the next 24 hours you will be writing a penetration test exam report. The exam manual, which you get at the start of the exam, explains clearly what is required in the report. Make sure you collect this information during the exam in the required format. Prior experience with report writing (lab report for example) will help you a lot at this point. After submitting the lab report I got the following e-mail about 2 days later from Offensive security:
Tips before the OSCP exam
The following tips will help you before the OSCP exam:
- Make a battle plan before the exam which at least contains the following:
- Breaks with time, including dinner, lunch and breakfast.
- Determine when and for how long you will sleep. Yes, you need to sleep in 24 hours.
- How long to work on a single box. Personally I suggest to switch to another box when you are stuck on a box for more than 2 hours.
- Which enumeration to perform on every step of the penetration test (at the start and on a low privileged shell).
- Finish your lab report for 5 extra points and optionally the course exercises for an additional 5 points. You might need them to reach the 70 points.
- Rest before the exam, at least a day is what I would recommend. A fresh and sharp brain at the start of the exam is more important than a few more details covered.
- You need to write a penetration test report after the exam. Make sure you know how to write it so you know what information to collect during the exam. The lab report is a great practice for this, use it to learn how to document properly.

Tips during the OSCP exam
The following tip are helpful during the OSCP exam:
- Personally I would suggest to not work longer than 12 hours on the exam without sleep or at least a longer period of rest to cool down your brains. Pick a timeframe for the exam which supports this and give you 2 fresh starts with enough time.
- Take frequent breaks during the exam.
- Recognize rabbit holes! PWK/OSCP is not an advanced penetration testing course and 24 hours is not enough time to write a custom privilege escalation exploit from scratch. Nor can you perform advanced blind SQL injection attacks which aren’t documented anywhere in such a short timeframe. Summarized: When it is too difficult, it is probably a rabbit hole.
- Use the last 15-30 minutes of the exam to check if you collected all required information before your VPN connection dies. It is easy to miss important information in the state of mind you will be in after 24 exam hours. Note: the VPN connection dies after 23 hours and 45 minutes! Schedule this check on time!
Conclusion and resources
I want to finished this article with saying that Offensive Security did a great job on this course. It is a very challenging course and the hard exam really gives value to this certificate. Many people say that PWK/OSCP is not an entry course and question themselves (and others) when to engage OSCP. Personally I think these people are just partly right, PWK is not entry level but it’s not advanced either. More important is the time you can spend on the course. If you are able to consume a lot of information in a short period of time and your devotion (try harder!). It is always a good thing to prepare yourself for a course like this. I would like to recommend the following books, tutorials and resources:
The Virtual Hacking Labs – Online Penetration Testing Lab
Practice on vulnerable machine in the online Penetration Testing Labs: The Virtual Hacking Labs
General penetration testing
Penetration Testing: A Hands-On Introduction to Hacking by Georgia Weidman
Web application hacking
The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws by Dafydd Stuttard and Marcus Pinto.
Exploiting
Hacking: The Art of Exploitation, 2nd Edition by John Erickson
Any or all of these hacking tutorials:
- Metasploitable 2 enumeration
- Metasploitable 2 vulnerability assessment
- Exploiting VSFTPD v2.3.4 on Metasploitable 2
- Hacking Unreal IRCd 3.2.8.1 on Metasploitable 2
- Hacking dRuby RMI Server 1.8
- Buffer overflow explained: The basics
- Hacking with Netcat part 2: Bind and reverse shells
- Mingw-w64: How to compile Windows exploits on Kali Linux
Links
The following links are very helpful during the PWK course:
More links and books will be added over time.
Help during the OSCP course
Earlier in this OSCP course review I mentioned that it is a good thing to ask other people to help. Especially when you’re stuck on something or when you cannot find the information that you need. I’d be happy to help you answer your questions or give advice and such. But don’t contact me and ask for the PWK courseware, for help during the exam or anything else that will ruin your or anyone else’s learning experience. For simple questions please use the comment functionality below the article so anyone can benefit from the response given. Also note that Offensive Security admins are available on the IRC channel to help you when you get stuck (and sometimes give you a hint instead of try harder).


115 Comments
Great review! Would you be able to expand a little on the manual exploitation and point me to any resources (links, books, videos) on that subject. I understand from reading tons of reviews including yours that Metasploit is mostly not allowed on exams, and to be honest I’d prefer to learn how to manually exploit machines anyways, but I cannot find any material on how to specifically manually exploit machines. Every search brings me back to some resource using meterpreter for exploitation. I even found a link on Reddit asking the same and there was not really anything helpful there. All I’ve found is that you need some kind of ‘handler’ (such as meterpreter) to deliver your exploit, but I’ve found nothing substantive about the manual exploitation process or what other tools to use to facilitate it. Thanks for any help you can provide.
Hi Joey,
Thanks!
I suggest you follow these two tutorials to learn about manually exploiting vulnerabilities. The manual part refers to performing vulnerability assessments and locating, modifying and testing exploits and payloads. The following tutorials show you how to do both ways:
http://www.hackingtutorials.org/metasploit-tutorials/exploiting-vsftpd-metasploitable/
http://www.hackingtutorials.org/metasploit-tutorials/hacking-unreal-ircd-3-2-8-1/
Good luck! And don’t hesitate to ask questions.
Congrats on achieving your OSCP! You tried harder!
Thank you!
Congrats! Just curious do you have an email by any chance?
Thank you! Please use the contact form to contact us.
Thanks for the links! I’m reading one of the recommended PDFs… Nice! Thanks for sharing. Keep up the amazing work!
Thanks! Glad you like it!
Dear first of all congratulations on obtaining OSCP certifications.
Secondly, it was one of the most detailed reviews, it was a good read.
Thank you and have a good day.
Thank you! Have a good day yourself too!
I went through the path of OSCP myself. The author couldnt be more spot on. All the details provided above will help you if you are thinking about taking OSCP.
Great analysis and review thank you
Thanks and congrats on passing OSCP too!
Great review! Congratulations the OSCP certification. You made up your mind to do it and you did not give up until you completed it.
This is the direction I plan on going in my career. This review provided me with the confidence that this is an achievable goal. Great information loaded with wisdom from hands on experience. You’ve written an analytical review that can be trusted.
Thank you!
Thank you! Your comment is very appreciated!
Great Review – thank you!
Congratulations on passing the exam.
I have enjoyed your review. I find it to be very balanced in terms of what to expect from the learning process. I have read a few OSCP reviews and have enjoyed this one the most. Before I read this review, I was planning to attempt OSCP in 2 years’ time. I think that I might attempt it sooner.
I also appreciate the fact that you’ve included a few extra resources. I am sure that these will come in handy during and before the course. I will definitely come back to ask more questions in the future – I promise that it won’t be anything that will minimize the learning experience. :-)
Thank you very much!
Im currently taking the oscp and this is pretty much what to expect. You’ll find yourself pretty frustrated from time to time but if your willing to Try Harder one should pass. This is a difficult course compared to other information security certifications.
Thanks!
A very good review and quite motivating. I have already learned a lot in the past 2-3 weeks something which I never learned in 1-2 years. I have basic pen testing experience and wanted to go for an advanced course which, OSCP checks all the boxes. My course is about to start in a 2-3 weeks and am trying to learn as much as I can and can only learn the course specific stuff when I get my course-ware in my hands. Done with Buffer Overflow, did some VMs from Vulnhub, however I read somewhere about compiling exploits for Windows and Linux. Can you recommend some good resources for such exploits especially Windows? Also how easy/difficult are the Web Application side attacks?
Thank you!
Exploit (cross)compilation is covered in the courseware and is pretty easy and basic throughout the course. The labs offer are lot of scenario’s to practice this. Regarding your question about the web application; all vulnerabilities are easy when you know how to exploit them. You’ll probably spend a lot of time on some and only a little time on others.
Personally if would recommend you the Web application hacking handbook for web application hacking as mentioned in the review. Also I would focus on privilege escalation techniques, including enumeration, for Linux and Windows as this is not extensively covered in the courseware.
Good luck on OSCP! You can always contact me here or on Twitter if you have questions.
Wooo what a great review! Thanks for this. I was looking around for OSCP reviews, the fact is i am a computer security enthousiast, but currently working in developing Java/JEE web application, and aims at switching on computer security, my first love. I certainly do not have your experience and knowledge guys, so after reading some reviews, and yours, specially your “Many people say that PWK/OSCP is not an entry course”, i’m now asking your point of view. Is there another more accessible course, for ex vulnhub.com to start to root VM, or the books you mentionned (already have the art of exploitation), metasploitable may be, or more lab access time will do the trick ( 4, 5, or 6 months)… . Think it’s going to be a huge challenge!!!!
Thanks again for your feedback and congrats for your OSCP ;)!
Hi! Thanks for the compliments!
Personally I think that most important is to spend enough time on the labs and find a methodology that works for you. I also think that OSCP is not an entry course but it’s not a very advanced or expert course either. The course covers a wide range of subjects and techniques, but it is like 1000 foot wide but only 10 foot deep. In the labs you need to learn how to find and exploit vulnerabilities in an effective and efficient way in order to pass the exam within the 24h time limit. From this perspective I wrote the tips and tricks for the courseware, labs and exam and when applying them I am sure you will pass OSCP as well :)
If you have more questions, do not hesitate to contact me here or on Twitter.
Thanks for your reply full of motivation ;) !!!
Good advice! Thank you. :)
Do you have any recommended links for working with existing exploits from exploit-db? I followed the courseware for the section on fuzzing, but they just kind of dump you onto an example written in C that I was not ready for.
Hi!
Check out the following tutorials:
http://www.hackingtutorials.org/metasploit-tutorials/hacking-unreal-ircd-3-2-8-1/
http://www.hackingtutorials.org/metasploit-tutorials/exploiting-vsftpd-metasploitable/
Also read the comments on the exploit-db exploits. They often tell you how to compile or use them.
Hi, Great review, thanks for the tips. My query is did you complete the entire course video and material before you try it on the lab? or you proceeded parallelly with lab and course material?
Hi! Thanks for the compliment!
I did complete most of the video courseware before starting the labs. For some exercises you need lab access, for buffer overflow for example, but for most you don’t. Are you planning to sign up for the course?
Hi,
My lab will start from Sunday.
great, good luck and more important: have fun!
Contact me if you need help with anything :)
Sure, Thanks!
My first attempt im fail ! my second chance is in January/17 !
Too bad, but many fail on the first attempt (including me). Just review where it went wrong and take a look at the tips here.
Good luck in January and let us know how it went!
Have you prepared some well-working manual built exploits before exam? Or you picked them up during exam?
Hi Alex,
No I didn’t prepare exploits before the exam, I compiled them when I needed them. It is never a bad idea to prepare some exploits though.
I’m a little confused on the exam portion. So if I’m not an expert at buffer overflows, but understand the needed registers for a buffer overflow such as EIP, ESP JMP for exploits am I good to go? Or should I be ready to write a buffer overflow from scratch?
IE; As of right now I’ve just taken PoCs and the needed registers from Metasploit modules.
I can’t say too much about the buffer overflow portion on the exam other than that the courseware provides enough information to successfully exploit it. Just study the courseware and use it during the exam.
Have you planned an exam date already?
I’ve signed up for the course and haven’t planned an exam date. I still have a month or so left in the labs, I might schedule the exam soon so I don’t have a gap in between my lab time and my studies.
At first I was afraid to trigger anything in the labs and being really cautious. Now I’m just going head on taking down machines, while honing my skills and understanding my weaknesses. At this point it’s more of a game to me, my 60 hours of Counter Strike every two weeks have turned to 0 lol.
Congrats on your certification.
Thank you.
I think it is time well spend in the labs instead of playing games lol :)
Good luck and if you need help with anything, just let me know.
Hi, congrats on passing.
Great review, I am happy that I found this blog.
Could you please answer me this two questions:
1. Do you think the person that comes from .Net programming and recently acquired CompTia Linux+ with very general knowledge of networks but nothing about windows admin is a good enough to start this course?
2. You buying 30 days access to labs and course materials, but can you extend additional access and schedule exam after 2-3 months?
Thanks for the answers.
Hi, Thanks for the compliments, very much appreciated!
Regarding your questions:
1. I think if you have a programming background, you won’t have much trouble with reading and customizing exploits which you’ll be doing a lot during the course. If you have a network/system engineering background, you won’t have much trouble with understand pivoting techniques and privilege escalation etc. etc. As mentioned in the review, OSCP is 1000 feet wide and only 10 foot deep, so I think you will be okay. You cannot be an expert in every field so you will (need to) learn a lot of new stuff during the course. CompTia Linux+ will also help you with basic understanding of the Linux OS which will help you during the course.
2. You can buy 30 day lab access and extend as many times as necessary. Unless you buy new lab access, you will need to schedule you exam within 3 months after the last labtime ended. Please note that lab extension does include a new exam attempt. So you can attempt the exam after 30 days and renew lab time with a new exam attempt if you fail.
When will you start the course?
Thanks for a fast reply.
I think after a new year, as Xmas time is usually very busy for me…
Hello there,
II will take the course next Saturday (60 days). If I extend the lab before the 60 days, would that mean that I have 2 exam attempts?
Hello!
Yes, good point! Lab extensions include an exam attempt so it would be wise to attempt the exam after 60 days and extend if you failed.
Hi, Sorry I do not speak english , I don’t understand that is ‘rabbit hole’, Please can you explain the concept.
Thank you
Hi! Good question.
A rabbit hole in OSCP context is when you think you have a solution to root a certain box or get a limited shell, but after a while (often many hours later) you realize you were wrong and something else was vulnerable. In this case you went down the rabbit hole. This often happens when you’re not performing a full vulnerability assessment on a box and try to exploit every vulnerability you find on the way (many rabbit holes among them). As you probably know, during the exam you don’t have time to lose on rabbit holes. This is why it is important to come up with a strategy to avoid them.
With a full vulnerability assessment you are able to make a list of vulnerabilities and start to exploit the ones which you think have the highest success rate. For example: you have found a CMS with a blind SQL injection vulnerability with no proof of concept code on exploit-db and a local file inclusion (LFI) vulnerability on another web application. Personally I would go for the web application with LFI instead of the blind SQL injection vulnerability. If you are aware of both and choose for the LFI, you probably avoided a rabbit hole.
Hi, I am understand, thank you so much! Is very cool your webpage! :D
Wow! This is by far the best OSCP cert & prep review! Thanks for taking your time to share this valuable guide! I plan to sign up the course next week.
Few questions:
1) To enumerate vulns on a box, can you use Nessus or nmap vuln enum script? Your method to find all vulns in the box?
2) When you say full vulnerability assessment, do you refer to scanning the box for all ports to find the vulns, or looking on banners of all services manually? Came you elaborate?
3) If a box has multiple vulns, do you go by the one with exploit-db available? Or your method to select the one with high success rate?
4) During the test, can you use all the available kali tools to enumerate and carry out exploit?
5) For the report, does each exploit needs to be documented in detail?
6) Does each box, during the exam, has more than few vulns just to trick you into the rabbit hole?
7) Is there signal or tell-tale sign that you could sense it’s rabbit hole?
8) How extensive is the password cracking vuln involve? E.g. Requires obtaining hashes, then bruteforce it?
Sorry for many questions, and thanks in advance for your reply!
Hi, thank you!
1. You can use any tool you like in the labs. You cannot use automated vulnerability scanners like Nessus and Open-VAS during the exam. Personally I would recommend you to not rely on them in the labs.
2. With a vulnerability assessment I am talking about translating the enumeration details like open ports, service banners etc. to known vulnerabilities. For example FTP server 1.2 is vulnerable to a directory traversal, Proof of concept is available on exploit-db.
3. If a box has multiple vulnerabilities I suggest to check exploit-db for proof of concepts codes and/or exploits. Often you need exploit multiple vulnerabilities to get shell. For example Remote code execution vulnerability in combination with upload functionality.
4. Automated vulnerability scanners and tools are not allowed during the exam. Metasploit use is very limited. Once you get there, you will be informed about what to use and what not.
5. The exam guide contains all information about what you need to document. You will get it before the exam and you can read about this in the user panel.
6. Be prepared for rabbit holes.
7. Experience is key, so work your way through the labs.
8. You will learn about brute forcing passwords and hashes. Have a look at your user panel too when you’ve signed up.
Thank you so much!
I failed my OSCP exam.
During OSCP exam I was doing the machine with buffer overflow.
It seems that I follow the methodology. Get EIP, ESP, Bad characters.
My problem was to generate a payload with out bad characters. The tool use was msfvenom.
However when I use msfvenom with 2 bad characters. My msfvenom crashed in kali2.
Did you have this error? at the end I fail the buffer overflow and fail exam.
May I contact you?
Hi,
If I understand correctly, Kali Linux crashed when generating a payload with 2 bad characters using msfvenom? I’ve never had this error, can you post the command here?
Sure, you can contact me.
Hi,
A very nice article and it add’s up confidence to me to book for online training and exam. Just a few questions:
1.) How did you prepare to bounce back from your first attempt. Specifically when you encounter those “rabbit holes”.
2.) Can we use our own custom script?
3.) I know that the course it self is not enough, but does it give you the pattern how the exam will go through?
Thanks so much! =)
congrats to me I passed too.
Hello,
Thanks for such a good article. I am a B.Tech. II year Computer Science student and have a little knowledge of hacking as I did a course in it. I want to take up this course, can you please help me to take the right path. I searched a lot of things about it in last 2 days, but I think I can not take this course as there is a registration fee of 800 USD (if I am not wrong) which is a huge amount for me. Can you tell me how you applied for the course? This course is really interesting and gained a lot of attention from my side. Can you tell me the procedure to register for the course and what is the registration fee? I also want to ask about the time period of the course (how long the course is?). In short, can you please give a brief explanation of the course containing all things like how to apply, what is the fee, course structure, pre-requisite, when to apply, course duration, where we can apply, etc.
Congratulations for your OSCP certificate.
Thanks in advance :D
Hi!
Thank you, i’m glad you like the review. What exactly is your questions? I mean all details about pricing etc. is on the offensive security website. The price for Penetration Testing Training with Kali Linux is from $800-$1.150 USD for a lab duration of 30 to 90 days. I can understand that this can be a huge chunk when converting from other currencies.
Anyway, I hope you find a way to do this course!
Best of luck,
Hacking Tutorials
Yes, it will be helpful if you provide all the details about the course.
Thanks in advance.
Hi,
Awesome review! I start the course in a few weeks. I know you mentioned metasploit being limited during exam time, I’m a systems engineer and I haven’t had real experience in pen testing, should I to go through their free metasploit course to get the juices flowing prior to PWK?
This may be a trivial question, but are you able to practice on a box multiple times to fine tune skills/techniques?
Thanks,
Glenn
Hi Glenn!
Thanks, great you liked it!
Metasploit usage is limited during the exam; you are allowed to use an exploit module once during the exam, except the multi/handler module. You can use the multi/handler module as much as you need. Also, you are not allowed to use any post exploitation modules. Therefor it is recommended to not rely totally on Metasploit during the time in the labs. Before the exam you will receive an exam guide which clearly explains what is allowed during the OSCP exam and what not.
To prepare for the course I would recommend you to take a look at the tutorials in the Metasploit/Metasploitable 2 section here on hacking tutorials. Especially the enumeration tutorial, vulnerability assessment tutorial, exploitation tutorials and the tutorials in the networking section will be great for basic preparation.
Regarding your question about practicing multiple times on boxes; you can practice as much on any box as you like and you labtime allows to.
Good luck on PWK!
Best regards,
Hacking Tutorials
Hi,
Congratulations for your OSCP certificate!!!.
Great review and analysis of the entire process involved. Arguably the best help for OSCP preparations.
I am a software developer with 2.5 years of experience in Java. I am very much interested in cyber security and want to pursue it as a career. I am planning to do OSCP and have some doubts regarding it. I have a basic knowledge of python and shell scripting and am little weak in networking.
1. Will 3 months of self study be apt before starting the labs as my plan is to take the course for 90 days after the self study period.
2. In the self study period, am planning to study networking and shell scripting, is anything else required?
3. In networking, how much pre knowledge is required before starting the course?
Thanks,
Rahul
Hi!
Thank you very much, great you liked the review!
1. Personally I think if you spend those 3 months well, it is a great preparation for the course. Also have a look at my other tutorials (especially the enumeration/vulnerability assessment/exploiting tutorials in the Metasploit section) and the books mentioned in the review.
2. Only basics of networking are required in my opinion. During the course you will learn about bind- and reverse shells, port forwarding etc.
3. The basics will be sufficient. Also note that you don’t need to know everything before the course.
Good luck and if you have more questions, do not hesitate to contact me!
Best regards,
Hacking Tutorials
Thanks a lot for the quick and great reply.
Can you give me some books or links where i can brush up my networking skills. Is the knowledge of protocols like FTP,HTTP,ICMP,SMTP required?
Can you please provide me any links where i can learn these by doing as it helps in retaining in the longer run.
As the certification cost is a bit on the higher side and i have some financial constraints i was planning to have the necessary skills beforehand so that i can be on top of the process. And thanks again for the help!!!
Yeah, I understand.
Personally I would recommend Georgia Weidmann – penetration testing. It covers a lot of subjects, from basics to more advanced.
Basic knowledge of protocols is required, like connecting to SMTP servers with telnet. Connecting to FTP and MySQL from the command line etc.
Thanks A lot for the reply!!!!!
Hi,
I know that metaslpoit is prohibited from being used in the exam. What are the other tools (like nmap, hydra ) that are not allowed to use in the exam?
Hi,
Automated tools are not allowed; vulnerability scanners, sqlmap etc. You will be informed about what is allowed and what not before the exam.
great.
can you tell me how I can write a oscp report ?
because I am afraid about the report ? I do not know how to write it
Don’t be afraid for the report. It’s easy, really. There is a great sample report with the course too which shows you exactly how to write the report.
Good luck!
Hi,
Thank you for this great review. How many many hours of learning (including labbing) do you think is enough for the course? (Assuming good networking expeirence and basic haking skills)
Thank you in advance,
Hi,
A lot! You can finish the courseware in a couple days but the labs are the most time consuming part of the course. This is not a course for those who cannot afford to spend a lot of time on it for the full duration of the course. Some lab machines take days to complete while others can be rooted in a few hours. Personally I would suggest at minimum 20 hours a week.
BR,
Hacking Tutorials
Thank you for the thorough review. I have a couple questions.
1. Did you use the Kali Linux VM provided by Offensive Security?
2. Did you use VMware workstation? If so, are snapshots of the Kali VM needed in this course?
I’m hesitant on spending money on VMware workstation pro and I’m thinking of using the free VMware workstation player, which only limits you to running 1 VM at a time, however I lose the ability to create snapshots. Your thoughts?
Thanks!
Glenn
Hi, thank for the compliments!
1 & 2: I used the virtual machine provided by Offensive Security for just a part of the course. After updating the host system or VMWare Player free, the VM kept crashing every hour or so. I think this was related to my system. Instead of solving this problem I reinstalled a fresh Kali Linux on a dedicated machine and used that for the remaining part of the course. And by the way, the free version is not restricted to running 1 machine, you can run multiple VM’s at the same time. The free version does not have snapshot functionality, but do you really need this? You can also back-up the VM instead of keeping snapshots.
Good luck and if you have more questions, just leave a message here.
Best regards,
Hacking Tutorials
Hello there,
Just to expand on this, an alternative will be to useVirtualBox since you can take snapshots, just use the vsftool. See the following link for a tutorial: https://www.howtogeek.com/125640/how-to-convert-virtual-machines-between-virtualbox-and-vmware/
You can install Vbox guest additions, and put a shared folder between your host system and the VM. I will start next Saturday, and I like taking snapshots. My host system is Linux mint 17, and so far I dint have any problems. Also, Using a windows host instead might let you do copy/paste of files as in VMWare (the functionality does not alway work with Linux).
Hope that helps.
Congrats on your achievement. Well done!
I was in the student forum looking for the walkthrough by Offensive Security for machine 71, but can’t find it. Can you please provide a link to get to it.
Thank you in advance
The walkthrough is the first thread in the forums for box 71..
Hi,
Congrats on your great achievement, Well Done.
I am in a software development role in a company. I have no experience in security. Will OSCP help me get a pen-testing job as i am very much interested in it. Will it help me in getting a good job and overcome the barrier of “no relevant experience”?
I have started studying networking to prepare for the OSCP course and hope to start the course in a couple of months.
Thank you in advance
Hi,
I think OSCP can definitely help you find a job in the field of information security. Ofcourse everything depends on your background, experience, degree’s and certification and ofcourse the employer/company.
Good luck!
Dear author
I’m interested in OSCP exam. I need to ask, when taking this exam, do you go to an exam center or you simply do it online though VPN access provided to you?
Hi Bruce,
The exam is online through a VPN connection, you do not have to go to an exam center.
Just wanted to say thank you for this write up and the information through the comments here. My course begins this month and this has been very helpful to prepare myself for what lies ahead.
You’re welcome! Good luck with the course!
Hi, Is the OSCP exam an open book or closed book? Can I take custom built scripts into the exam environment with me? Or I will be required to write my scripts from scratch inside the exam environment? Your input is valuable.
Hi Bruce,
You can use the courseware and also custom build scripts. Personally I’ve wrote some enumeration scripts automating a small part of the enumeration process. This saves you some time during the exam.
Hi Admin
This information is so valuable and thanks for your support. I’m gathering all the relevant information I might need before starting the OSCP labs. In other words, I’m PLANNING.
Great! It’s a good thing to gather information and prepare for OSCP!
Good luck!
congrats on the certification mate..!!!
Nice review on the exam…Going through the comments solved all my questions just one remaining..
Do we have to pay again 800$ for 2nd attempt ?
Thanks!!
No, an exam retake costs USD 60.00 and if you fail the exam and renew labtime, the labtime includes a new exam attempt.
No. The re-write is about $65 only. Secondly, the cert does not expire, once achieved. I’m also working towards in obtain this lifetime cert.
Have you started the course already?
I have just completed the CEH exam last week, with a very good score (95.2%)
I’m planning to do the CCNA security, to familiarize myself with firewalls and IPS/IDS, then opt for the OSCP. Is CCNA Security necessary, or should I dive straight into OSCP ? By the way, I’m quite comfortable with basic Linux operations (I am certified RHCE-7) and basic security (CompTIA Security Plus certified)? But I have no prior knowledge to Windows Active Directory. What can you suggest/recommend?
Great, and nice score!
Personally I think you don’t have to be an expert in every subject, remember you will learn a lot during the course too. Also I don’t consider CCNA Security or CompTIA Security+ necessary to pass OSCP or start the course. I do recommend to spend enough time on OSCP and the labs, along the way you will find out which skills you need to develop further (mine were web application hacking and a little privilege escalation).
The following book helped me a lot: The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws by Dafydd Stuttard and Marcus Pinto
Thanks for the recommendation. I have one more question, please. The exam is precisely 23hrs 45 mins before you are disconnected from VPN, then you have another 24 hours to submit the documentation. Is that correct?
Yes, That is correct.
This is blog is really exciting me:
1. If I were to invest at least 4 hours a day on hands-on, how long can I be ready (just an estimate)?
2. Will a custom lab (https://youtu.be/UaxzHqcCE7A) be helpful, in addition to the official lab during the exam preparation?
NB: The custom lab can accommodate routers, switches, firewalls, IPS/IDS, windows desktops and servers, linux desktops and servers, android, and Kali linux. And you can have multiple networks too, as seen in the video. Your opinion is valuable.
4 hours is a start, some boxes take a lot of time to root which makes spending more time than 4 hours more effective. Personally I spend like 10-12 hours a day during the weekends and I took a week of from work for OSCP twice.
Personally I would recommend to spend your time during OSCP on the OSCP labs. If you can root most of the lab machines than you will be ready for the exam.
Great information and advice. I will consider that. Your story inspires me, that is why I am fascinated. And I have always wanted to attempt for the OSCP exam. Thank for the swift responses too. Will keep in touch.
Hello,I am new in hacking world, I want to know what are prerequisite to do oscp, And what is its scope in India.
Thank you
Hi
I want to ask about the oscp report!! can you tell us how to write it !!
because I’m afraid about report !!
thanks a lot of
Awesome review! thanks for sharing. Regarding web application testing, what chapters do you recommend from the Web Application Hacker’s Handbook? Or, it will be enough reading the Gerogia Weidman Penn testing Book? I have been using it to prepare myself for PWK!
Thanks!
In general the courseware supplied by Offensive Security is sufficient. The Georgia Weidman Penetration testing Book covers a wide range of basic subjects in the field of penetration testing which is a nice preparation and allows you to go trough the OSCP courseware faster in my opinion. The Web Application Hacker’s Handbook focuses on web applications only. If you’re planning to read it then I recommend to read the full book.
Good luck with OSCP!
I have read all comment on your website and also read and implement metasploit 2 vulnerability. I want to know about exploit compilation and modification. I have done with metsploit. now i want to know without metasploit .I have little bit knowledge about python , shell script and more on c. could you suggest me some source and link which will help me .
Hello,
I am an info sec governance guy. I have CCNA, CCNP, CISSP, CISM, CRISC.
Do you think this exam is for me? I am not planning to work into technical security but stay on governance side.
I know every knowledge helps but what I am asking is should I consider this or focus more on Cloud Security?
Regards
Z.
Hi,
It’s hard to say, OSCP is not an easy certification you ‘pick up along the way’ and requires you to invest a lot of time. If you can do that I personally think it’s a good an valuable in combination with a GRC background. Also have a look at the resources mentioned in this review, i’m sure they will be pretty helpful.
If you have more questions or need some help on the practical side you can contact me by e-mail or Twitter.
Best regards,
Hacking Tutorials
After 17 years of doing pentests for Governments and Big Cats, I decided to try PWK/ OSCP to settle a friendly debate between me and an OSCP hacker who had just been terminated coz he had no idea what to do …..
Wow, OSCP is a load of tosh! Not withstanding the fractured pedagogy and purposeless Labs; buffer overflows and aggressive SQLi without any countermeasures being recommended ??? If anyone suggested those to any of my Fortune 500 Clients, then you’d be fired. In my company we pay CEH/ECSA/LPT hackers USD 420+ per hour; OSCP’s are not in our Tiger Team as not one single Client allows it. OSCP is for anyone who thinks they are mischievous enough for LulzSec, cDc or AnonOps, so certainly not in the “ethical” category that IT Depts require to get them compliant with PCI_DSS or ISO 2700x.
Thankfully, I do not need OSCP for any purpose, but my advice is if you want to cause mischief go for OSCP, if you want a career get CEH or ECSA/LPT, and lots of experience.
DucatiNat
BSc, MSc PhD CISSP+ CEH ECSA LPT GPEN
The review and comments are all amazing.
If possible, could you share if there is an advance web security in the course or exam? I’m from Networking background and i have zero knowledge on web security path.
should i straighten myself to be strong at web first or just get some basic knowledge to enroll the OSCP?
Hi,
This course does not contain advanced web security topics, just some basics. I wouldn’t say it’s required to work on strong web skills before starting OSCP. Personally I was in the same situation as you and the OSCP courseware, plus some of the resources mentioned in the review, were sufficient to overcome the web challenges in the labs and during the exam.
Good luck!
Hello,
Thank you for this article, its really helping me in preparing for the course. Lot of the questions that i had have been answered here. I have done CEH, and now I am planning to go for this cert.
Just had a couple of questions :
-Is assembly language required for this course?
-Regarding exam: Going through your article, i understand that this exam is taken from home on our own computers and not in a center like EC council’s. So, during the 24 hour exam time,what if my internet disconnects or there happens to be a power outage like maybe for 2-3 hours, means i lose that amount of time during exam? Is there any kind of workaround for this? Because power outages are pretty common at my place.
Hello,
You’re very welcome, glad you liked the article!
Regarding your questions:
1) Knowing assembly language is not required for this course.
2) The exam is indeed online and taken from your home location, you don’t have to travel to an exam centre. When you’re being disconnected from the internet the VPN connection drops and you will have to reconnect. If there’s a power outage you will lose all exam time for the duration of the outage. If there’s a lot of power outages at your place I would recommend to consider taking the exam in a place with lesser or no power outages. Losing a couple hours exam time can definitely make a difference in the exam outcome.
Good luck!
This is such an great review, well done!
Also congratulations on obtaining your certification :)
You do great work and inspire many, keep at it!
Hej,
congratulations. Your report was fantastic and very clear. I just did not get what a rabbit hole is…
I am going to enroll soon for the same certification and hope to have a great experience as you actually did have.’
One question only. Is Python and bash scripting required for passing the exam?
Thanks,
Alex
Hi Alex,
Thank you! Python and Bash scripting knowledge is not really ‘required’ for passing the exam. During the course and lab time you will learn how to read and modify scripts written in Bash & Python, generally this is sufficient for getting all scripting knowledge you need to pass the exam. Personally I’ve written an enumeration script in Bash before the exam to save time, this proved to be really helpful and can be a good exercise when you’re unfamiliar with scripting languages.
A rabbit hole during OSCP is when you think you’ve found a vulnerability on a box that will give you root access but after spending a lot of time on it you hit a dead end. You’ve went down the rabbit hole and found out another services was also vulnerable. This usually happens when you focus on the first possible vulnerability that you’ve come across instead of doing a proper vulnerability assessment. Personally I think avoiding such rabbit holes can make the difference between passing and failing the exam due to the limited mount of time you’ve got.
When will you sign up?
Best regards,
Hacking Tutorials
Congrats on your OSCP certification and nice review! I’ve also used https://www.virtualhackinglabs.com in preparation for OSCP and I can definitely recommend this source to anyone.
Hey first of congratulations on trying harder
My question is can a college student give oscp exam with no prior experience in IT field.
Thanks! It could be possible when you spend a lot of time on studying and completing labs. Prior experience in the field might help but is not strictly necessary I think.
Hello, i understand its a long time you passed but anyway congrats on passing oscp. You have explained very well and really appreciate your efforts.
I am having exper. in ccnp level data network, firewall, proxy, windows server/client OS basics and RHCSA level Linux knowledge. I have experience in nmap and vulnerability assessment and mgmt.tools like ISS, openvas CE etc.
I wish to make my base strong to go for oscp. Kindly suggest what should i learn next before taking oscp.