Last year we already did a tutorial on how to install VPN on Kali Linux. Since then a lot has changed and the installation procedure is a little different now. This resulted in a lot of questions by our readers through comments on this website and social media. In this tutorial we will be installing VPN on Kali Linux 2016 rolling edition using OpenVPN and also the VPN service from Golden Frog again as we did in the last tutorial. Of course you can use any VPN provider you like, including free VPN services, since the installation procedure will be practically the same for any provider. If you do not have a VPN provider yet you might as well take advantage of one of the following offers from Golden Frog:
If you sign up using one of the following links you can get a 50% discount:
Or the following offer with 25% off for annual accounts:
Why do I use VyprVPN from Golden Frog?
- 700+ servers worldwide on 50+ locations and free unlimited switching.
- VyprVPN apps for all common platforms for easy server switching.
- Unlimited speed and data usage.
- Golden Frog owns all servers, no 3rd parties.
Installing VPN on Kali Linux 2016
By default the the network settings do not offer an option to set a VPN connection. The first step is to add the OpenVPN option to the network settings menu. For this purpose we need to install OpenVPN in order to be able to add a new VPN connection in the network settings. Let’s start installing VPN on Kali Linux 2016 by using the following command on a new terminal session:
apt-get install network-manager-openvpn-gnome
This command will install the OpenVPN network manager and the additional packages which are needed to have it function properly. The network-manager-openvpn-gnome package only installs the OpenVPN protocol, this is sufficient in most of the cases and certainly if you’re using the Golden Frog VPN service. If you want to install other VPN protocols like PTTP or L2TP, you can use the following command that will install all of them:
apt-get install network-manager-openvpn network-manager-openvpn-gnome network-manager-pptp network-manager-pptp-gnome network-manager-strongswan network-manager-vpnc network-manager-vpnc-gnome
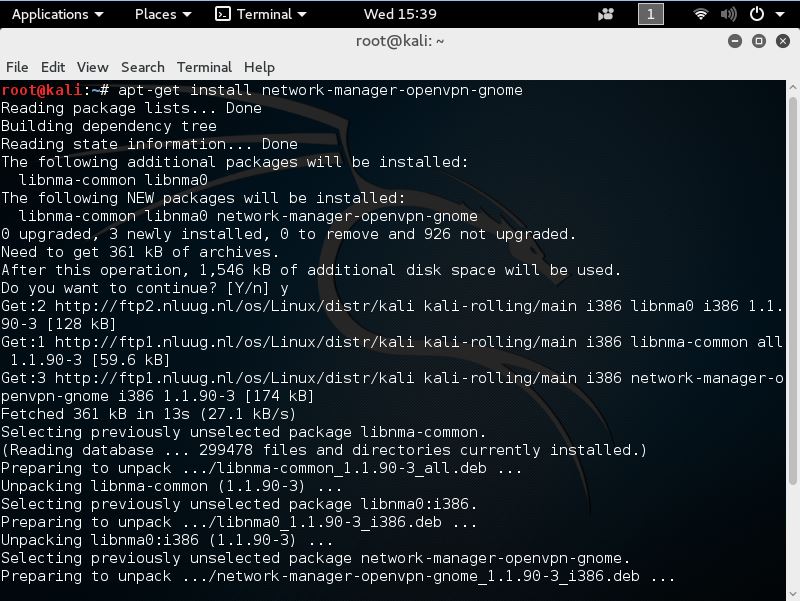
When the installation of all packages has been finished we can continue with the following step: Add a new VPN connection and configure the VPN connection settings. Let’s start with adding a new VPN connection in the network settings by navigating to the settings menu:
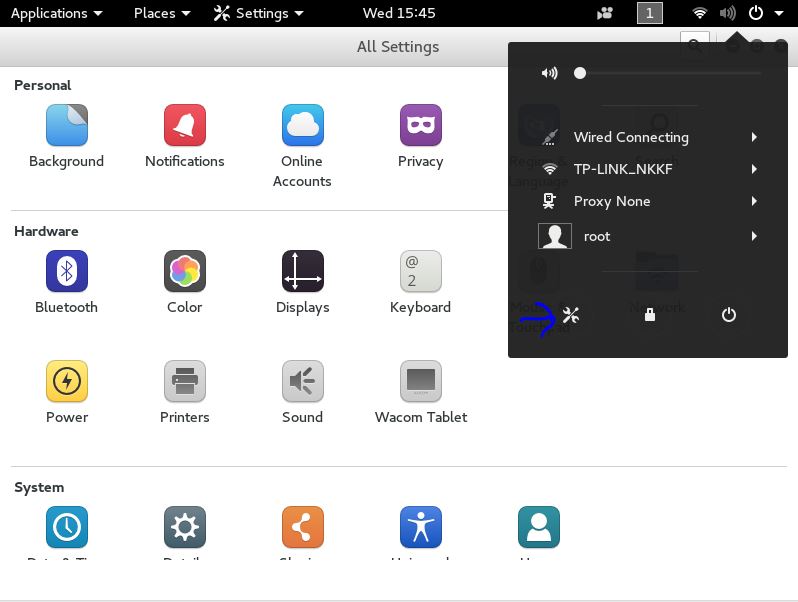
And open the Network settings panel by using the following button:
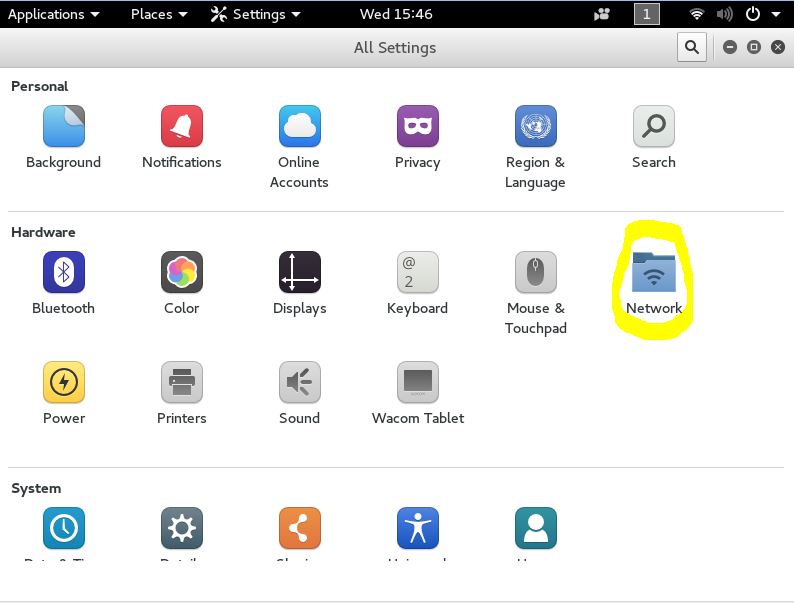
Now click the + sign in the bottom left corner to add a new connection and click “VPN” in the add network connection menu:
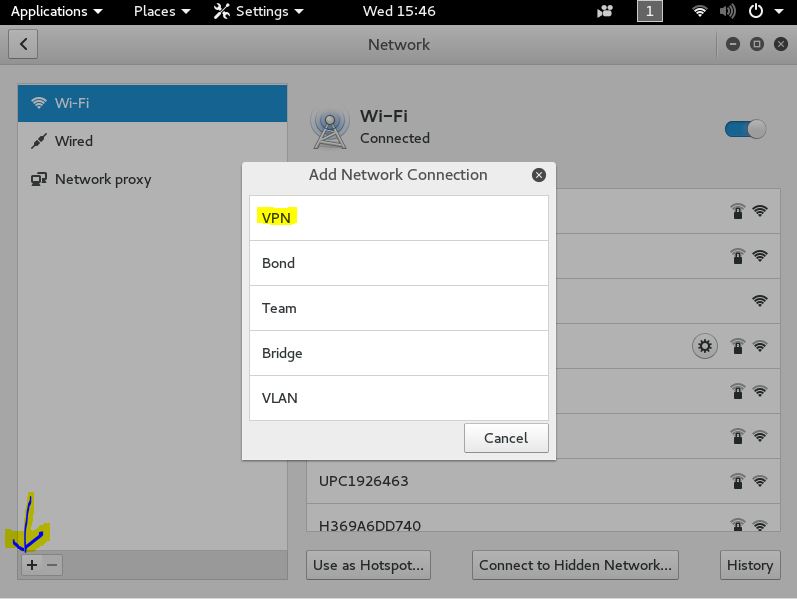
And finally add a new OpenVPN Connection:
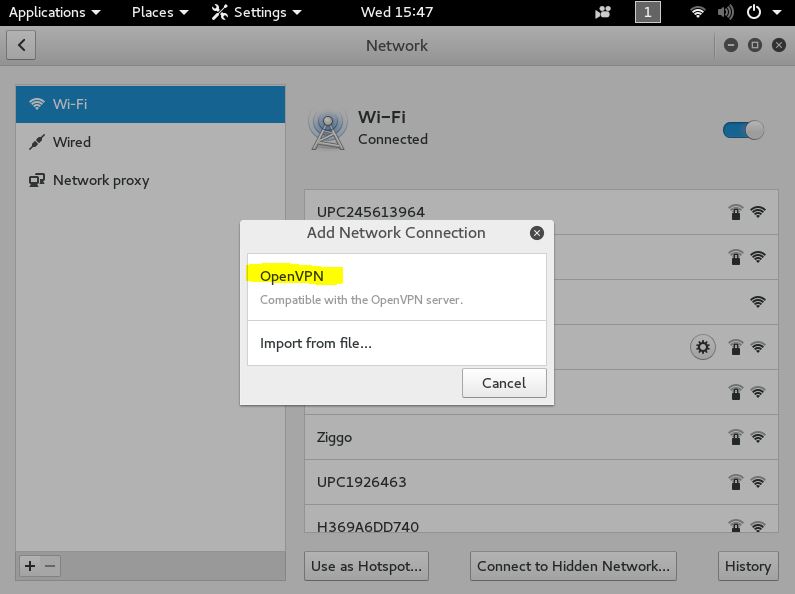
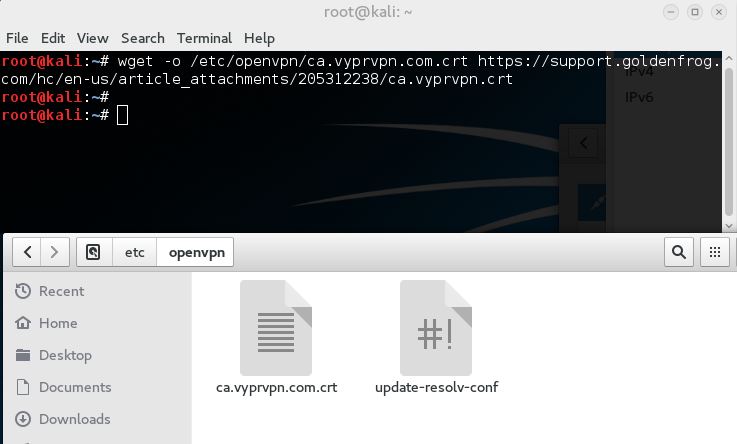
This will take us to the menu where we can define the VPN server settings to set up a connection. In this step we need to define the gateway, login credentials and a VyprVPN Certificate Authority (CA) certificate. Let’s download the certificate first by using the following command:
wget -O /etc/openvpn/ca.vyprvpn.com.crt
https://support.goldenfrog.com/hc/en-us/article_attachments/205312238/ca.vyprvpn.com.crt
You can also download the certificate file manually using the following link:
https://support.goldenfrog.com/hc/en-us/article_attachments/205312238/ca.vyprvpn.com.crt
Make sure that you save the certificate file to the following location:
/etc/openvpn/
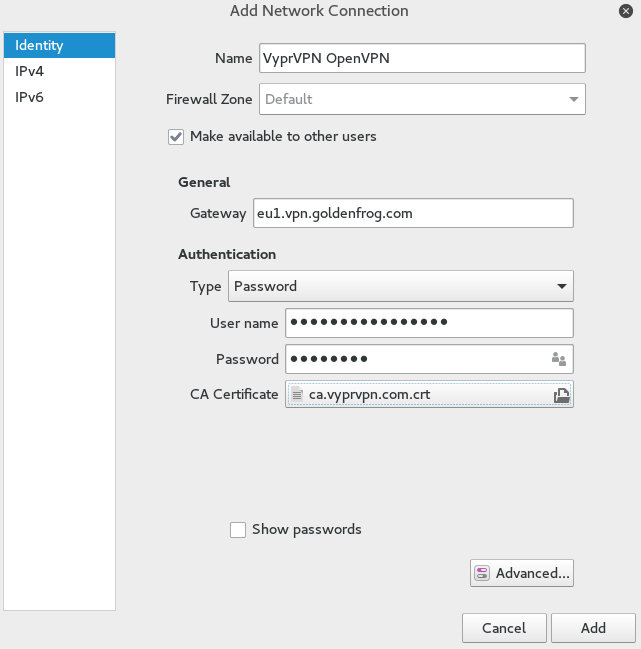
Now we need to specify the gateway and some other settings:
- Name: VyprVPN OpenVPN
- Make available to other users when applicable
- Gateway: VPN server gateway, pick any of these servers from Golden Frog.
- User name: The e-mail address used during registration at Golden Frog
- Password: The password from your VyprVPN account
- CA Certificate: Select the downloaded CA certificate from the following directory: /etc/openvpn/
After entering all the required settings the form should look like this:
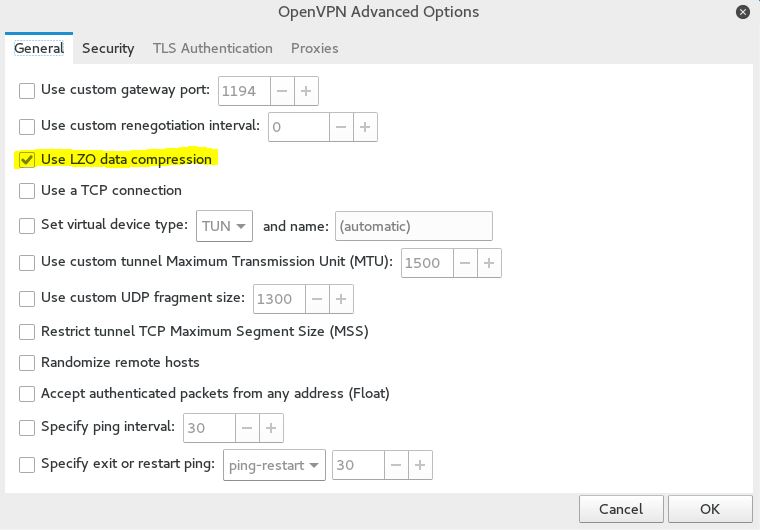
The last step in the setup process is to enable LZO compression in the advanced menu. You can do this by clicking the advanced button in the bottom right corner of the screen and enable LZO compression.
Now close the advanced options menu and apply the changes to the new VPN connection and let’s see if it is working by levering the blue switch in the top right corner of the VPN connection screen to activate the VPN connection:
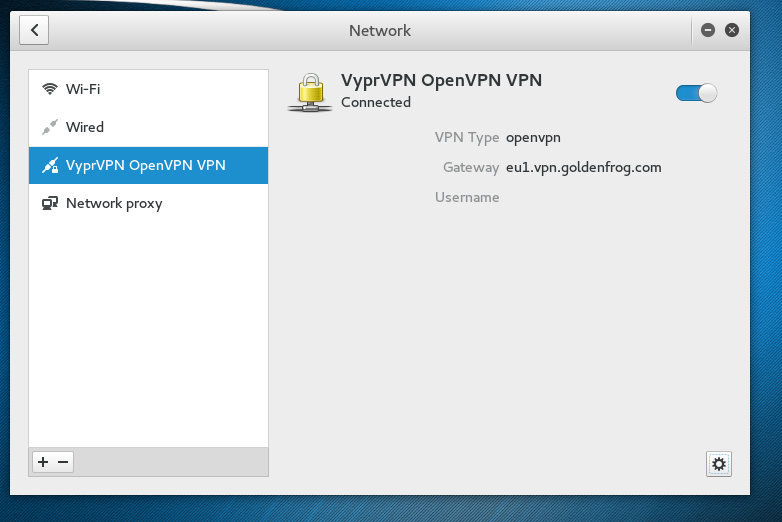
If all settings are valid you should be able to setup a VPN connection successfully. If any errors occur you will be notified with a message looking like: Activation of network connection failed. If this error message occurs you have to check the logs using the following command in the terminal:
journalctl -n100
This will open the last 100 lines of the log. Any errors in the log will be marked red and should clear things up why the error occurred. In the following instance there was a problem with the downloaded certificate, which was solved by downloading the certificate again but manually this time using a browser.
If you have any questions regarding installing VPN on Kali Linux 2016 please use the comment function at the bottom of this page. Thanks for reading again on Hacking Tutorials!




37 Comments
cant connect already tryed downloadig the zert. manually here the logs cant find any errors
— Logs begin at Do 2016-03-31 22:07:13 CEST, end at Do 2016-03-31 23:17:10 CEST. —
Mär 31 23:14:28 D3F4ULT NetworkManager[594]: (eth0): DHCPv4 state changed bound -> done
Mär 31 23:14:28 D3F4ULT NetworkManager[594]: NetworkManager state is now CONNECTED_LOCAL
Mär 31 23:14:28 D3F4ULT NetworkManager[594]: NetworkManager state is now CONNECTED_GLOBAL
Mär 31 23:14:28 D3F4ULT NetworkManager[594]: Policy set ‘FRITZ!Box Fon WLAN 7360 SL’ (wlan0) as default
for IPv4 routing and DNS.
Mär 31 23:14:28 D3F4ULT dbus[568]: [system] Activating via systemd: service name=’org.freedesktop.nm_di
spatcher’ unit=’dbus-org.freedesktop.nm-dispatcher.service’
Mär 31 23:14:28 D3F4ULT systemd[1]: Starting Network Manager Script Dispatcher Service…
Mär 31 23:14:28 D3F4ULT dbus[568]: [system] Successfully activated service ‘org.freedesktop.nm_dispatch
er’
Mär 31 23:14:28 D3F4ULT systemd[1]: Started Network Manager Script Dispatcher Service.
Mär 31 23:14:28 D3F4ULT nm-dispatcher[3127]: Dispatching action ‘down’ for eth0
Mär 31 23:14:44 D3F4ULT dbus[568]: [system] Activating via systemd: service name=’org.freedesktop.hostn
ame1′ unit=’dbus-org.freedesktop.hostname1.service’
Mär 31 23:14:44 D3F4ULT systemd[1]: Starting Hostname Service…
Mär 31 23:14:44 D3F4ULT dbus[568]: [system] Successfully activated service ‘org.freedesktop.hostname1’
Mär 31 23:14:44 D3F4ULT systemd[1]: Started Hostname Service.
Mär 31 23:15:19 D3F4ULT NetworkManager[594]: nm-openvpn-Message: openvpn[3168] started
Mär 31 23:15:19 D3F4ULT NetworkManager[594]: VPN plugin state changed: starting (3)
Mär 31 23:15:19 D3F4ULT NetworkManager[594]: VPN connection ‘VyprVPN OpenVPN’ (ConnectInteractive) repl
y received.
I don’t see any error too. Did you try to restart the network manager?
Best Regards,
Hacking Tutorials
After installing the VPN it asks me for the password, the password screen pops up like 4 times after typing it in and then a notification pops up stating that there was a connection error. What to do?
Hi, Check out the last paragraph of the tutorial and post the result of the following command here:
journalctl -n100
Best regards
Logs begin at Fri 2016-04-01 17:13:54 IST, end at Fri 2016-04-01 18:28:49 IST
. —
Apr 01 18:28:15 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:15 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:15 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:15 Huawei-HG658c-instalacion gvfsd[2232]: ** (gvfsd:2232): WARNING
**: dbus_mount_reply: Error from org.gtk.vfs.Mountable.mount(): Failed to retrie
ve share list from server: Connection refused
Apr 01 18:28:15 Huawei-HG658c-instalacion gvfsd[2232]: ** (process:2983): WARNIN
G **: Couldn’t create directory monitor on smb://x-gnome-default-workgroup/. Err
or: The specified location is not mounted
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d09748] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: resolve_wins: WINS server
resolution selected and no WINS servers listed.
Apr 01 18:28:16 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d09748] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: resolve_wins: WINS server
resolution selected and no WINS servers listed.
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: resolve_hosts: Attempting
host lookup for name WORKGROUP
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: resolve_hosts: getaddrinf
o failed for name WORKGROUP [Name or service not known]
Apr 01 18:28:17 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d09570] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– [smb://WORKGROUP/; 0] dir = (nil), cancelled = 0, errno = [111] ‘Connection re
fused’
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– (errno != EPERM && errno != EACCES), cancelled = 0, breaking
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Performing aggressive shu
tdown.
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: purging s
erver cache
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Context 0xb3d043c0 succes
sfully freed
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: params.c:OpenConfFile() –
Unable to open configuration file “/root/.smb/smb.conf”:
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ** (gvfsd:2232): WARNING
**: dbus_mount_reply: Error from org.gtk.vfs.Mountable.mount(): Failed to retrie
ve share list from server: Connection refused
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: No such file or directory
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: pm_process() returned No
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: lp_load_ex: refreshing pa
rameters
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Initialising global param
eters
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ** (process:2985): WARNIN
G **: Couldn’t create directory monitor on smb://x-gnome-default-workgroup/. Err
or: The specified location is not mounted
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: rlimit_max: increasing rl
imit_max (1024) to minimum Windows limit (16384)
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: params.c:pm_process() – P
rocessing configuration file “/etc/samba/smb.conf”
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Processing section “[glob
al]”
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter workgroup
= WORKGROUP
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter dns proxy
= no
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter log file
= /var/log/samba/log.%m
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter max log s
ize = 1000
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter syslog =
0
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter panic act
ion = /usr/share/samba/panic-action %d
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter server ro
le = standalone server
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter passdb ba
ckend = tdbsam
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter obey pam
restrictions = yes
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter unix pass
word sync = yes
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter passwd pr
ogram = /usr/bin/passwd %u
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter passwd ch
at = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\
supdated\ssuccessfully* .
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter pam passw
ord change = yes
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter map to gu
est = bad user
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: doing parameter usershare
allow guests = yes
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: pm_process() returned Yes
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: lp_load_ex: refreshing pa
rameters
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: params.c:OpenConfFile() –
Unable to open configuration file “/root/.smb/smb.conf.append”:
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: No such file or directory
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: pm_process() returned No
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: added interface wlan0 ip=
192.168.1.4 bcast=192.168.1.255 netmask=255.255.255.0
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Using netbios name HUAWEI
-HG658C-INSTALACION.
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: Using workgroup WORKGROUP
.
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– URI = smb://WORKGROUP/
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– try #0
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: parsed path: fname=’smb:/
/WORKGROUP/’ server=’WORKGROUP’ share=” path=” options=”
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: SMBC_check_options(): ser
ver=’WORKGROUP’ share=” path=” options=”
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: looking u
p cached server ‘WORKGROUP’\’IPC$’, user ‘WORKGROUP’;’root’
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: returni
ng (nil)
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: auth_call
back – anonymous pass
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: auth_call
back – out: last_user = ‘root’, last_domain = ‘WORKGROUP’
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: looking u
p cached server ‘WORKGROUP’\’IPC$’, user ‘WORKGROUP’;’root’
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: returni
ng (nil)
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:18 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d09a18] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: resolve_wins: WINS server
resolution selected and no WINS servers listed.
Apr 01 18:28:19 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d093f8] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: resolve_lmhosts: Attempti
ng lmhosts lookup for name WORKGROUP
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: startlmhosts: Can’t open
lmhosts file /etc/samba/lmhosts. Error was No such file or directory
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: resolve_wins: WINS server
resolution selected and no WINS servers listed.
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: resolve_hosts: Attempting
host lookup for name WORKGROUP
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: resolve_hosts: getaddrinf
o failed for name WORKGROUP [Name or service not known]
Apr 01 18:28:20 Huawei-HG658c-instalacion gvfsd[2232]: name_resolve_bcast: Attem
pting broadcast lookup for name WORKGROUP
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: samba_tevent: EPOLL_CTL_D
EL EBADF for fde[0xb3d093c0] mpx_fde[(nil)] fd[14] – disabling
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– [smb://WORKGROUP/; 0] dir = (nil), cancelled = 0, errno = [111] ‘Connection re
fused’
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: do_mount
– (errno != EPERM && errno != EACCES), cancelled = 0, breaking
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: Performing aggressive shu
tdown.
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: ** (gvfsd:2232): WARNING
**: dbus_mount_reply: Error from org.gtk.vfs.Mountable.mount(): Failed to retrie
ve share list from server: Connection refused
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: ### SMB-BROWSE: purging s
erver cache
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: Context 0xb3d02e68 succes
sfully freed
Apr 01 18:28:21 Huawei-HG658c-instalacion gvfsd[2232]: ** (process:2978): WARNIN
G **: Couldn’t create directory monitor on smb://x-gnome-default-workgroup/. Err
or: The specified location is not mounted
Apr 01 18:28:47 Huawei-HG658c-instalacion gnome-session[2186]: (gnome-shell:2312
): mutter-WARNING **: STACK_OP_RAISE_ABOVE: window 0x5f00e00015 not in stack
Apr 01 18:28:48 Huawei-HG658c-instalacion dbus-daemon[2170]: Activating service
name=’org.gnome.Terminal’
Apr 01 18:28:48 Huawei-HG658c-instalacion dbus-daemon[2170]: Successfully activa
ted service ‘org.gnome.Terminal’
Apr 01 18:28:49 Huawei-HG658c-instalacion gnome-session[2186]: (gnome-shell:2312
): mutter-WARNING **: STACK_OP_RAISE_ABOVE: window 0x5f00e00015 not in stack
Apr 01 18:28:49 Huawei-HG658c-instalacion gnome-session[2186]: (gnome-shell:2312
): mutter-WARNING **: STACK_OP_RAISE_ABOVE: window 0x5f00e00015 not in stack
Apr 01 18:28:49 Huawei-HG658c-instalacion gnome-session[2186]: (gnome-shell:2312
): mutter-WARNING **: STACK_OP_RAISE_ABOVE: window 0x5f00e00015 not in stack
The log is too short and doesn’t contain any entries related to OpenVpn. There should be something like:
Huawei-HG658c-instalacion gvfsd[2232]: nm-openvpn-Message: openvpn[3168] started
Try connect to the VPN and run the log again. If 100 lines is too short than you need to change the command to the following so you get a 1000 lines:
journalctl -n1000
journalctl -n100
— Logs begin at Пн 2016-04-11 10:36:31 MSK, end at Пн 2016-04-11 15:46:04 MSK.
апр 11 15:44:48 dotu gnome-session[702]: NMVPNSection<.setActiveConnections@reso
апр 11 15:44:48 dotu gnome-session[702]: wrapper@resource:///org/gnome/gjs/modul
апр 11 15:44:48 dotu gnome-session[702]: NMApplet<._syncVPNConnections@resource:
апр 11 15:44:48 dotu gnome-session[702]: wrapper@resource:///org/gnome/gjs/modul
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.3485] vpn-connecti
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.3671] vpn-connecti
апр 11 15:44:48 dotu NetworkManager[562]: nm-openvpn-Message: openvpn[6808] star
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4283] vpn-connecti
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4285] vpn-connecti
апр 11 15:44:48 dotu nm-openvpn[6808]: OpenVPN 2.3.10 i586-pc-linux-gnu [SSL (Op
апр 11 15:44:48 dotu nm-openvpn[6808]: library versions: OpenSSL 1.0.2g 1 Mar 2
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4472] vpn-connecti
апр 11 15:44:48 dotu NetworkManager[562]: (nm-openvpn-service:6805): nm-openvpn-
апр 11 15:44:48 dotu nm-openvpn[6808]: WARNING: No server certificate verificati
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4484] vpn-connecti
апр 11 15:44:48 dotu nm-openvpn[6808]: NOTE: the current –script-security setti
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4497] vpn-connecti
апр 11 15:44:48 dotu nm-openvpn[6808]: Error reading PKCS#12 file /root/ca.vyprv
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4510] vpn-connecti
апр 11 15:44:48 dotu nm-openvpn[6808]: Exiting due to fatal error
апр 11 15:44:48 dotu NetworkManager[562]: [1460378688.4545] vpn-connecti
апр 11 15:44:53 dotu gnome-session[1064]: (gnome-shell:1188): mutter-WARNING **:
lines 1-23
i did it but when i check dns leak test (website) it shows my real location why ??
I’m using a wired connection and have the VPN enabled, but it isn’t working….still showing my real IP address. Anything idea why?
i try to connect but when turn to on the switch take a message :
##You need to Authenticate to access th Virtual Private Network ” Italy OpenVPN “##
##password …. ##
then i write the password
i take the message :
##An application want access to the keyring “Default Keyring” but is locked##
##password…##
i write the password but nothing
then i write to the terminal :
journalctl -n100
and the red lines is :
TLS Error: TLS object -> incoming plaintext
Sep 17 17:53:37 kali nm-openvpn[2807]: TLS Error: TLS handshake failed
and
VERIFY ERROR: depth=1, error=self signed ce
Sep 17 17:53:39 kali nm-openvpn[2807]: OpenSSL: error:14090086:SSL routines:ssl3_g
Sep 17 17:53:39 kali nm-openvpn[2807]: TLS_ERROR: BIO read tls_read_plaintext erro
Sep 17 17:53:39 kali nm-openvpn[2807]: TLS Error: TLS object -> incoming plaintext
Sep 17 17:53:39 kali nm-openvpn[2807]: TLS Error: TLS handshake failed
can you help me ?
thank you for your time
Are you running Kali Linux?
~# apt-get install network-manager-openvpn
Reading package lists… Done
Building dependency tree
Reading state information… Done
E: Unable to locate package network-manager-openvpn
what should i do i only want to install mullvad on my kali linux and i can’t find any instructions :/
same problem bro…
go to Terminal type
apt update && apt full upgrade
after this reboot u’re system then type
apt-get install network-manager-openvpn-gnome
reboot u’re system
got to settings -> network -> vpn-> add …..
I had an issue with using Kali Linux 2016.2 and OpenVPN while using user with low privileges. I followed PIA instructions and managed to connect to the service using GUI. Although the Internet was not reachable while using network-manager-openvpn-gnome, but worked flawlessly using directly with openvpn. While connecting to the VPN via CLI I was forces to use root account [sudo]. Later this gave me an idea why the issue might be occurring. The solution I found was to change permissions directly in the configuration files. All network configuration files are stored in /etc/NetworkManager/system-connections/. Open the file with sudo nano vpn_connection and instead “permissions=” change to “permissions=root”. Worked like a charm. Hope you will find this useful. I was pulling my hairs out and did not find any similar solution on the net.
Apologies, little mistake. Connection started to work after setting cipher=AES-128-CBC, not the permissions field. I have set both on the same time, but make wrong assumptions.
I need help. There is a message that says package network-manager-openvpn-gnome is not available, but is referred to by another package. I’m getting the same error for each package. Please help
Check your /etc/apt/sources.list file.
Kali Rolling is expected to have the following entries in the sources.list file:
deb http://http.kali.org/kali kali-rolling main contrib non-free
# For source package access, uncomment the following line
# deb-src http://http.kali.org/kali kali-rolling main contrib non-free
thanks
I just did that but now I have another problem, I dont see the openvpn option when I click the vpn option. Please help.
What command did you run with apt-get ?
Apt-get install network-manager-openvpn-gnome
And i tried the rest as well
Im having a problem getting past the Authenticate part, I changed the permissions to “root”
But no luck yet, can anyone help me, starting to regret upgrading to Rolling.
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.h
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined script
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.htm
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mit
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: F
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mi
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#m
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]:
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
Nov 22 05:09:22 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:25 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:27 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:29 T4CN4YN NetworkManager[482]: [1479812969.2712] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mit
Nov 22 05:09:30 T4CN4YN nm-openvpn[1621]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link local: [undef]
Nov 22 05:09:31 T4CN4YN nm-openvpn[1621]: UDPv4 link remote: [AF_INET]216.166.57.55:1194
Nov 22 05:09:34 T4CN4YN nm-openvpn[1621]: [de1.vyprvpn.com] Peer Connection Initiated with [AF_INET]216.166.57.55:1194
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: AUTH: Received control message: AUTH_FAILED
Nov 22 05:09:36 T4CN4YN nm-openvpn[1621]: SIGUSR1[soft,auth-failure] received, process restarting
Nov 22 05:09:38 T4CN4YN NetworkManager[482]: [1479812978.5852] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2381] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: F
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
Nov 22 05:10:39 T4CN4YN nm-openvpn[1621]: Exiting due to fatal error
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2636] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2663] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:39 T4CN4YN NetworkManager[482]: [1479813039.2679] vpn-connection[0x1cc5110,d0247264-6153-4fb2-9a59-ffb5c72a8dad,”Vypervpn”,0]: V
Nov 22 05:10:42 T4CN4YN dbus-daemon[964]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Nov 22 05:10:42 T4CN4YN systemd[948]: Starting GNOME Terminal Server…
Nov 22 05:10:43 T4CN4YN dbus-daemon[964]: Successfully activated service ‘org.gnome.Terminal’
Nov 22 05:10:43 T4CN4YN systemd[948]: Started GNOME Terminal Server.
lines 79-101/101 (END)
the ERROR is on the bottom.
T4CN4YN nm-openvpn[1621]: ERROR: could not read Auth username/password/ok/string from management interface
First time it didn’t connect, i used the command and everything said critical but nothing was red. I tried to turn it on again anyway, it asked for password again and again. Any idea what’s happening?
What does the log say?
Hello!
what is the password? Or where is it?
Thanks.
Hi!
You will get a password when signing up with GoldenFrog.
Remember to apt-get update after correcting the sources.list file.
how to sign up on the GoldenFrog
it is not free guys…
You are right, it is not a free VPN provider but a premium one.
Sir please help, can’t connect .it asks for password then i type it and then it gives a message try again .
here is the result of journalctl -n100 – # I have listed only the error part
Apr 22 06:25:59 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:26:04 KALI06 NetworkManager[635]: [1492822564.1809] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4803] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242]: send SIGTERM
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] wait for 1 openvpn processes to terminate…
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: ERROR: could not read Auth username/password/ok/string from management interface
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: Exiting due to fatal error
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] exited with error code 1
…skipping…
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.08
Apr 22 06:25:34 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] started
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: chroot will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: UID/GID downgrade will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:40 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:41 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:25:46 KALI06 NetworkManager[635]: [1492822546.9594] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:49 KALI06 anacron[2796]: Job `cron.weekly’ started
Apr 22 06:25:49 KALI06 anacron[4252]: Updated timestamp for job `cron.weekly’ to 2017-04-22
Apr 22 06:25:54 KALI06 NetworkManager[635]: [1492822554.0139] keyfile: update /etc/NetworkManager/system-connections/VyprVPN OpenVPN (f9719cb8
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 anacron[2796]: Job `cron.weekly’ terminated
Apr 22 06:25:57 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:59 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:26:04 KALI06 NetworkManager[635]: [1492822564.1809] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4803] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242]: send SIGTERM
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] wait for 1 openvpn processes to terminate…
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: ERROR: could not read Auth username/password/ok/string from management interface
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: Exiting due to fatal error
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] exited with error code 1
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4925] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4926] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4934] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: DRM: resuming kernel object tree…
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: bus: MMIO write of 0000001f FAULT at 6013d4 [ IBUS ]
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: DRM: resuming client object trees…
Apr 22 06:26:13 KALI06 kernel: ACPI Warning: \_SB.PCI0.RP05.PEGP._DSM: Argument #4 type mismatch – Found [Buffer], ACPI requires [Package] (20160108/n
Apr 22 06:26:13 KALI06 kernel: ACPI: \_SB_.PCI0.RP05.PEGP: failed to evaluate _DSM
Apr 22 06:26:13 KALI06 kernel: ACPI Warning: \_SB.PCI0.RP05.PEGP._DSM: Argument #4 type mismatch – Found [Buffer], ACPI requires [Package] (20160108/n
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: evicting buffers…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: waiting for kernel channels to go idle…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: suspending client object trees…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: suspending kernel object tree…
Apr 22 06:26:33 KALI06 plugin-containe[4343]: g_path_get_basename: assertion ‘file_name != NULL’ failed
Apr 22 06:27:09 KALI06 firefox-esr.desktop[4262]: 1492822629805 addons.productaddons ERROR Request failed certificate checks: [Ex
Apr 22 06:28:22 KALI06 dbus-daemon[844]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Apr 22 06:28:22 KALI06 systemd[838]: Starting GNOME Terminal Server…
Apr 22 06:28:22 KALI06 dbus-daemon[844]: Successfully activated service ‘org.gnome.Terminal’
Apr 22 06:28:22 KALI06 systemd[838]: Started GNOME Terminal Server.
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.08
Apr 22 06:25:34 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] started
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: chroot will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: UID/GID downgrade will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:40 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:41 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:25:46 KALI06 NetworkManager[635]: [1492822546.9594] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:49 KALI06 anacron[2796]: Job `cron.weekly’ started
Apr 22 06:25:49 KALI06 anacron[4252]: Updated timestamp for job `cron.weekly’ to 2017-04-22
Apr 22 06:25:54 KALI06 NetworkManager[635]: [1492822554.0139] keyfile: update /etc/NetworkManager/system-connections/VyprVPN OpenVPN (f9719cb8
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 anacron[2796]: Job `cron.weekly’ terminated
Apr 22 06:25:57 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:59 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:26:04 KALI06 NetworkManager[635]: [1492822564.1809] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4803] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242]: send SIGTERM
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] wait for 1 openvpn processes to terminate…
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: ERROR: could not read Auth username/password/ok/string from management interface
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: Exiting due to fatal error
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] exited with error code 1
…skipping…
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: library versions: OpenSSL 1.0.2k 26 Jan 2017, LZO 2.08
Apr 22 06:25:34 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] started
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 NetworkManager[635]: [1492822534.3390] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:34 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: chroot will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:36 KALI06 nm-openvpn[4242]: NOTE: UID/GID downgrade will be delayed because of –client, –pull, or –up-delay
Apr 22 06:25:40 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:41 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:41 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:25:46 KALI06 NetworkManager[635]: [1492822546.9594] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:25:49 KALI06 anacron[2796]: Job `cron.weekly’ started
Apr 22 06:25:49 KALI06 anacron[4252]: Updated timestamp for job `cron.weekly’ to 2017-04-22
Apr 22 06:25:54 KALI06 NetworkManager[635]: [1492822554.0139] keyfile: update /etc/NetworkManager/system-connections/VyprVPN OpenVPN (f9719cb8
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: NOTE: the current –script-security setting may allow this configuration to call user-defined scripts
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: TCP/UDP: Preserving recently used remote address: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link local: (not bound)
Apr 22 06:25:54 KALI06 nm-openvpn[4242]: UDP link remote: [AF_INET]209.99.61.33:1194
Apr 22 06:25:54 KALI06 anacron[2796]: Job `cron.weekly’ terminated
Apr 22 06:25:57 KALI06 nm-openvpn[4242]: [us3.vyprvpn.com] Peer Connection Initiated with [AF_INET]209.99.61.33:1194
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: AUTH: Received control message: AUTH_FAILED
Apr 22 06:25:59 KALI06 nm-openvpn[4242]: SIGUSR1[soft,auth-failure] received, process restarting
Apr 22 06:25:59 KALI06 NetworkManager[635]: nm-openvpn[4239] Password verification failed
Apr 22 06:26:04 KALI06 NetworkManager[635]: [1492822564.1809] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4803] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242]: send SIGTERM
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] wait for 1 openvpn processes to terminate…
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: ERROR: could not read Auth username/password/ok/string from management interface
Apr 22 06:26:06 KALI06 nm-openvpn[4242]: Exiting due to fatal error
Apr 22 06:26:06 KALI06 NetworkManager[635]: nm-openvpn[4239] openvpn[4242] exited with error code 1
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4925] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4926] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:06 KALI06 NetworkManager[635]: [1492822566.4934] vpn-connection[0x21965d0,f9719cb8-b710-4dae-b332-44df3b0bfa37,”VyprVPN OpenVPN”,
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: DRM: resuming kernel object tree…
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: bus: MMIO write of 0000001f FAULT at 6013d4 [ IBUS ]
Apr 22 06:26:08 KALI06 kernel: nouveau 0000:08:00.0: DRM: resuming client object trees…
Apr 22 06:26:13 KALI06 kernel: ACPI Warning: \_SB.PCI0.RP05.PEGP._DSM: Argument #4 type mismatch – Found [Buffer], ACPI requires [Package] (20160108/n
Apr 22 06:26:13 KALI06 kernel: ACPI: \_SB_.PCI0.RP05.PEGP: failed to evaluate _DSM
Apr 22 06:26:13 KALI06 kernel: ACPI Warning: \_SB.PCI0.RP05.PEGP._DSM: Argument #4 type mismatch – Found [Buffer], ACPI requires [Package] (20160108/n
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: evicting buffers…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: waiting for kernel channels to go idle…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: suspending client object trees…
Apr 22 06:26:13 KALI06 kernel: nouveau 0000:08:00.0: DRM: suspending kernel object tree…
Apr 22 06:26:33 KALI06 plugin-containe[4343]: g_path_get_basename: assertion ‘file_name != NULL’ failed
Apr 22 06:27:09 KALI06 firefox-esr.desktop[4262]: 1492822629805 addons.productaddons ERROR Request failed certificate checks: [Ex
Apr 22 06:28:22 KALI06 dbus-daemon[844]: Activating via systemd: service name=’org.gnome.Terminal’ unit=’gnome-terminal-server.service’
Apr 22 06:28:22 KALI06 systemd[838]: Starting GNOME Terminal Server…
Apr 22 06:28:22 KALI06 dbus-daemon[844]: Successfully activated service ‘org.gnome.Terminal’
Apr 22 06:28:22 KALI06 systemd[838]: Started GNOME Terminal Server.
:100
Timed out waiting for device dev-disk-by\x2did-usb\x2dDell_Dell_USB_001D60EDDECCBF11E1D65AD9\x2d0:0.device.
i got this error how to fix it
Hi,
after Installing a VPN (from
Vpnbook) I cannot make a connection to internet. The installion is successful but when opening a browser I get ‘Request Certifcate ‘ errors. I have tried installing via command line and via GUI set up in network manager.
Any input appreciated.
I have this Error:
jun 05 16:15:56 kali nm-openvpn[1392]: TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
jun 05 16:15:56 kali nm-openvpn[1392]: TLS Error: TLS handshake failed
can you help me ?
thank you for your time