Uniscan is a simple but great tool for Remote File Include, Local File Include and Remote Command Execution vulnerability scanner. In this tutorial we will be exploring the webserver fingerprinting functionality in Uniscan on Kali Linux. The webserver fingerprinting functionality in Uniscan peforms a ping, traceroute, NS lookup, OS detection and service scan with Nmap on the specified target.
Uniscan Webserver fingerprinting Tutorial
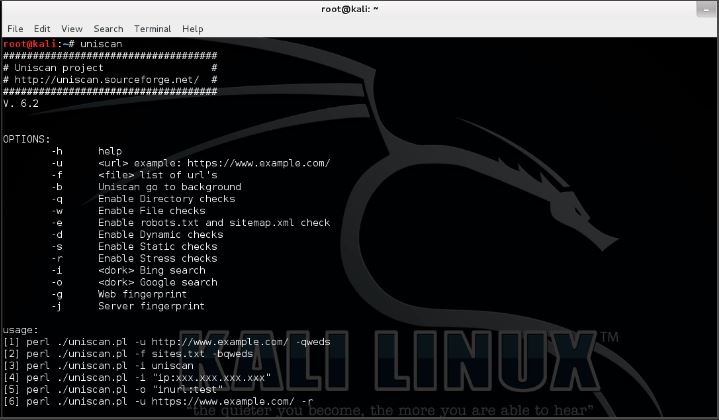
Let’s start with opening a terminal and run Uniscan with the following command to get an overview of options:
uniscan
We will be running Uniscan again with the -j Server fingerprint flag on a specified target using the following command (this will take a little while to finish):
uniscan -u [target]-j
As mentioned earlier, Uniscan will perform a ping, traceroute, NS lookup and Nmap OS & Service scan. From which in particular the Nmap scans take a little while to finish. In the meantime we will be looking at the different scans in general and what they do:
Ping
The name ping comes from sonor terminology which uses sound and echo’s to detect objects underwater. As a network utility a Ping is used to test the reachability of a specified host. By sending and ICMP echo request packet to the specified host and waiting for a reply the roundtrip time can be measured and packet loss and reception will be calculated.
Traceroute
A trace route is a diagnostic tool for displaying the route and measuring transit delays of packets across an IP network. The path of the route is recorded together with the round-trip times from each successive host in the route. Traceroute continues unless all sent packets are lost more than twice, this means a loss of connection.
NS Lookup
NS Lookup stands for Name Server Lookup and is used to obtain the domain name or the IP address or for any other specific DNS record.
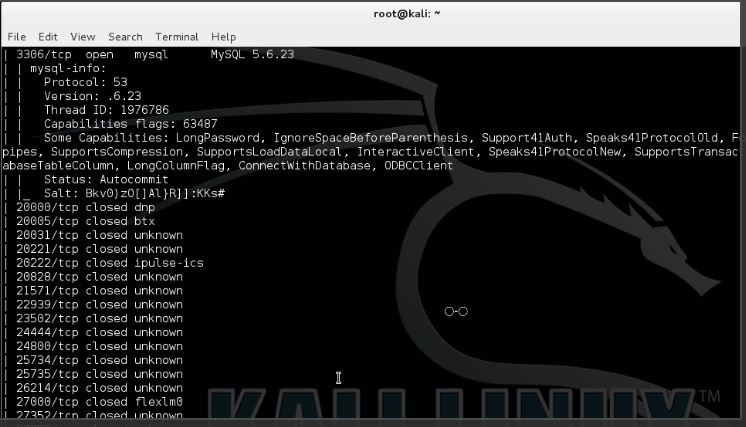
Nmap OS detection & Service scan
The Nmap OS detection scan returns the operating system of the specified host and the service scan does scan for ports and relates them to known services with the version number if available.
More information about the service scan can be read here.
When the scan is finished you can scroll back for the details Uniscan returned during the webserver fingerprinting scan:
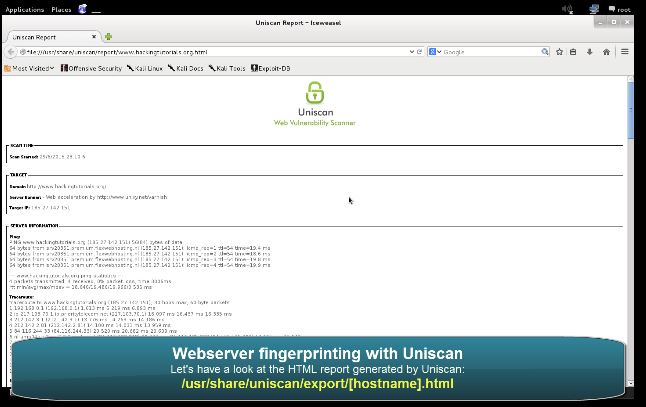
Another great feature of Uniscan is the option to export the results as a HTML page. The html page is stored at the following location (or click the link from the terminal):
/usr/share/uniscan/export/[hostname].html
In Kali Linux 2.0 the correct path to the report is:
/usr/share/uniscan/report
In the upcoming tutorials we will be exploring more functions in Uniscan.
Uniscan Video Tutorial
Thanks for watching and please subscribe to my YouTube channel for more hacking tutorials :)

If you’re interested in learning more about web penetration testing you can follow any of these online courses:
Online Hacking Courses
Web Penetration Tester
You will learn hacking tools, methodologies and techniques. This is a both practical and theoretical step-by-step course. Read more…

How to be an Independent security researcher
If you are a web developer, Bug Hunter or any it security researcher then this course will be very help full.
Read more…


2 Comments
In Kali 2.0 the correct path is:
/usr/share/uniscan/report
Thanks for commenting, I’ve added the correct filepath in the tutorial :)