In this article on Hacking Tutorials we will be looking at a new penetration testing course priced at only $99,- offered by a newcomer on the block: The Virtual Hacking Labs. The Virtual Hacking Labs & Hacking Tutorials offer a full penetration testing course that includes access to an online penetration testing lab for practical training. The penetration testing lab contains 30 vulnerable machines that can be used to practice penetration testing techniques and tools in a safe way. All vulnerable machines and scenarios are based on real life scenarios as you would encounter on real company networks. After completing the courseware and the lab machines the student will have a good understanding of basic penetration testing techniques and practical experience applying these techniques.
Penetration Testing Courseware
The penetration testing course and the virtual labs are targeting both beginning and experienced penetration testers. The courseware covers subjects like enumeration, vulnerability assessments and exploitation from the ground up and teaches the student techniques that can be used to compromise machines on the lab network. More experienced penetration testers can use the lab machines on the lab network to sharpen their pentesting skills. The courseware is offered both online and offline. The online courseware is accessible from the website and contains functionality to track progress. The offline courseware is a downloadable PDF that is included with a month pass or greater.
Let’s have a look at an overview of the subjects that are covered in the online hacking course: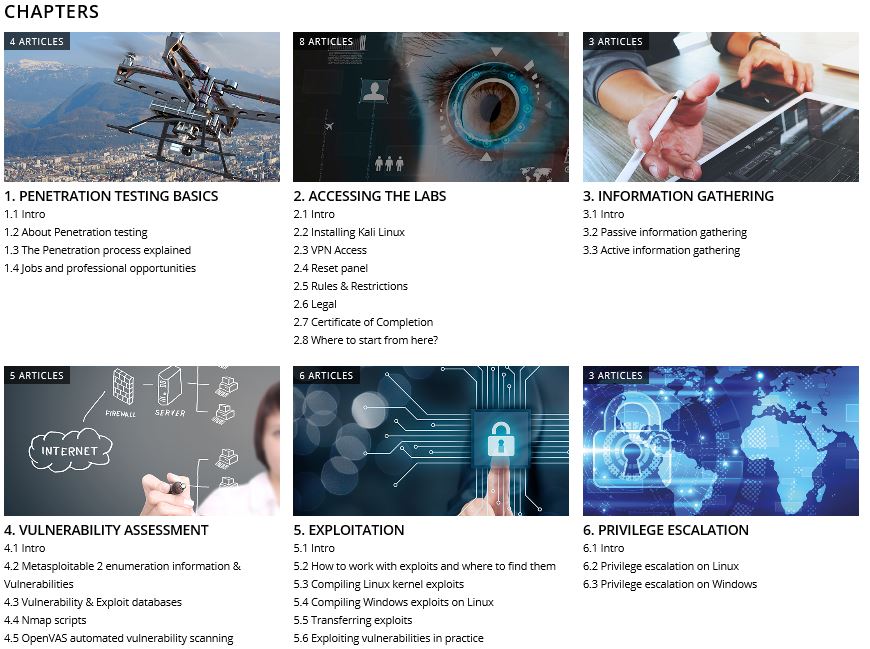
There is also a free courseware sample available that can be requested here:

Virtual Hacking Labs Network
The penetration testing lab network consists of 30 vulnerable custom hosts that are based on real life scenarios and can be accessed by connecting to the VPN. The network contains a wide range of multi purpose devices and appliances such as domain controllers, firewalls, webservers, fileservers, NAS devices and clients that are vulnerable in one or more ways. In the labs you will learn how to exploit software and services running all major operating systems such as Windows, Linux, FreeBSD and Android. All hosts on the network have been designed by the Virtual Hacking Labs to contribute to a specific learning experience. This learning experience can be anything ranging from identifying and exploiting vulnerabilities in web applications and operating systems to analysing and modifying exploit code.
The vulnerable machines are being updated on a regular basis in order to provide scenarios with recently discovered vulnerabilities.
Penetration Testing VM’s
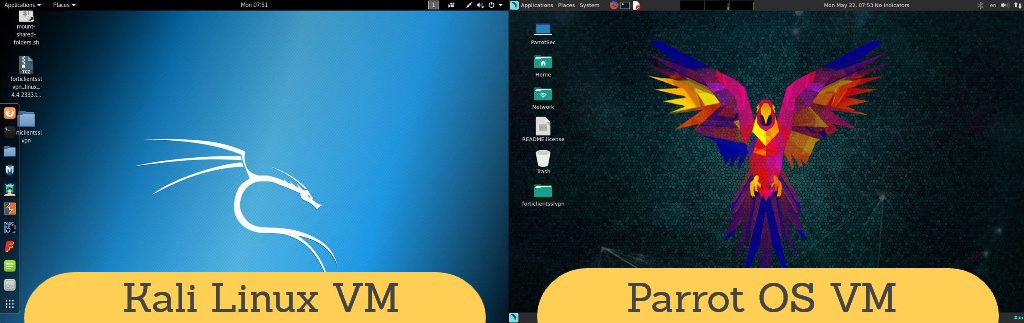
Accessing the Virtual Hacking Labs is as easy as logging in a VPN client on one of the pre-installed VM’s. The Virtual Hacking Labs offer a download for a pre-installed Kali Linux 2017.1 and Parrot OS 3.5 pentesting machine with every subscription. Both VM’s include a pre-installed VPN client so there is no need to go trough difficult installation procedures. The courseware also includes a detailed description on how to install the VM’s on VMWare Player free. Of course you can also use your own penetration testing distro to access the Virtual Hacking Labs. In this case you only need to download the client software on the VHL website.
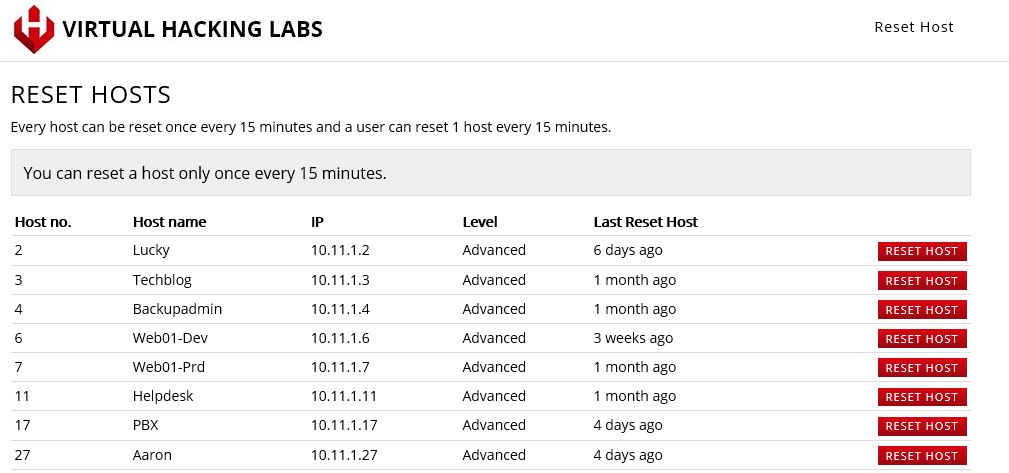
Personal Reset Panel
All students have access to a personal reset panel that can be used to reset hosts back to their original, vulnerable state. Resetting a host is especially useful when it’s left in an non-exploitable state by another student or yourself. An example of such state is a system that has crashed or became unstable because of a kernel exploit. This way every student proceeds through the course and labs without needing to wait on timed resets or administrator interference.
Certificate of Completion
Students who have compromised at least 20 machines on the lab network can request a Certificate of Completion. In order to apply for this certificate a student needs to document the exploitation process for each host and supply proof of this. To become eligible for the Virtual Hacking Labs Certificate of Completion a student needs to:
- Get administrator access on at least 20 lab machines.
- Provide documentation of the exploitation process.
- Include screenshots proving that you have administrator access to the compromised host.
- Supply the contents of key.txt files on the rooted lab machines.
When all documentation is submitted by e-mail to the VHL team, the Certificate will be issued shortly after approval of the supplied documentation.
The Virtual Hacking Labs Certificate of Completion is only available for students who have purchased a month pass or greater. The week pass does not include the certificate.
Pricing
The pricing for the penetration testing course and lab access is subscription based and priced at $99,- for 1 month access. A major pro of the subscription based model compared to a flat fee is that anyone can decide for themselves how much to spend on this course. If you are an experienced penetration tester and/or you can spend a lot of time on the course, it is possible to finish the courseware and 20 machines in a month time. If you have less time to spend or you are a beginner in the field of penetration testing, then the 3 month access pass might be a better choice. This access pass is priced at $249,- for 3 months.

If you are a very experienced penetration tester or you can spend a lot of time on the course, it is possible to finish the courseware and 20 machines in a month time. Otherwise 3 months is a better choice.
Don’t forget to check out the Virtual Hacking Labs Reviews page to see what others have to say about this penetration testing course!
What happens after signing up?
After signing up you will receive a few e-mails with the credentials to access the labs and information about where to find the VM downloads and courseware. After downloading the VM you can boot it with VMware Player Free and use the pre-installed VPN client to connect to the labs. If you purchased a month pass or greater you can also download the courseware from you user panel. The online courseware will be available on the course page on the website.

