In this tutorial we will be scanning a target for the well known Heartbleed SSL Bug using the popular Nmap tool on Kali Linux. The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library and was introduced on 31 December on 2011 and released in March 2012. This weakness allows the attacker to steal information protected by the SSL/TLS encryption which is very commonly used to secure internet connections. The official name for Heartbleed is CVE-2014-0160. A fix has been released and deployed by many OS and application vendors but when a vulnerable version of OpenSSL is used or when applications haven’t been patched by the user or vendor, the vulnerability can still be exploited. With Nmap’s SSL-Heartbleed script it takes us just a couple seconds to check for this vulnerability and should be part of any penetration test.
Many software applications, web applications and web services have SSL/TLS encryption integrated and have been affected by Heartbleed. These applications include among a lot more: multiple VMware products, Yahoo, Filemaker, Cisco Routers, HP server applications, Sourceforge and Github. Even governments have temporarily shut down online services to defend their applications and networks from attackers, like the Canada Revenue Agency (CRA). Many websites instructed their users to change passwords after a fix had been implemented to reduce the risk of attackers using passwords which were stolen by exploiting the Heartbleed SSL vulnerability.
The Heartbleed SSL bug was discovered by Neel Mehta from Google Security and announced to the public by the OpenSSL project on April 7th 2014. After companies like Yahoo, Google and Microsoft had a chance to fix Heartbleed on their applications. Researchers at AVG’s Virus Labs said they scanned Alexa’s league table of the top 800,000 sites in the world and found 12,043 sites (1.5 per cent) are still vulnerable. Let’s continue this tutorial with some hands on testing and see how we can use Nmap to scan targets for Heartbleed vulnerabilities.
Scanning for Heartbleed with Nmap
Use the following command to scan a target for the Heartbleed SSL bug:
nmap -d –script ssl-heartbleed –script-args vulns.showall -sV [host]
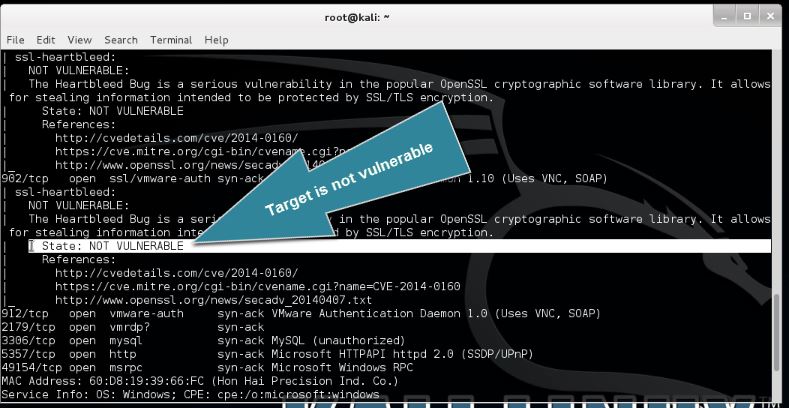
When using the –script-args vulns.showall flag, Nmap will show you also when the target is not vulnerable.
As you can see on the screenshot the target host we have scanned is not vulnerable to Heartbleed. The scanning took only a few seconds and since a lot of applications have been vulnerable to Heartbleed we suggest you to run this script when performing a penetration test or security scan.
Nmap Heartbleed Scanning Video Tutorial
Thanks for watching and please subscribe to my YouTube channel :)
Related Nmap Hacking Tutorials
Open Port Scanning and OS Detection with Nmap in Kali Linux
Scanning a network for live hosts with Nmap
How to enumerate webserver directories with Nmap
Scanning for SMB vulnerabilities using Nmap
Heartbleed SSL bug Scanning using Nmap on Kali Linux

2 Comments
Nice tutorial…
Thanks pal