In this tutorial we will demonstrate how to install Metasploitable 3 in a Windows 10 environment using Vagrant, Packer and Virtualbox. So far we did a number of tutorials on hacking the Metasploitable 2 Linux machine on Hacking Tutorials. We’ve demonstrated how to install Metasploitable 2, how to enumerate it and perform a vulnerability assessment, and finally how to exploit it. As like many vulnerable machines that are for download Metasploitable 2 is a Linux machine. Because of strict licensing policies it a challenge to provide vulnerable Windows machines without breaking any licensing rules. Unfortunately you cannot just download the VM but you have to configure it yourself using a few tools and a Windows 2008 evaluation copy which is downloaded from the Microsoft website.
The installation process is pretty straightforward and should not cause too much trouble when the right dependencies are installed. The biggest part of the installation process is handled automatically by the install scripts. The full installation procedure might take a couple hours in total, be prepared to spend time on the installation of Metasploitable 3.
Before we can continue with the installation procedure we need to install a few dependencies:
- Packer v1.0.0: https://www.packer.io/downloads.html
- Vagrant 1.9.1: https://releases.hashicorp.com/vagrant/1.9.1/
- Vagrant Reload Plugin v0.0.1: https://github.com/aidanns/vagrant-reload
- Virtualbox 5.1.14: https://www.virtualbox.org/wiki/Downloads
In order to avoid (a lot of) trouble it is recommended to download the exact version as mentioned above. The success rate of the installation script depends greatly on the build environment. For your reference, we’re building the Metasploitable 3 machine on Windows 10 Enterprise x64 Build 15063.
Before we can build the VM we have to install Vagrant and Virtualbox using the downloaded installation files. We will not demonstrate the installation procedure for this software as it’s very straightforward and only involves clicking ‘next’ a couple times. Next we need to install the Vagrant reload plugin and we need to download Packer.
Install Vagrant reload plugin
Change the directory on the command line to the directory where you have downloaded and unpacked the Vagrant Reload plugin. Then run the following command to install the plugin:
vagrant plugin install vagrant-reload
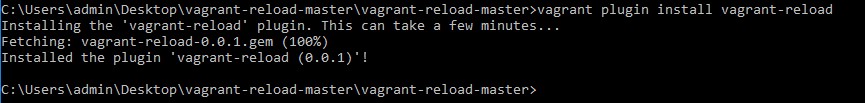
Now that we have installed the Vagrant reload plugin we can continue with downloading Packer.
Download Packer
The next step is to download Packer from the following download page:
https://www.packer.io/downloads.html
Download the latest version of Packer and unpack it the Metasploitable 3 master directory. Storing the Packer binary in the Metasploitable 3 directory allows us to easily execute it to setup the VM without setting up system variables or using full paths to the binary. After copying the Packer file to the Metasploitable 3 directory we can start setting up the virtual machine.
Creating the Metasploitable 3 VM
Now that we have all pre-requisites installed we can use Packer to setup the Virtual Machine in Virtualbox. Move the command line to the Metasploitable 3 location and run the following command from an elevated command line:
packer build windows_2008_r2.json
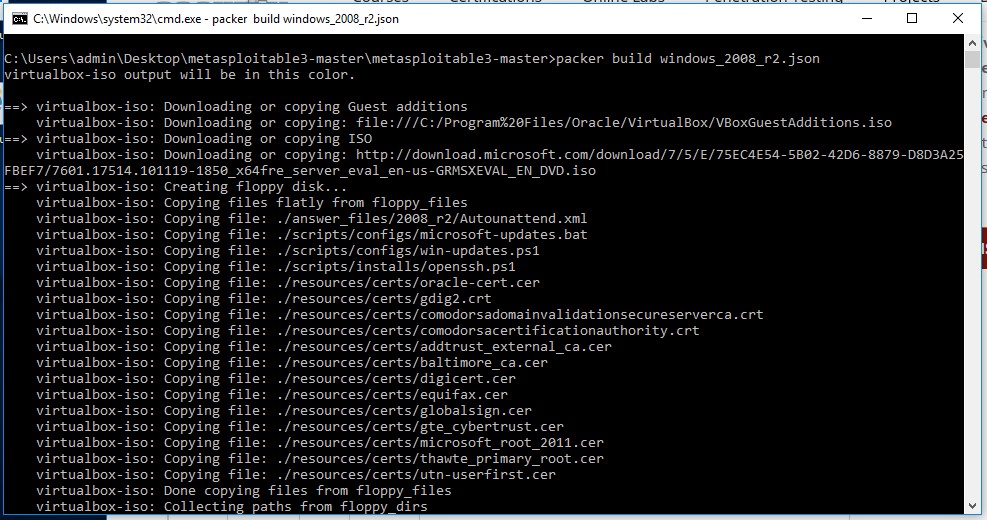
This command will take a while to complete because first it will download a Windows 2008 evaluation copy from the Microsoft website. When the download is finished, the script will continue to setup the virtual machine in Virtualbox and install Windows 2008 on the virtual machine. The entire process will take anywhere from 30-60 minutes. This depends on the configuration of your host machine and the speed of your internet connection. When the script is finished the output looks as following:
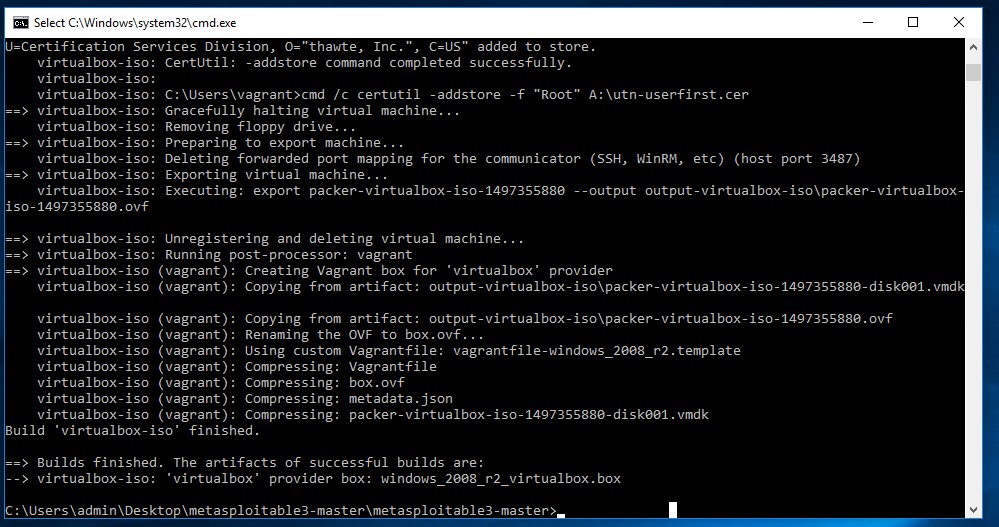
When the script is finished run the following command:
vagrant box add windows_2008_r2_virtualbox.box –name=metasploitable3
Note: Use 2 dashes for the name parameter here.
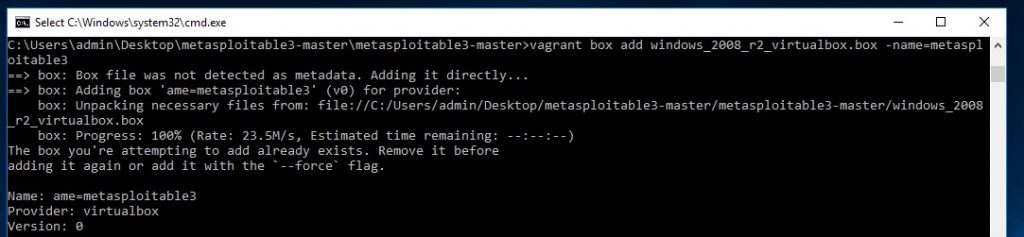
Finally we have to run the one more command to have Vagrant execute the scripts that install the vulnerable software on the Windows server 2008 virtual machine. Run the following command and expect to wait another 15-30 minutes until completion:
vagrant up
This will conclude the installation of Metasploitable 3 and you should be able to start the VM within Virtualbox.
Metasploitable 3 installation errors with Vagrant
The Metasploitable 3 setup process is a bit tricky and prone to errors related to specific versions of the prerequisites. Most errors I faced while writing this tutorial were avoided by using the versions of Vagrant, Packer & Virtualbox mentioned earlier in this tutorial. Especially the latest version of Virtualbox resulted in many errors after issuing the vagrant up command.
During the installation of the vulnerable software you might get an error related to the virtual machine state: “The guest machine entered an invalid state while waiting for it to boot.”. When this happens reboot the virtual machine and run the vagrant up command again.
Another error that may occur during the installation of vulnerable software is the following: “chocolatey is not recognized as an internal or external command”. The error didn’t only apply to Chocolatey but also some other scripts. To get rid of this error I’ve added the following directory to the Path variable:
C:\Users\admin\Desktop\metasploitable-3-master\metasploitable-3-master\scripts\installs\
This will make all the scripts in this directory accessible without using a full path. Eventually I had to run the ‘Vagrant up’ command several times before it finished without errors.
Running Kali Linux VM on the same host
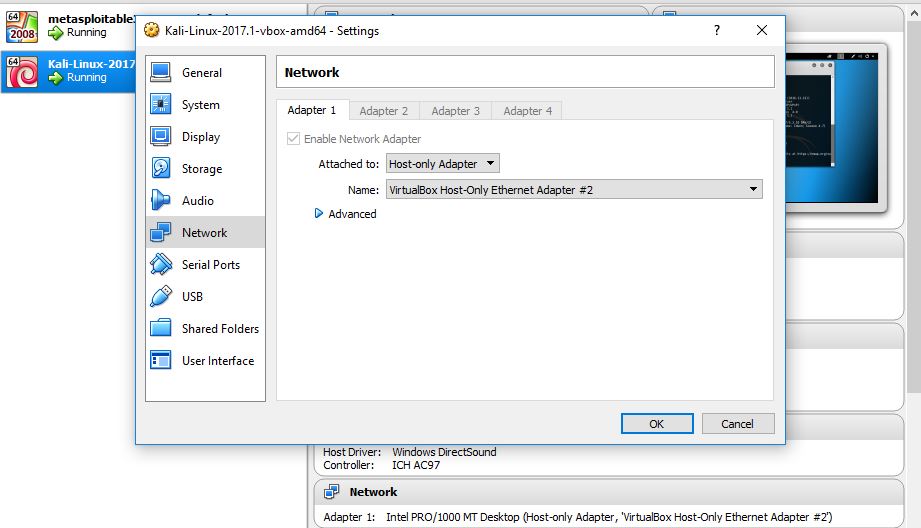
If you’re running your Kali Linux virtual machine in Virtualbox on the same host you have to make sure that you set the correct network settings. Otherwise you won’t be able to connect to the Metasploitable 3 machine from your Kali Linux attack box. You’re not required to alter the network settings for the Metasploitable 3 machine, only for the Kali Linux VM:
Booting Metasploitable 3
Now that we’ve completed the installation procedure for Metasploitable 2 we are ready to boot in in Virtualbox. The default username for the virtual machine is “vagrant” with password “vagrant”. Even though the installation process produced quiet some errors there were none that we couldn’t fix quickly (Google is your friend!). I must say that the developers of Metasploitable 3 did a great job on the installation procedure and providing a vulnerable Windows machine to the public.
In the next tutorials we will be enumerating and exploiting Metasploitable 3 and create a full walkthrough.
Do you prefer immediate access to a full virtual penetration testing environment with 30 vulnerable machines, courseware and a Certificate for less than $99,- USD? Check out: The Virtual Hacking Labs.


28 Comments
Hey Man, you have a typo in your syntax above – which is also reflected in your screen shot.
vagrant box add windows_2008_r2_virtualbox.box –name=metasploitable3
should be
vagrant box add windows_2008_r2_virtualbox.box –-name metasploitable3
Otherwise you don’t get a metasploit3.box and the vagrant up command fails.
Other than that, tidy like.
Hi Rob!
Thanks for your comment! You are right, the command in the screenshot is wrong and this probably caused those errors, thanks for pointing that out!
The command in the tutorial should now display 2 hyphens instead of an em-dash.
Best regards,
Hacking Tutorials
All i get is that vagrant is not a recognized as an internal or external command.
I am in the same directory i cannot even see a vagrant file…
What am i missing?
Use double dash before the name option as following:
vagrant box add windows_2008_r2_virtualbox.box (Use double dash here ->)–name=metasploitable3
I am setting it up on VMWare Workstation Pro (Uni got free license for students). The kali box and the Metasploitable 3 run on same host. But Kali can’t find the metasploitable 3 machine using nmap. What network settings I need to do?
Build ‘vmware-iso’ errored: Failed creating VMware driver: Unable to initialize any driver for this platform. The errors
from each driver are shown below. Please fix at least one driver
to continue:
* VMware application not found:
* VMware application not found:
* VMware application not found:
* VMware application not found:
Hey,
i installed all and packer is running too, but the command:
packer build windows_2008_r2.json
isn’t running. (Failed to parse template: open windows_2008_r2.json)
What am i doing wrong?
Hi,
Can you post the full error? Does it say that it cannot find the json file?
how do you resolve this issue ? the full error says “Failed to parse template: open windows_2008_r2.json: The system cannot find the file specified.”
Yes, I’m getting this error, too. It appears as though as we need to acquire this .json file from somewhere, but the instructions don’t mention anything about it. How do we proceed without it?
Can you verify if the the windows_2008_r2.json file is in the directory where you execute the packer command?
I’m also getting this and was looking for the windows_2008_r2.json but haven’t found it yet. Will let you know if i get this to work.
Hi i went through all the steps on creating a Metasploitable 3 and no success.. the vm fails.. I have tried this process at least 4 times and no luck. Virtualbox fails to load
Hi, What errors are you getting? Maybe we can help…
Hi
thank you for reaching back out –
All steps seemed to go without problem until I go to start the virtual machine. I get two VirtualBox Errors that say: Failed to open a session for the virtual machine metasploitable3_default_1481161588202_8101. The VM session was aborted. Result Code: E_FAIL (0x80004005) Component: SessionMachine Interface: ISession {7844aa05-b02e-4cdd-a04f-ade4a762e6b7} AND Failed to open a session for the virtual machine metasploitable3_default_1481161588202_8101. Callee RC: E_FAIL (0x80004005) Any idea what could have went wrong? All steps seemed to go well I had no errors until this point.
PS C:\Users\MickeyM\Downloads\metasploitable3-master\metasploitable3-master> vagrant up win2k8
Bringing machine ‘win2k8’ up with ‘virtualbox’ provider…
==> win2k8: Clearing any previously set forwarded ports…
==> win2k8: Clearing any previously set network interfaces…
==> win2k8: Preparing network interfaces based on configuration…
win2k8: Adapter 1: nat
win2k8: Adapter 2: hostonly
==> win2k8: Forwarding ports…
win2k8: 3389 (guest) => 3389 (host) (adapter 1)
win2k8: 22 (guest) => 2222 (host) (adapter 1)
win2k8: 5985 (guest) => 55985 (host) (adapter 1)
win2k8: 5986 (guest) => 55986 (host) (adapter 1)
==> win2k8: Running ‘pre-boot’ VM customizations…
==> win2k8: Booting VM…
There was an error while executing `VBoxManage`, a CLI used by Vagrant
for controlling VirtualBox. The command and stderr is shown below.
Command: [“startvm”, “cd8317d0-4538-4e52-81bf-53a5504f69a5”, “–type”, “headless”]
Stderr: VBoxManage.exe: error: VT-x is not available (VERR_VMX_NO_VMX)
VBoxManage.exe: error: Details: code E_FAIL (0x80004005), component ConsoleWrap, interface IConsole
PS C:\Users\MickeyM\Downloads\metasploitable3-master\metasploitable3-master>
This is where it goes wrong:
Stderr: VBoxManage.exe: error: VT-x is not available (VERR_VMX_NO_VMX)
Do you maybe have Hyper-V running? This may cause errors when running VirtualBox:
https://blogs.technet.microsoft.com/gmarchetti/2008/12/07/turning-hyper-v-on-and-off/
Also make sure that Intel VT virtualization is turned on in BIOS settings and restart the machine.
I did not have the hyper-v turned on in windows features – i just verified again and it is not on. also the VT virtualization is turned on in the BIOS settings and still getting having the same issue
If you go to the VM settings for Metasploitable 3 in Virtualbox -> System -> Acceleration -> Enable VT-x/AMD-V, is this option enabled?
Hey, i got this ERROR while the installation process, and all the dependencies are installed as you recommended to download the exact version as mentioned above.
packer build windows_2008_r2.json
…
virtualbox-iso: Executing custom VBoxManage commands…
virtualbox-iso: Executing: modifyvm metasploitable3-win2k8 –memory 4096
virtualbox-iso: Executing: modifyvm metasploitable3-win2k8 –cpus 2
==> virtualbox-iso: Starting the virtual machine…
==> virtualbox-iso: Error starting VM: VBoxManage error: VBoxManage.exe: error: The virtual machine ‘metasploitable3-win2k8’ has terminated unexpectedly during startup with exit code 1 (0x1). More details may be available in ‘C:\Users\sec-pen\VirtualBox VMs\metasploitable3-win2k8\Logs\VBoxHardening.log’
==> virtualbox-iso: VBoxManage.exe: error: Details: code E_FAIL (0x80004005), component MachineWrap, interface IMachine
==> virtualbox-iso: Unregistering and deleting virtual machine…
==> virtualbox-iso: Deleting output directory…
Build ‘virtualbox-iso’ errored: Error starting VM: VBoxManage error: VBoxManage.exe: error: The virtual machine ‘metasploitable3-win2k8’ has terminated unexpectedly during startup with exit code 1 (0x1). More details may be available in ‘C:\Users\sec-pen\VirtualBox VMs\metasploitable3-win2k8\Logs\VBoxHardening.log’
VBoxManage.exe: error: Details: code E_FAIL (0x80004005), component MachineWrap, interface IMachine
==> Some builds didn’t complete successfully and had errors:
–> vmware-iso: Error creating disk: VMware error: Failed to initialize logging, can’t open C:\Users\sec-pen\AppData\Local\Temp\vmware-sec-pen\vdiskmanager.log for writing.
–> virtualbox-iso: Error starting VM: VBoxManage error: VBoxManage.exe: error: The virtual machine ‘metasploitable3-win2k8’ has terminated unexpectedly during startup with exit code 1 (0x1). More details may be available in ‘C:\Users\sec-pen\VirtualBox VMs\metasploitable3-win2k8\Logs\VBoxHardening.log’
VBoxManage.exe: error: Details: code E_FAIL (0x80004005), component MachineWrap, interface IMachine
==> Builds finished but no artifacts were created.
THANKS FOR YOUR BESTS
Hi, Have you checked the log files the error is referring to?
I get an error when i start the vm after the last ‘vagrant up win2k8’ command.
Result Code:
E_FAIL (0x80004005)
Component:
SessionMachine
Interface:
ISession {7844aa05-b02e-4cdd-a04f-ade4a762e6b7}
Hi guys,
Can someone explain me why my windows defender detects a Trojan? the package has been downloaded from the git hub
Hi,
Thanks for you step by step instruction of setting up Metasploitable 3.
I have been onto it since the last 10 hours. All steps completed ok. However, since last few hours, I am now at :
Progress: Downloading boxstrater.bootstrapper 2.12.0… 100%
It does not seem to go beyond it.
Please can you let me know if that’s ok or not.
Thanks & Regards,
Faisal
how do i install the application and services with their respective ports in my metasploitable 3 since it lacks them as stated in their wiki github page
Elasticsearch Install Error
Script uses file metasploitable3-master\scripts\installs/install_elasticsearch.bat
–>
powershell -Command “(New-Object System.Net.WebClient).DownloadFile(‘http://repo1.maven.org/maven2/org/elasticsearch/elasticsearch/1.1.1/elasticsearch-1.1.1.zip’, ‘C:\Windows\Temp\elasticsearch-1.1.1.zip’)” <NUL
[…]
<–
URL results in 501 http not allowed (or similar)
replace with https:// to fix this
Downloading Elasticsearch needs an upgrade:
http download throws 501-Error.
metasploitable3-master\scripts\installs\install_elasticsearch.bat
first line has to be changed using HTTPS/TLS1.2:
powershell -Command “[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; (New-Object System.Net.WebClient).DownloadFile(‘https://repo1.maven.org/maven2/org/elasticsearch/elasticsearch/1.1.1/elasticsearch-1.1.1.zip’, ‘C:\Windows\Temp\elasticsearch-1.1.1.zip’)” 0<NUL
Hello,
at the step “Install Vagrant reload plugin”, Windows tells me that the word “vagrant” is not recognized. Do I need to install something ?
Thank you for your help