Questions about if a certain Wifi adapter is compatible with the Aircrack-ng suite or what Wifi card is capable of packet injection and operating monitoring mode are commonly asked at discussion boards and social media. A Wifi adapter that is capable of packet injection and monitoring mode is trivial and important functionality to be successful in Wifi hacking. Wireless packet injection is spoofing packets on a network to appear as if they are part of the regular network communication stream. Packet injection allows to intercept, disrupt and manipulate network communication. An example of this is sending a deauthentication message from an unknown party outside the network to a connected client as if it was send by the wireless router. This will result in the client disconnecting from the router. Monitoring mode is one of the six modes a Wifi card can operate in which allows you to capture network packets without having to associate with the access point.
If you are looking to buy a Wifi card which is capable of packet injection using the Aircrack-NG suite you can have a look at the following list with supported Wifi adapters:
http://www.aircrack-ng.org/doku.php?id=compatible_cards
Wifi adapter packet injection test
Performing an Wifi adapter packet injection test to see whether your Wifi adapter is capable of injection can be done easily with Aireplay-ng. Aireplay-ng is great tool to generate traffic for cracking WEP and WPA keys. Another great feature is the Deauthentication option which we have used a lot through the Wifi hacking tutorials like:
- How to hack UPC wireless networks and other WLAN pt 1
- How to hack a TP link WR841N router wireless network
First we need to put the Wifi adapter in Monitoring mode using the following command:
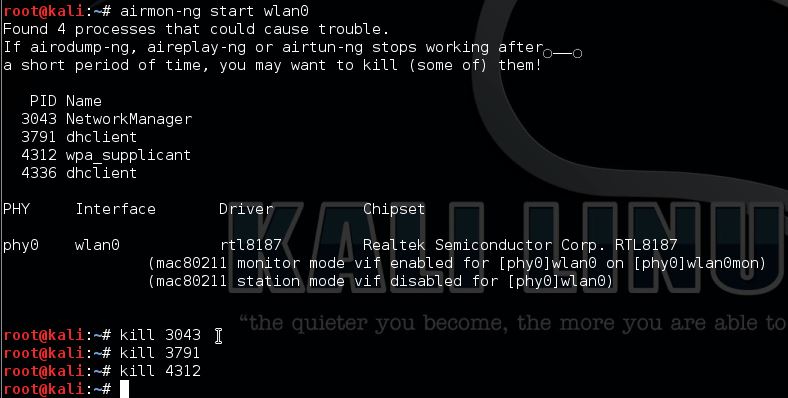
airmon-ng start wlan0
For anyone getting errors in Kali Linux 2.0: read this post
If necessary kill the processes Kali is complaining about:
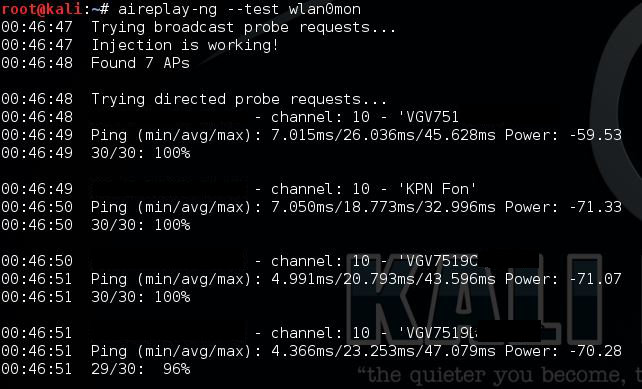
Testing if your Wifi adapter support packet injection can be done using the following command:
aireplay-ng –test wlan0mon
Packet Injection is working for this card!
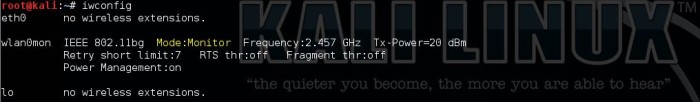
In Kali Linux ‘iwconfig’ will show you the operating mode of your Wifi card:
Wifi adapter packet injection video tutorial
Thanks for watching and please subscribe to our YouTube channel for more hacking tutorials :)


10 Comments
When I run the test I’m getting ;
Invalid tods filter. [0,1]
Is this the tell tale sign that my card is unsupported?
Use aireplay-ng –test wlan0mon
Sorry I mean use:
aireplay-ng –test wlan0mon
“–test” not “-test”
what is the difference between those two? because i see the same thing -test
One is with a single dash and the other is with double dash but WordPress formatting automatically converts a double dash to a single dash.
Hi,
If I have that, I can’t do injection and crack wifi, isn’t it ? :(
root@parrot:~# airmon-ng start wlan0
PHY Interface Driver Chipset
phy0 wlan0mon iwlwifi Intel Corporation Wireless 7265 (rev 59)
root@parrot:~# aireplay-ng –test wlan0mon
09:51:38 Trying broadcast probe requests…
09:51:40 No Answer…
09:51:40 Found 0 APs
Thank you
regards
Same problem . my Wi-Fi driver Qualcomm Atheros QCA9377 .when I try aireplay-ng –test wlp1s0 it gives no answer found 0 APs
When i try it give No answer
That mean my card is not injectable. plz tell me
very informative, i appreciate your patients.It must be very difficult for a man of your vast knowledge to break down the information so students such as i, a mere mortal can understand. who would of ever thought that the word processor would change a double hyphen back to a single.so much to learn and as a mortal i only have a lifetime to learn it.