In the upcoming 6 hacking tutorials we will be talking about basic malware analysis and we will start with discussing the many different Basic Malware Analysis Tools which are available. A Malware Analyst is someone highly skilled in reverse engineering malware to get a deep understanding about what a certain piece of malware does and how it does it. To become a malware analyst it is important to have a good understanding of operating systems, software, networking, programming in general, malware in general and assembly language. Assembly language is the low level programming code between the high level programming code and the machine instructions. In other words: it translates the high level language into machine instructions which will be processed by your computers hardware.
In this tutorial we will be looking at simple but popular tools for basic static malware analysis like: PEiD to detect packers, Dependency Walker to view dynamically linked functions, Resource Hacker to view the malware’s resources and PEview and FileAlyzer to examine the PE file headers and sections. These tools are used for basic static malware analysis to try to determine the kind of malware and it’s function without actually running the malware. Running and analysing the malware will be covered in laters tutorials. After this we will be looking at the malware analysis advanced tools available for advanced static analysis and advanced dynamic malware analysis in the next article: Dynamic Malware Analysis Tools. Note that we will be discussing the tools in general first and get into detailed tutorials later. In the upcoming tutorials we will be using them on sample malware in detailed step-by-step hacking tutorials.
For now the Malware Analysis Tutorials will be divided in 6 subjects and will be released the upcoming few weeks:
- Basic Malware Analysis Tools
- Dynamic Malware Analysis Tools
- Malware Types Explained
- Basic Malware Analysis
- Advanced Static Malware Analysis
- Advanced Dynamic Malware Analysis
Basic Malware Analysis Tools
As promised we’ll be looking at the following basic malware analysis tool: PEiD, Dependency Walker, Resource Hacker, PEview and FileAlyzer. For your convenience we will supply a download link for the tools as well so you can get your malware analysis toolbox ready for the upcoming tutorials. Be sure to subscribe to our newsletter as we will be updating this list and our toolbox along the upcoming tutorials.
PEiD
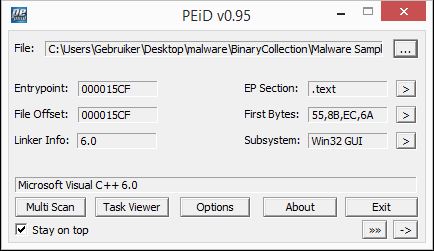
PEiD is a small application which is used to detect common packers, cryptors and compilers. Malware writers often attempt to pack or obfuscate their malware to make it harder to detect and to analyse. The current version of PEiD can detect over 470 different signatures in PE files which are loaded from a txt file called userdb. The official PEiD website is not active anymore but you can download PEiD-0.95-20081103 from Hacking Tutorials using the following download link: PEiD-0.95-20081103.zip (645772 downloads )
You need to replace the userdb.txt file with the following file to add the signatures; [Download not found]
Dependency Walker
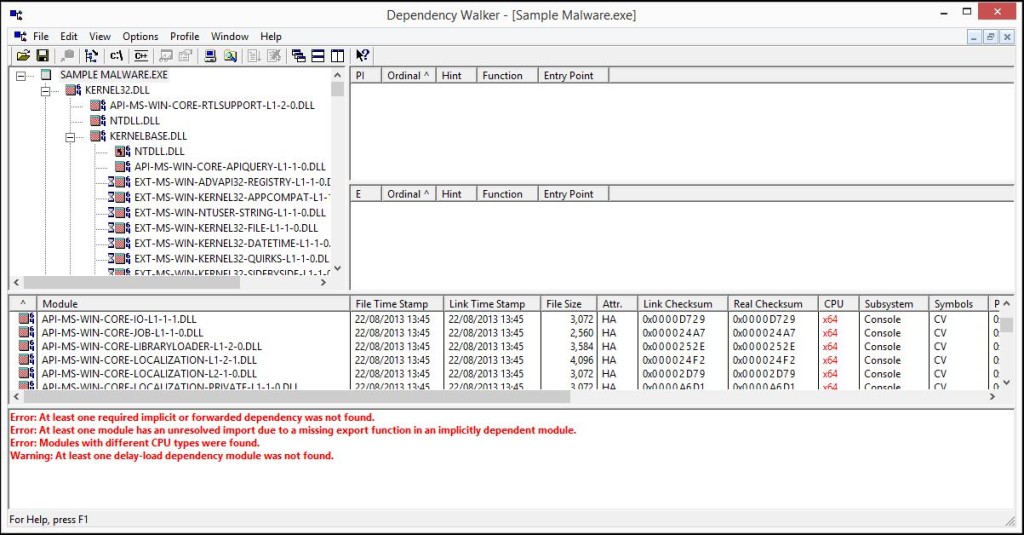
Another great basic malware analysis tool is Dependency Walker. Dependency Walter is a free application which can be used to scan 32 and 64 bit Windows modules (.exe, .dll, .ocx, etc.) and is used to list all the imported and exported functions of a module. Dependency Walker also displays the dependencies of the file which will result in a minimum set of required files. Depency Walker also displays detailed information about those files including the filepath, version number, machine type, debug information etc.
Dependency Walker can be downloaded here.
Resource Hacker
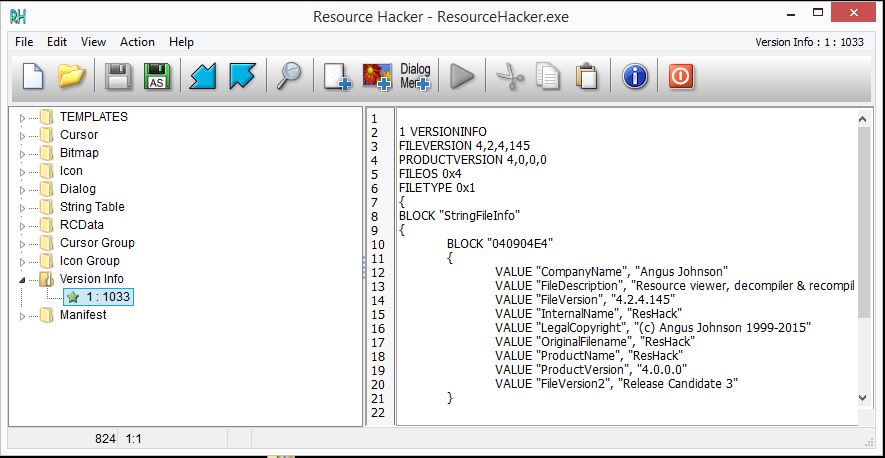
Resource Hacker, or sometimes called ResHackers, is a free application used to extract resources from Windows binaries. Resource Hacker can extract, add and modify most resources like strings, images, menus, dialogs, VersionInfo, Manifest resources etc. The latest version of Resource Hacker, which is version 4.2.4, was release in July 2015.
Resource Hacker can be downloaded using the following link: Resource Hacker
PEview
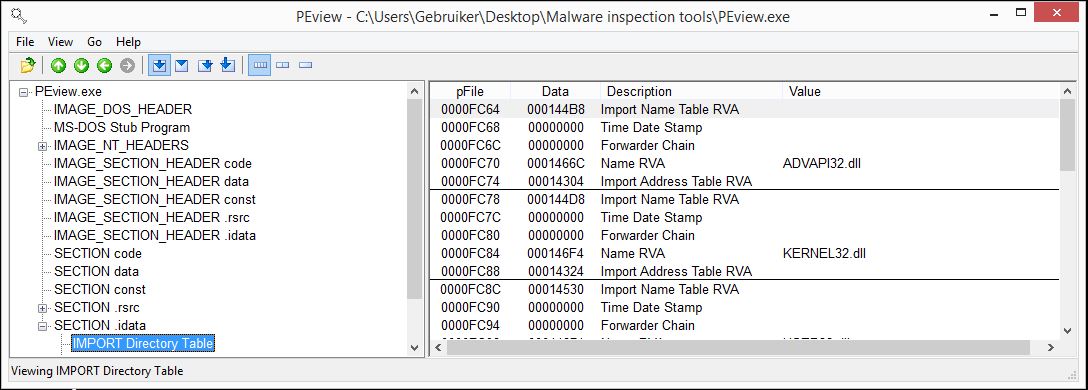
PEview is a free and easy to use application to browse through the information stored in Portable Executable (PE) file headers and the different sections of the file. In the following tutorials we will be learning how to read those headers when we’re examining real malware.
PEview can be downloaded using the following link: PEview.
FileAlyzer
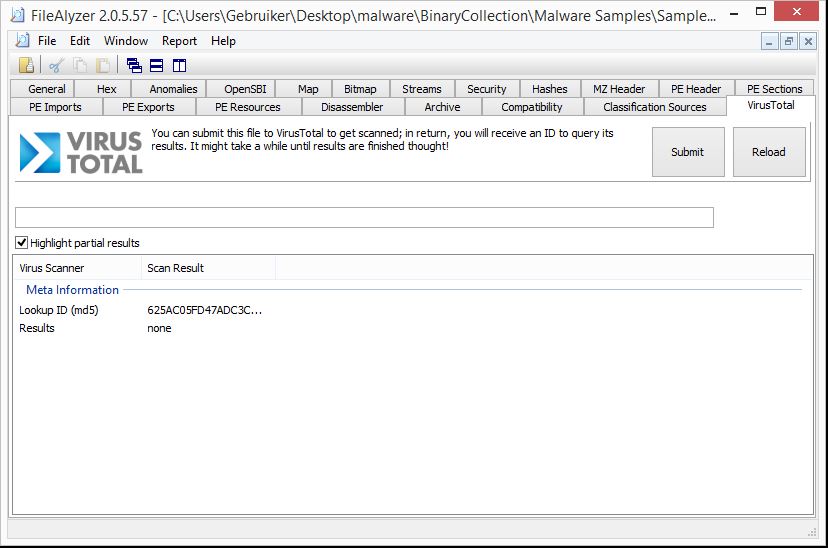
FileAlyzer is also a free tool to read information stored in PE file headers and sections but offers slightly more features and functionality than PEview. Nice features are the VirusTotal tab which can be used to submit malware to VirusTotal for analysis and the functionality to unpack UPX and PECompact packed files. And yes, Filealyzer is a typo but the developer decided to stick with the name which is kinda cool in our opinion.
FileAlyzer can be downloaded using the following link: FileAlyzer.
More Basic Malware Analysis Tools
Needless to say is that we’ve covered only a very small portion of the Basic Malware Analysis Tools available. In the upcoming few days we will be adding more tools for you to download and explore so be sure to subscribe to Hacking Tutorials to stay informed about updates. If you have any questions regarding the tools we encourage you to ask them here. Also let us know when you have suggestions for other tools. You can do so by replying to this post.
Thanks for reading and see you in the next chapter: Dynamic Malware Analysis Tools
If you’re interested in learning more about reverse engineering, malware analysis and exploits, you can follow any of these online courses:
Online Hacking Courses
Penetration Testing Course + Labs

Reverse Engineering and Exploit Development
Application Penetration Testing for Security Professionals. Read more…

Windows Exploit Development Megaprimer
Learn how to write reliable exploits.
Read more…

10 Comments
Awsome
Thank you!
Nice article, looking forward to the tutorials.
Thanks!
hey sir total nice articles,,, can you favor some thing,,,, plz post step by step to Scan some malware…. As i also want to be malware analyst so can you provide some step to step. { please mail me.. luckyrawat29@gmail.com}
Waiting for your rply.
Thanks. wait to next tutorial.
What happend with other 3 tutorials?
We still need to write the last 3 tutorials.
Thank you……….
Great !! still waiting the other three articles !!!