In this tutorial we will be looking at how to bypass MAC filtering on a wireless network. MAC filtering, or MAC white- or blacklisting, is often used as a security measure to prevent non-whitelisted or blacklisted MAC addresses from connecting to the wireless network. MAC Address stands for media access control address and is a unique identifier assigned to your network interface. With MAC filtering you can specify MAC addresses which are allowed or not allowed to connect to the network. For many occasions MAC filtering can be sufficient as a security measure but in others it is certainly not. MAC filtering is totally useless to protect company networks and data or to prevent networks from being hacked over WiFi because is it so easy to bypass. When MAC filtering is in place you can easily determine whitelisted MAC addresses by scanning for connected clients using a tool like airodump-ng. In this case we can assume that every connected MAC address is part of the whitelist or not on the black list.
In this tutorial we will be bypass MAC filtering on a TP link WR-841N router by spoofing the MAC address of a connected client. The connected client’s MAC address is whitelisted, otherwise it would not have been able to connect to the wireless network. We will put our wifi adapter in monitoring mode and retrieve the MAC address of connected clients with Airodump-NG on Kali Linux. Then we will be using the Macchanger tool to spoof our MAC address, bypass MAC filtering and connect to the wireless network. Hacking the WiFi network password is outside the scope of this tutorial. You can have a look at the following WiFi hacking tutorials and tools to learn how to retrieve the password (and prevent this from happening):
- The Top 10 Wifi Hacking Tools in Kali Linux
- Pixie Dust Attack WPS in Kali Linux with Reaver
- How to hack a TP link WR841N router wireless network
MAC filtering settings
First we will be configuring the MAC filtering functionality in the router settings. We will be adding one client to the whitelist which will be our connected client:
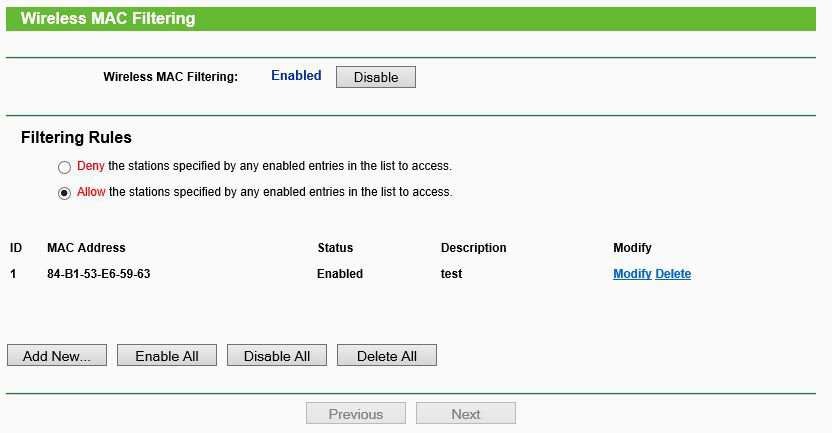
Let’s try to connect from another client in Kali Linux 2.0:
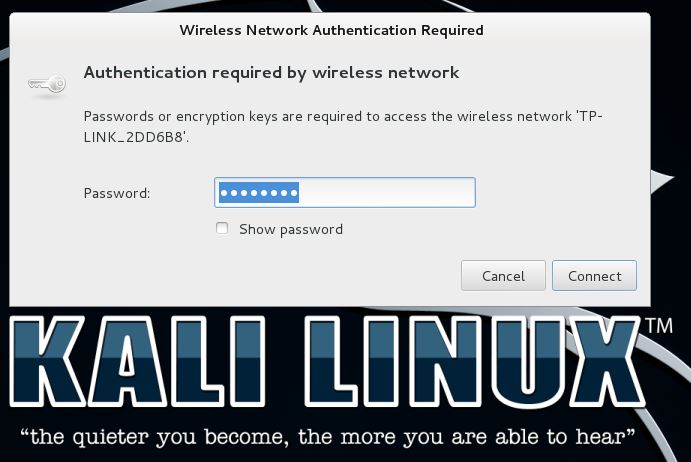
Even if we use the right password is does not allow us to connect to the wireless network. We end up in an endless loop without authentication. This tells us the MAC filtering is active and working like a charm.
Bypass MAC Filtering
First we will have to put our WiFi adapter in monitoring mode using Airmon-ng and kill all the processes Kali Linux is complaining about:
airmon-ng start wlan0
kill [pid]
Then we launch Airodump-ng to locate the wireless network and the connected client(s) using the following command:
airodump-ng –c [channel]–bssid [target router MAC Address]–i wlan0mon
Airodump-ng now shows us a list of all connected clients at the bottom of the terminal. The second column lists the MAC Addresses of the connected client which we will be spoofing in order to authenticate with the wireless network.
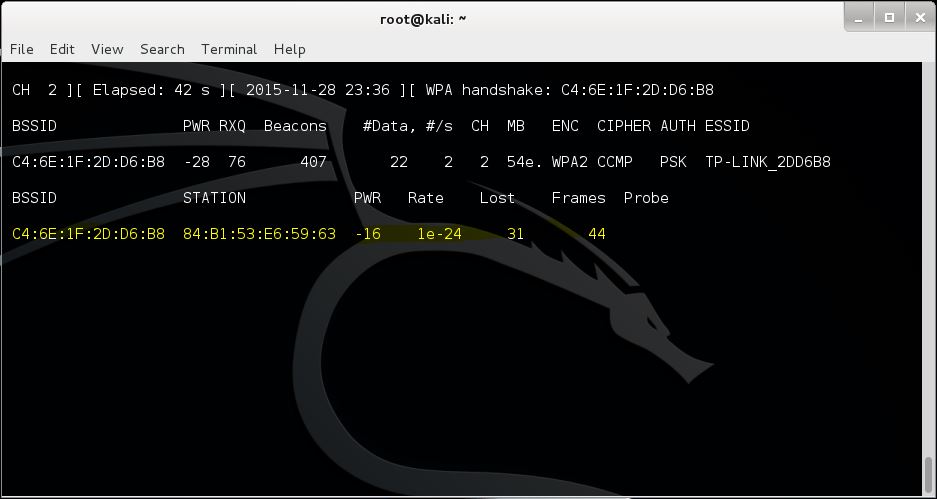
Spoofing the MAC Address with Macchanger
Now that we know a MAC address that is whitelisted in the TP Link router settings we can use it to spoof our own MAC address in order to authenticate with the network. Let’s spoof the MAC address of your wireless adapter but first we take need to take down the monitoring interface wlan0mon and the wlan0 interface in order to change the MAC address. We can do this by using the following command:
airmon-ng stop wlan0mon
Now we take down the wireless interface who’s MAC address we want to spoof with the following command:
ifconfig wlan0 down
Now we can use Macchanger to change the MAC address:
macchanger -m [New MAC Address] wlan0
And bring it up again:
ifconfig wlan0 up
Now that we have changed the MAC address of our wireless adapter to a whitelisted MAC address in the router we can try to authenticate with the network and see if we’re able to connect:
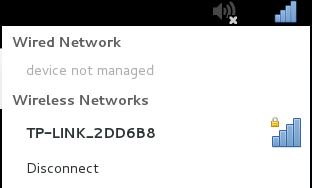
As you can see we have managed to connect to the wireless network using a spoofed MAC address of a connected client. This tutorial shows us that it was extremely easy to bypass MAC filtering on a wireless network and that MAC filtering is generally useless to protect your network from hackers.
Hacking Courses on Udemy
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques

Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.

11 Comments
can you give me the link of the wifi hacker and macchanger so that i can download them
When ever I type
airodump-ng –c [channel]–bssid [target router MAC Address]–i wlan0mon
its replying with
“airodump-ng –help” for help.
what to do now?
Are you using double dash (–) for the bssid parameter?
airodump-ng -c [channel] –bssid [target router mac address] -i wlan0mon
there is double (-) before bssid.
like this –bssid.
Sir
Add space after – ng
Two dashes (–) before bssid
You have to write as below
Airodump-ng – c [channel] – – bssid (MAC address) – w (choose file name) wlan0mon
macchanger is native on Kali Linux
this method does not work any more with new devices due the auth/assoc mechanism got imcomplete because a device with the white-listed mac is already connected.
Try deauthing it🤔
Network drivers didn’t actually change to the new MAC!!!
I am getting this error, I need help!
I had this when I was just changing the WiFi Mac address using my Mac book. Basically, turn off your WiFi completely, then change it, then turn it on and it should change the MAC Address.
It change MAC to whose MAC address?9