Tox Ransomware is malware which encrypts your hard drive and demands money in exchange for decryption. After CTB-Locker, Teslacrypt, CryptoWall, Cryptolocker and TorrentLocker, Tox is the new ransomware on the block. Tox is set up as a Ransomware-as-a-service where Tox developers take 20% of the paid ransoms. Tox (or toxicola ransomware) is only accessible over the TOR network and bitcoin is used for pay-outs which keeps users kind of ‘anonymous’. Since it does not require any technical knowledge to set up this ransomware it is expected to be exploited by many users.
Tox Ransomeware is a free ransomware-as-a-service kit, easy to set-up because no technical knowledge is required. Access and virus creation through TOR network, no contact details for registration, pay-outs using bitcoin and Tox takes a 20% cut of the ransom. This is a great formula that will lead us to one thing: Trouble!
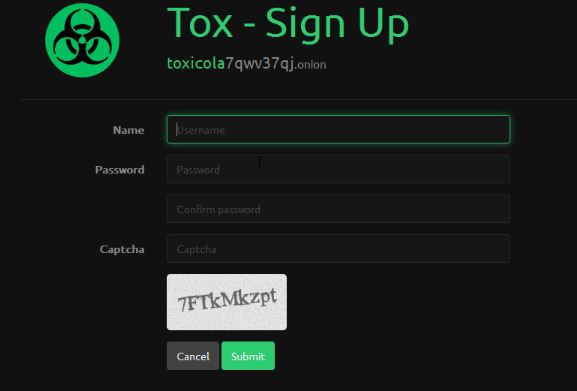
Tox Ransomeware creation
Tox ransomware can be easily created on a TOR union website by signing up with just a name and password.
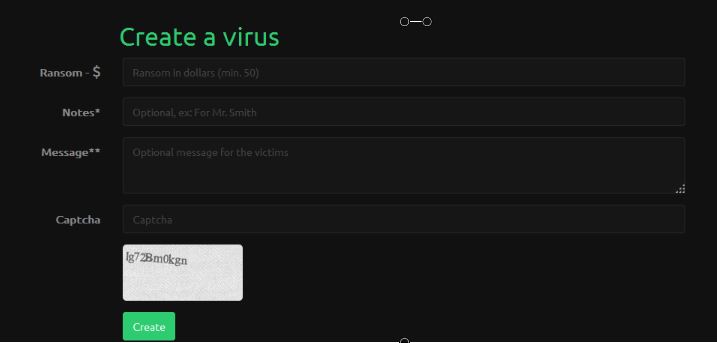
Than completing a form which contains a message, ransom fee and a note.
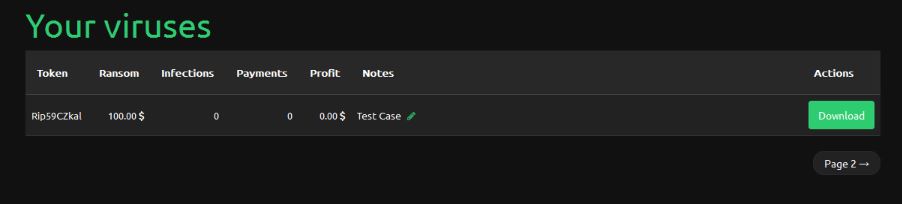
And the final step is to download the Tox Ransomeware virus and it is ready to spread. The output file looks like a regular Microsoft Office Word document and has a .src extension. When the document is opened by the victim the virus will encrypt your hard drive, download and install Curl and TOR. All downloaded files will be stored in the following path: C:\Users\AppData\Roaming\
After execution, Tox Ransomware will start TOR in SOCKS5 proxy mode.
How to protect yourself
- Make regular back-ups of your data.
- Do not open attachments or files from an unknown source.
- Keep your antivirus up-to-date.
- Scan for Malware on a regular basis.
- Browse internet safely.
Tox Ransomware removal
In this tutorial we will be infecting ourselves with Tox ransomware and remove it afterwards using AntiMalwareBytes. Please note that decrypting your files will be very hard and is not covered in this tutorial, just removal of the malware and persistence methods to prevent further damage to your system. Watch below video for a step-by-step tutorial on how to remove Tox Ransomware using MalwareBytes.
Thanks for watching and please subscribe to my YouTube channel for more hacking tutorials :)

5 Comments
why this site is not open in tor ?
The owner was selling the platform. It has probably been taken offline or sold.
Does this work on any OS or just Windows?
This is Windows only.
If this were bundled in a password protected rar, would it still be detected by malware bytes?