In this tutorial we’re going to crack the WPA/WPA2 wireless network key using oclHashcat on Windows. Instead of using CPU power to brute force the password we’re going to use the GPU’s, short for Graphics Processing Unit. The benefit of using the GPU instead of the CPU for brute forcing is the huge increase in cracking speed. A GPU is designed to perform repetitive tasks very fast because it has many more cores than a CPU that can be used to process tasks in parallel. Because of the number of cores in a GPU even an older GPU can outperform a modern CPU by using heavy parallelism. The difference between older and newer graphics cards and GPU’s is even larger. The older Radeon 7670M video card in a 2012 laptop does an average of 20kh (20.000 attempts) per second where an AMD HD7970 videocard can do 142kh (142.000 attempts) per second and 8 x NVidea Titan X cards can do 2.233 kh per second. This makes brute forcing routers with easy default passwords, like the TP-LINK (default WPS PIN) or the standard UPC broadband routers (8 capital letters), a piece of cake and just a matter of time. In the first part of the tutorial we created 26 different wordlists which allows us to distribute the wordlist over multiple PC’s with multiple GPU’s. Of course you can and have to question the cost effectiveness of this setup to crack a password because GPU’s don’t come cheap and require massive amounts of power when performing at top speed. Nevertheless it gives us a good understanding of what passwords are strong and what passwords aren’t when using GPU’s to brute force them.
This tutorial starts where part 1 has ended. In part 1 we generated the wordlists using Crunch and we captured the 4 way handshake. If you haven’t followed these tutorials yet I recommend you to check them out first before continuing with oclHashcat:
Part 1: https://youtu.be/1NkK1PGLrQA
Converting .pcap to .hccap: https://youtu.be/1hoGVUAo7xA
oclHashcat downloads
First we need to install some prerequisites such as AMD Catalyst 14.9 (and exactly this version, otherwise oclHashcat won’t work) and download oclHashcat. Windows and Linux versions should work on both 32 and 64 bit.
oclHashcat 1.35 Windows download: https://hashcat.net/wiki/doku.php?id=oclhashcat
AMD Catalyst 14.9: https://www.techpowerup.com/downloads/2405/amd-catalyst-14-9-software-suite-vista-7-8-64-bit/mirrors (or use AMD website)
Update: Together with the release of Hascat 2.0 the developers has decided to make Hashcat and oclHashcat an open source project. The sourcecode is available from GitHub: https://github.com/hashcat/
OclHashcat 2.0 has fixes for the following bugs:
- –increment-max problem: it did not allow to set a value equal to the mask length
- table lookup fix: there was a limit in place which was lifted now
- –remove race condition: hashcat did not always guarantee that all cracked hashes will be removed at the end
The developers also added a new algorithm:
- -m 1431 = base64(sha256(unicode($pass)))
Cracking WPA with oclHashcat
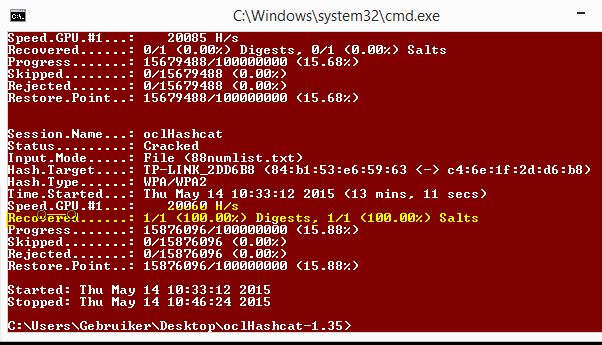
Now that we’ve created the password list and captured the WPA handshake we need to store both files in the oclHashcat folder. Next right click the oclHashcat folder and select “Open Command Prompt Here” to open a command line session.
Use the following command to start oclHashcat:
oclHashcat64 -m 2500 -w 3 –gpu-temp-retain=60 –status -o cracked.txt upc.hccap alist.txt
-m 2500 = WPA/WPA2
-w 3 = Workload profile high latency
-o = Output file path for result file
Note: –gpu-temp-retain is AMD only.
Hashcat Mask Mode
In this tutorial we’ve created a password list with Crunch and have oclHashcat use it to brute force the password. In general this isn’t really effective and slows down the process because we have to wait till Crunch finished generating the wordlist. Reading the passwords from a file will also slow down cracking performance in oclHashcat. Instead of using a password list file we can also use Hashcat mask mode as following:
oclHashcat64 -m 2500 -w 3 –gpu-temp-retain=60 –status -o cracked.txt upc.hccap -a 3 ?d?d?d?d?d?d?d
When oclHashcat finished the cracking process it will store the results in a file named: cracked.txt. This file is located in the oclHashcat folder.
Lesson learned
Now that fast GPU’s are available for decent prices and become the standard in consumer laptops and desktops, the average home user has the power to crack passwords which were considered strong and safe by many end users. A password containing 8 numbers can be cracked with great ease in a very reasonable time frame, just a couple hours with a speed of 20kh/sec. When you’re the proud owner of a TP Link router and didn’t change the default password, it is recommended to change the password as soon as possible. Consider using a password of at least 10 characters containing lower- and uppercase letters, digits and special signs.
If you’re interested in learning more about WiFi hacking and wireless in general, you can follow any of these online courses:
Online Hacking Courses
Penetration Testing Course with Labs

Learn Wi-fi Hacking/Penetration Testing From Scratch
This course contains 50 Videos to learn practical attacks to test the security of Wi-fi and wired networks from scratch using Linux. Read more…
ARP spoofing & Man In The Middle Attacks Execution & Detection
Learn practical attacks to test the security of clients connected to a network and how to protect against these attacks. Read more…



8 Comments
Thanks, I appreciate it!
Hi, thanks for taking the time to write this.
With this method, need any special wireless network card or will my regular intel card work ?
Hi, You’re very welcome!
For this tutorial you won’t need a network card at all. You only need a good GPU for cracking. You do need a compatible network card for capturing the 4-way handshake.
Hi! Very useful tutorial, thank you!
What about your promise:
*** In a couple days I will add a custom made Windows tool to provide the user with an easy GUI for WPA cracking with oclHashcat. Please subscribe to my channel to stay informed :-) ***
:-)
Thank you for your reply!
When I have time, i’ll upload the promised tool and make it available for download :)
i waiting for your tool sir…
is not working
Lets us know what is not working and which errors occur, maybe we can help you.