MAC address spoofing is a technique for temporarily changing your Media Access Control (MAC) address on a network device. A MAC Address is a unique and hardcoded address programmed into network devices which cannot be changed permanently. The MAC address is in the 2nd OSI layer and should be seen as the physical address of your interface. Macchanger is a tool that is included with any version of Kali Linux including the 2016 rolling edition and can change the MAC address to any desired address until the next reboot. In this tutorial we will be spoofing the MAC address of our wireless adapter with a random MAC address generated by Macchanger on Kali Linux.
MAC Address Spoofing
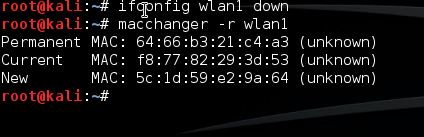
First we need to take down the network adapter in order to change the MAC address. This can be done using the following command:
ifconfig wlan1 down
The ifconfig tool will be replaced by iproute2. Use the following command to take down wlan1 with iproute2:
ip link set wlan1 down
Replace wlan1 with your own network interface.
Now use the following command to change your MAC address to a new random MAC Address:
macchanger -r wlan1
As shown on the screenshot, Macchanger will show you the permanent, current and changed MAC address. The permanent MAC Address will be restored to your network adapter after a reboot or you can reset your network adapters MAC address manually. Use the following command to restore the permanent MAC address to your network adapter manually:
macchanger –permanent wlan1
You can also spoof a particular MAC address using the following command:
macchanger -m [Spoofing MAC Address] wlan1
macchanger -m XX:XX:XX:XX:XX:XX wlan1
If you receive the following error you need to take down the network interface first before changing the MAC Address (Command: ifconfig wlan1 down):
ERROR: Can’t change MAC: interface up or not permission: Cannot assign requested address
Use the following command to bring up your network adapter with the new MAC address:
ifconfig wlan1 up
Or use the following iproute2 command to bring the wlan1 device back up:
ip link set wlan1 up
Use the following command to show the current MAC address:
macchanger –show wlan1
MAC address spoofing Video Tutorial
Thanks for watching and please subscribe to my YouTube channel for more hacking tutorials :)


15 Comments
Good post. Can you explain ‘Network Adapter’ to me? Is this the Bridged option on Kali?
Thanks!
With network adapter I mean the network interface or the physical adapter. You can bridge a network adapter in a VM or connect a dedicated (USB) network adapter and spoof the MAC address. It kind of depends on your configuration.
hi
i need learn hack computer
pleas teach me
Thanks for this tutorial
Hi,
When ever I change the mac address to random or any other than my original one .
I am not able connect to internet. I running on kali linux latest version, On virtualbox(oracle) on a windows 10 pc.9
same issue bro
plz lemme know if its solved :)
thanks.
So what happens when the new mac doesn’t stick? I tried using macchanger to spoof a random mac and it shows me the new mac. But, when I bring the interface back up the original mac is back (sounds like rap lyrics). BTW the interface I’m trying to spoof is my wlan0 on my raspberry pi 2. Any tips would be greatly appreciated:)
Hi Adam
I know it has been a while since your post but did you ever find the solution?
I am having the exact same issue on the same hardware.
Hi, please i need help.
When i spoofed a particular mac address without rebooting my laptop my permanent mac address is restored. Could help me to handle this ?
Don’t need mac changer just use:
Bring the interface down
sudo ifconfig wlan1 ether xx:xx:xx:xx:xx:xx
Bring the interface up
Dear all
Please note that “ifconfig” has been deprecated in latest Debian. From now on you will have to use “ip” command. See example below
ip link set wlan0 down
Thanks for this useful comment! I’ve added this to the tutorial.
I having laptop Serial Number and MAC Address. Please is there any possibility to track my laptops to get back, help me this.
install new
macchanger
runs perfect
Network driver didn’t actually change to the new MAC!!
facing this error plzz help